Session Layer Protocols
1) MQTT
MQTT stands for Message Queue Telemetry Transport. It was introduced by IBM in 1999 and standardized by OASIS in 2013. It is used for remote monitoring in IoT. Its main challenge is to collect statistics of many devices and the delivery of its infrastructure. MQTT connects devices and networks with packages and middle-ware. MQTT protocols work over TCP to provide reliable and straightforward information flows.
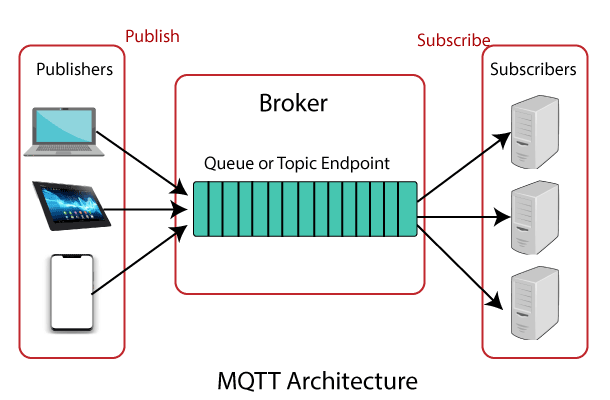
It follows the publish-subscribe architecture. The architecture has three main components: publisher, subscriber, and a broker.
The publisher collects the information and transmits the facts to subscribers through a broker. The broker guarantees security by controlling the movement of permission from publishers and subscribers.
2) Secure MQTT (SMQTT)
SMQTT is the extended form of MQTT. SMQTT stands for Secure MQTT. It uses encryption based on lightweight attribute-based encryption. The main advantage of attribute-based encryption is, it uses the broadcast encryption function. In this function, the message is encrypted and transmitted to several nodes that are quite common in IoT applications.
In general, the algorithm consists of four steps: configuration, encryption, publishing, and decryption.
In the configuration phase, subscribers and publishers register with the broker and obtain a master secret key based on the key generation algorithm chosen by the developer. In SMQTT, key generation and encryption algorithms are not standardized.
3) AMQP
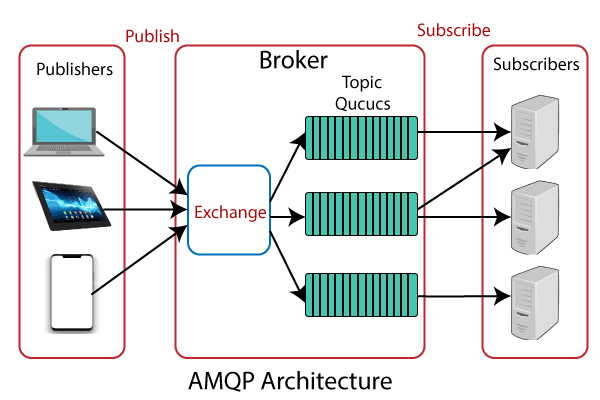
Advanced Message Queuing Protocol (AMQP) is another session-layer protocol designed for the financial industry. It runs on TCP and provides a publishing/subscription architecture similar to that of MQTT. The difference is that the broker is broken into two main components: exchange and queues. The exchange component receives the publisher’s messages and distributes that massages in queues according to predefined roles and conditions.
4) Constrained Application Protocol (CoAP)
CoAP is an Internet utility protocol for restricted devices. It is designed to allow single and small devices to join the IoT through low bandwidth restricted networks. This protocol is mainly used for Machine-to-Machine (M2M) communication and is specially designed for IoT systems based on HTTP protocols.
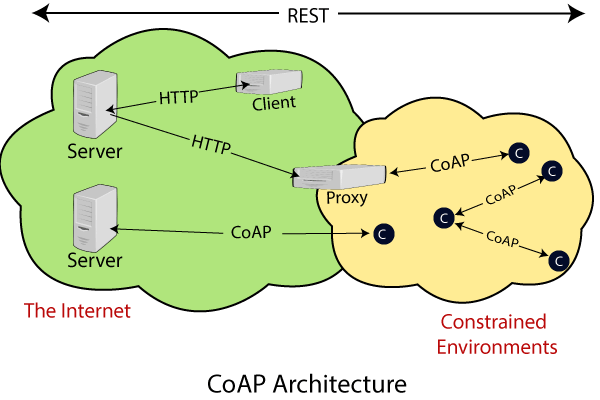
CoAP uses the UDP protocol for a lightweight implementation. It also uses a silent architecture, which is similar to the HTTP protocol. Use DTLS (Datagram Transport Layer Security) for changing statistics in the slippery layer.