What is Phishing Attack?
What is Phishing Attack?
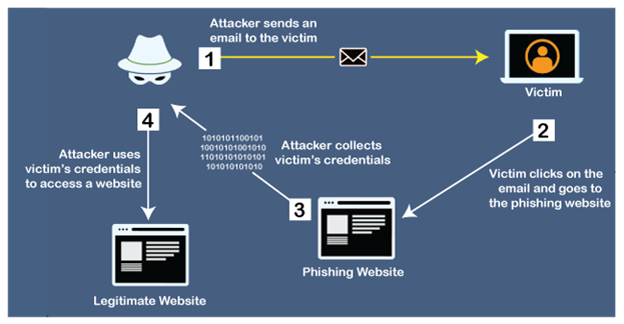
Phishing is a type of social engineering attack used to obtain or steal data, such as usernames, passwords and credit card details. It occurs when an attacker is disguising oneself as a trusted entity in an electronic communication.
Phishing cyber-attack uses disguised email as a weapon. The goal is to trap the email recipient into believing that the message is something they want, a request from their social websites or bank.
The recipient is then tricked into clicking a malicious link, leading to a malware installation, freezing the system as part of a ransomware attack, or revealing sensitive information.
It is one of the oldest types of cyberattacks that back to the 1990s. It is still one of the most harmful attacks, with phishing messages and techniques becoming increasingly sophisticated.
Also, Phishing is used to gain a foothold in corporate networks as a part of a larger attack, such as an advanced persistent threat (APT) event. In this scenario, employees are compromised to bypass security perimeters, distribute malware inside a closed environment, or gain privileged access to secured data.
An organization succumbing to such an attack sustains severe financial losses, declining market share, reputation, and consumer trust. Depending on the scope, a phishing attempt might escalate into a security incident from which a business will have difficulty recovering.
Types of Phishing Attack
Here are some specific types of Phishing that use targeted methods to attack certain organizations.
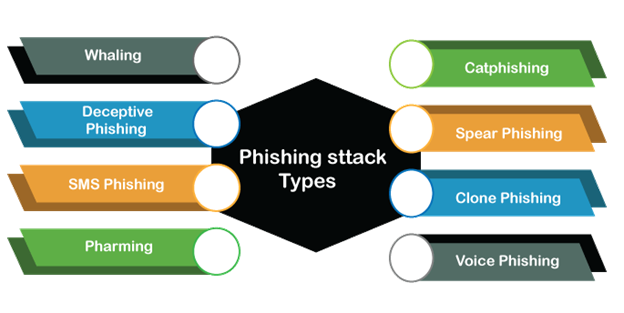
1. Spear Phishing
Phishing attempts by a specific person or company, as opposed to random application users, are known as spear phishing. In contrast to bulk Phishing, spear phishing attackers gather and use personal information about their target to increase their chance of success.
Within organizations, spear phishing targets employees, executives or those who work in financial departments with access to financial data.
Threat Group-4127 (Fancy Bear) used spear phishing tactics to target email accounts linked to Hillary Clinton’s 2016 presidential campaign. They attacked more than 1,800 Google accounts and implemented the accounts-google.com domain to threaten targeted users.
2. Clone Phishing
Clone phishing is a phishing attack whereby a legitimate and previously delivered email containing an attachment or link had its content and recipient address taken and used to create an almost identical or cloned email.
The email's attachment or link is replaced with a malicious version and then sent from an email address spoofed appears to come from the original sender.
It may claim to be a resend of the original or an updated version of the original. This requires either the sender or recipient to have been previously hacked for the malicious third party to obtain the legitimate email.
Auditing firms and accountants are phishing targets. It is usually through email, so text analysis is a common way to analyze phishing emails.
3. Voice Phishing
Not all phishing attacks require a fake website. Messages claimed to be from a bank told users to dial a phone number regarding their bank accounts problems.
Once the phone number was dialed owned by the phisher, and provided by a voice over IP service, then prompts a message to enter their account numbers and PIN. Sometimes Voice phishing or Vishing uses fake caller-ID data to give the appearance that calls come from a trusted organization.
4. SMS Phishing
SMS phishing or smishing uses cell phone text messages to induce people to make known their personal information.
Smishing attacks invite the user to click a link, call a phone number, or contact an email address provided by the attacker via SMS message. The victim is then invited to provide their private data, often, credentials to other websites or services.
Still, due to mobile browsers' nature, URLs may not be fully displayed; this may make it more difficult to identify an illegal login page. As the mobile phone market is saturated with smartphones, which all have fast internet connectivity, a malicious link sent via SMS can yield the same result as sent via email.
5. Deceptive Phishing
Deceptive Phishing is the most common type of Phishing. In this type of Phishing, an attacker attempts to obtain confidential information from the victims.
Attackers use the information to steal money or launch other attacks. For example, a fake email from a bank asking you to click a link and verify your account details.
- Whaling
The term whaling refers to spear-phishing attacks directed specifically at senior executives and other high-profile targets.
The content will be crafted to target an upper manager and the person's role in the company. The content of a whaling attack email may be an executive issue such as a customer complaint.
A whaling attack targets an employee with the ability to authorize payments. The phishing message often appears to be a command from an executive to authorize a large payment to a vendor when the payment would be made to the attackers.
- Pharming
Pharming is a type of phishing attack that uses DNA cache poisoning to redirect users from a valid site to a fake site even if the correct URL is typed. In this case, victims do not even have to click a malicious link to be taken to the fake site.
This is done to trick users into attempting to log in to the fake site with personal credentials.
- Catphishing and catfishing
Catphishing is a type of online deception that involves getting to know someone close to access information.
Catfishing is a similar but distinct concept, involves a person creating a social network presence as a sock puppet or fictional person to finagle someone into a romantic relationship. It usually begins online, with the hope or promise of it progressing to real-life romance. It is never the perpetrator's objective; in general, he is seeking access to the money or receiving gifts or other consideration from the victim.
Phishing Techniques
Phishing attacks depend on more than simply sending an email to victims and hoping that they click on a malicious link or open a malicious attachment. Attackers use several techniques to entrap their victims. Here are some of the most common techniques used in the Phishing attacks, such as:
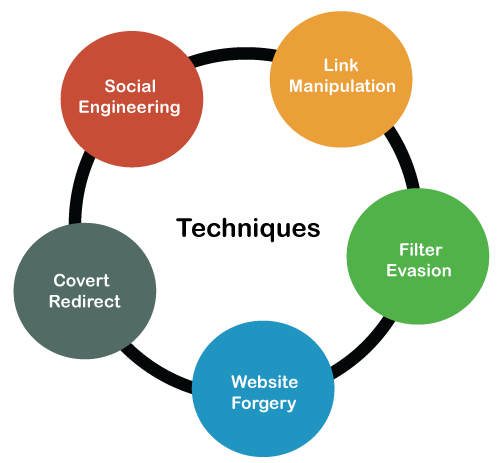
1. Link Manipulation
Link manipulation referred to as URL hiding, is present in many common types of Phishing and is used in different ways. The simplest approach is to create a malicious URL that is displayed as if it were linking to a valid site or webpage but having the actual link point to a malicious web resource.
Internationalized domain names (IDN) can be exploited via IDN spoofing or homograph attacks to create web addresses visually identical to a valid site, that lead instead to malicious version.
2. Filter Evasion
Phishers have sometimes used images instead of text to make it harder for anti-phishing filters to detect the text commonly used in phishing emails. In response, more sophisticated anti-phishing filters can recover hidden text in images using optical character recognition (OCR).
To avoid anti-phishing techniques that scan websites for phishing-related text, phishers sometimes use Adobe Flash. These look much like the real website but hide the text in a multimedia object.
3. Website Forgery
Some phishing scams use JavaScript commands to alter the address bar of the website they lead. It is done either by placing a picture of a legitimate URL over the address bar or closing the original bar and opening up a new one with the legitimate URL.
Also, an attacker can potentially use flaws in a trusted website's scripts against the victim. These types of attacks, known as cross-site scripting (XSS), are particularly problematic because they direct the user to sign in at their service's web page. Everything from the web address to the security certificates appears correct.
In reality, the link to the website is crafted to carry out the attack, making it very difficult to spot without specialist knowledge. Such a flaw was used in 2006 against PayPal.
4. Covert Redirect
Covert redirect is a subtle method to perform phishing attacks that makes links appear valid but redirect a victim to an attacker's website. The flaw is usually masqueraded under a login popup based on an affected site's domain. It can affect OAuth 2.0 and OpenID based on well-known exploit parameters. This often makes use of open redirect and XSS vulnerabilities in the third-party application websites. Users may also be redirected to phishing websites covertly through malicious browser extensions.
Normal phishing attempts can be easy to spot because the malicious page's URL will usually be different from the real site link. For covert redirect, an attacker could use a real website instead by corrupting the site with a malicious login popup dialogue box. This makes covert redirect different from others.
This vulnerability was discovered by Wang Jing, a Mathematics Ph.D. student at the School of Physical and Mathematical Sciences at Nanyang Technological University in Singapore. Covert redirect is a notable security flaw, though it is not a threat to the Internet worth significant attention.
5. Social Engineering
Users can be encouraged to click on various kinds of unexpected content for various technical and social reasons. For example, a malicious attachment might masquerade as a benign linked Google Doc.
Alternatively, users might be outraged by a fake news story, click a link and become infected.
How to Prevent Phishing Attack
Organizations should educate employees to prevent phishing attacks, such as how to recognize suspicious emails, links, and attachments.
Cyber attackers are always refining their techniques, so continued education is imperative. Phishing attack protection requires steps to be taken by both users and enterprises. Some common signs of a phishing email include:
- “Too good to be true” offers
- Unusual sender
- Poor spelling and grammar
- Threats of account shutdown, etc., particularly conveying a sense of urgency
- Links, especially when the destination URL is different than it appears in the email content.
- Unexpected attachments, especially .exe files.
For users, a spoofed message often contains subtle mistakes that expose its true identity. These can include spelling mistakes or changes to domain names, as seen in the earlier URL example. Users should also stop and think about why they’re even receiving such an email.
For enterprises, some steps can be taken to mitigate both Phishing and spear-phishing attacks:
- Two Factor Authentications (2FA): It is the most effective method for countering phishing attacks, as it adds an extra verification layer when logging in to sensitive applications.
2FA relies on users having two things: something they know, such as a password and user name, and something they have, such as their smartphones. Even when employees are compromised, 2FA prevents the use of their compromised credentials since these alone are insufficient to gain entry.
In addition to using 2FA, organizations should enforce strict password management policies. For example, employees should be required to frequently change their passwords and not be allowed to reuse a password for multiple applications.
- Email Filters: Email filters that use machine learning and natural language processing to flag high-risk email messages. DMARC protocol can also prevent email spoofing.
- Augmented password logins: It using personal images, identity cues, security skins, etc.
- Educational campaigns: It can also reduce the threat of phishing attacks by enforcing certain practices, such as not clicking on external email links.
- Technical approaches: A wide range of technical approaches are available to prevent phishing attacks from reaching users or prevent them from successfully capturing sensitive information.
- Filtering out phishing mail: Specialized spam filters can reduce the number of phishing emails that reach their addressees' inboxes. These filters use several techniques, including machine learning and natural language processing approaches, to classify phishing emails and reject emails with forged addresses.
- Email content redaction: Organizations that prioritize security over convenience can require their computers to use an email client that redacts URLs from email messages, making it impossible for the email reader to click on a link or even copy a URL. While this may result in an inconvenience, it does eliminate email phishing attacks.