Introduction to Firewall
What is Firewall?
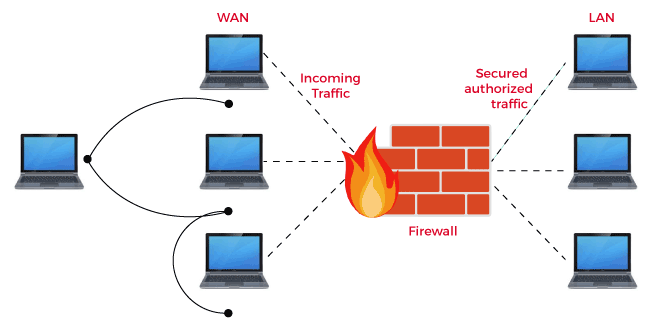
Firewall act as intermediator between external WAN and internal LAN. It checks all the traffic coming from external network against the rules and allow only secured and authorized traffic.
Design principles of Firewall:
- The firewall is immune to penetration.
- The firewall allows only legal traffic defined by the rules and blocks remaining traffic.
- Firewall act as a security agent between inside and outside network and block all malicious code before entering the system.
- The main aim of the firewall is to protect the organizational networks from network attacks.
Characteristics of Firewall:
- All the traffic going from inside to outside or maybe reverse have to pass through Firewall.
- There are different types of the firewall according to different security policies they must implement.
- Alarms and audits can be implemented with Firewall.
- The firewall allows changing network settings anytime when the user wants.
- Intruders trying to attack the network get initially blocked by the firewall. Access is given only if the user allows the permission in the pop-up box.
- The firewall has different protection levels.
- The firewall allows the only valid data packets to enter into a system.
- The firewall allows users to provide configurations and construct rules of their own to be applied for ensuring the security of the system.
- Firewall provides a secure system by blocking malware and other unauthorized access.
- Firewall provides the following security techniques:
10. 1 Service Control: It is mainly used to clarify the type of internet service used, inbound or outbound. The filtration of traffic is done with the help of an IP address or TCP port number. Every service request is filtered in Firewall
10. 2 Direction Control: It is used to show the direction in which service requests will flow and allow to pass through the firewall.
10. 3 User Control: It is used to control access to an application according to which the user is trying to access it.
10. 4 Behaviour Control: It is used to control the mechanism of how services are used. The firewall filters emails and separates spam.
Functions of Firewall:
Based on some rules defined by the network and its resources, the firewall will control all traffic in the system. A firewall is like a security guard for a system that will monitor all the traffic at the entry point and allow only the authorized ones to enter a system. A firewall is a combination of hardware and software components that protect the internal system.
The basic functions of a Firewall are:
- Packet Filtering: All the IP packets entering the system are filtered through the firewall. The main part which is checked is the IP header. The firewall makes the decision and decide whether to allow a packet or not. The set of rules is used by the firewall to decide whether the packet will pass in a system or get blocked. In the OSI reference model, packet filtering works at the network and transport layer. Source and destination IP address with protocols such as TCP, IP, UDP, or ICMP is used with flags in the header part. When the firewall detects any package entering the system it checks the packet against the rule defined. If the rules are satisfied packet gets accepted otherwise it gets dropped. In most of the network packet filtering provide security at the border by filtering the packet before entering the system. It is a little bit hard to configure and difficult to test.
- Stateful Packet Filtering: After the packet filtering, the stateful packet filtering is performed which maintains a record of the state of connection flows. It also keeps the record of IP addresses.
- Application-Level Gateways: The firewall can inspect protocol at an application-level but it requires the firewall to know of it.
- Data Filtering: Firewall protects all the valuable information many firewalls are used in the system for FTP. All the data traveling in a system is controlled by a firewall. The confidential files traveling through the system get protected by the firewall.
- Record User Activity: Whenever you access data from the network you will have to pass through the firewall. The firewall keeps all the records of the information which can be used later in the security system.
Limitations of the Firewall:
- If the user has given the authorized access to someone firewall cannot protect against them. Social Engineering attacks are not controlled by the firewalls. The poorly constructed security policy of firewall leads to exposure to network threats.
- Protection against internal threats is not provided by the firewall such as dishonest employees/ workers working in an organization.
- The Wireless LAN which is not properly secured get attacked by other organization. The firewall cannot protect against such wireless communication.
- Portable Storage devices which are infected connected to a system internally cannot be controlled by a firewall.
A firewall cannot prevent misuse of passwords.