What is DDoS Attack?
Distributed Denial of Service (DDoS) attack is an advanced version of a DoS attack and one of the most dangerous cyber threats. Here distributed tells that the attack sources are distributed among different computers or sources, which means that this attack is not from a single location. Still, it is from multiple locations, and Denial of Service (DoS) means that the service will be unavailable because it is attacked. You will not be able to use those services until it is recovered.
The attackers launch this attack using many compromised computers or networks. In the initial phase, the attacker identifies the vulnerabilities in one or more networks to install malware to gain remote control of the system. After that, the attackers build a network of many compromised computers called a botnet.
The attackers use this technique to make the server or the computer unavailable for legitimate users.
After building the botnet, the attackers generate many requests or packets by using those compromised computers. Then they exploit these compromised computers to send requests to the target servers or computers, which are usually outside the compromised network. It becomes very difficult to detect and defend against such threats as they attack thousands of computers to gain control with specialized malware.
These requests or packets overpower the target system or server, due to which it starts performing poorly and getting down and becoming unavailable for the users. According to how high the attack is, the victim’s computer or the server is damaged. If the attack is much higher than the server or the computer can handle, then the server gets down or crashes in a short time.
What is a Botnet?
A group of or network of many compromised and inter-connected computers acting as an army under the control of an attacker or a group of attackers is known as a botnet. The attacker uses a bot (Software application) that runs automated scripts and generates requests. The attacker totally controls the bot.
What do DDoS Attackers Target?
Generally, the DDoS attackers target any of the following targets:
- Servers or Websites,
- Operating Systems or Applications,
- Firewall or Security System,
- Communication systems or Services.
- Routers, links, etc.
How do Attackers Launch the DDoS Attack?
There are four major steps they follow:
- Selections of vulnerable computers: The attackers first select the larger no. of vulnerable computers to victimize these computers to launch the attack. They only select those computers with enough resources to maximize the attack as much as possible.
- Installing malware and compromising computers: They install specialized malware in all the selected computers and create a network of compromised computers known as a botnet. While planting the code, they take the necessary steps to plant and deactivate those codes after the attack so that it remains undetected.
- Planning the attack: The attackers communicate with each other and the client and plan the attack at the best time. There are some protocols they follow while communicating with each other.
- Attacking the Target: After finalizing all the steps, they launch the attack on the target. They send requests from all the compromised computers more than the target can handle, and depending on the intensity of the attack, the target gets damaged. And if the intensity is much high, the server gets down instantly. The attack's duration can last for a long time, depending on the attacker's perspective and demands. In this attack, the victim has to suffer from any damages and losses in recovering it back.
Types of DDoS Attack
DDoS attacks can be differentiated by which layer of the OSI (Open Systems Interconnection) model is attacked. There are a total of seven layers in the OSI model. Network layer (Layer 3), Transport Layer (Layer 4), Presentation layer (Layer 6), and Application layer (layer 7) are the most common layers attacked by hackers. DDoS attacks are classified into different types depending on which is attacked.
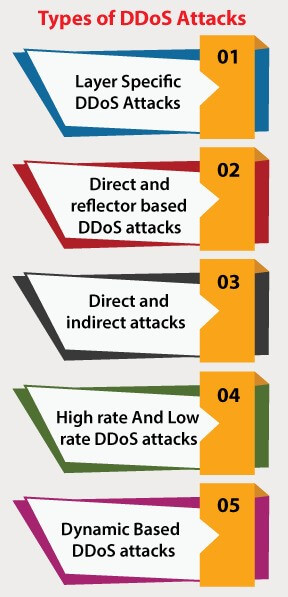
- Layer Specific DDoS Attacks: Depending on which layer of Open Interconnections System (OSI) the attackers use to carry out the attack.
- Application layer DDoS attacks or layer 7 DDoS attacks: In an application layer DDoS attack, hackers use the application layer protocols such as HTTP GET and HTTP POST for sending the stream of requests to the target using a botnet. Such attacks use CPU-intensive queries to make the server busy forever, and it is necessary to find such queries that are taking more CPU time. Downing a server in an application layer attack requires comparatively less traffic or requests than that of other types of attack, i.e., network layers DDoS attack. It becomes difficult to distinguish between normal and attacking requests in an application layer attack.
- Network layer or layer 3 DDoS attacks: The network layer of the OSI model makes the interconnected networks possible, i.e., the internet. The attacker tries to exhaust the resources such as the bandwidth of the links or the memory of the devices such as routers, firewalls, or switches. The attackers use different protocols to achieve this, such as Internet Control Messages Protocol (ICMP), User Datagram Protocol (UDP), and Transmission Control Protocols (TCP). The attackers use these protocols to send a large volume of traffic ranging from hundreds of Mbps to hundreds of Gbps in the network layer of the target.
Common Types of Network Layer DDoS attack
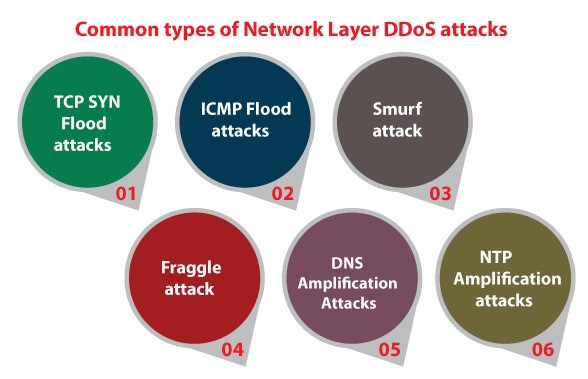
- TCP SYN Flood Attacks: To establish the connection with the server, everyone needs to send the requests to the server, then the server will send the acknowledgment to the sender, and the sender needs to send the acknowledgment back to the server. In the TCP SYN Flood attack, the attackers send the SYN requests (Synchronized requests) to the server. The server responds to each synchronized request with SYN-ACK (Synchronized Acknowledgment) to establish the connection without knowing the attack. The attacker does not send the ACK back to the server, keeps the server busy forever, and is unavailable for legitimate users.
- ICMP Flood attacks: Internet Control Message Protocol (ICMP) is used for detecting and reporting faults and network diagnosis. It detects whether the data is reaching the correct destination and sends the message to the sender from the receiver when data does not come the same way it should. An ICMP flood targets the server or the resource with ICMP Echo requests (Ping) packets by sending all the requests without waiting, and the server will take time to respond and becomes unavailable or busy. This attack uses both incoming and outgoing bandwidths, resulting in a large overwhelm on the target.
- Smurf Attack: In this type of attack, the attacker sends ICMP Echo packets from a fake IP address or the IP address of the target to all the hosts. All the computers connected with the hosts start replying to the source IP address here. The source IP address is not the attacker’s IP address but the victim’s IP address. Suppose the number of devices is large and most of the device replies to the source IP address. In that case, the network traffic slows down the victim’s computer or system, and it becomes unavailable for its legitimate users and causes a denial-of-service attack. It is prevented by blocking the requests from outside of the network but using the Source IP address that belongs to the network, and the hosts can be configured not to respond to ICMP packets or requests and do not forward them to the source IP address.
- Fraggle Attack: The Fraggle attack is also known as UDP flooding, and similar to the Smurf attack, but instead of using ICMP protocol, it uses User Datagram Protocol (UDP), and prevention from Fraggle attack is nearly the same as that of a Smurf attack.
- DNS amplification attack: DNS stands for Domain Name System. In this attack, the attacker amplifies the DNS queries into a larger no. by using multiple DNS servers to attack the target. DNS server resolves the internet domain name into its IP addresses. To launch a DNS amplification attack, the attackers tell to DNS server that the DNS resolver's IP address is the same as the Victim's IP address. As it results, all the DNS replies from the DNS server are sent to the victim's servers, and the attackers find an internet domain registered with many DNS records. During the attack, the attackers send DNS queries that request the entire list of DNS records for that domain. It results in large replies from the DNS servers. Usually so big that they need to be split over several packets.
Now the attacker is ready to launch the attack. Using very few computers, the attackers send a high rate of short DNS queries to the multiple DNS servers asking for the entire list of DNS records for the internet domain it chose earlier. The DNS servers look for the answer and provide it to the DNS resolver. Because the attacker spoofed the IP address of the DNS resolver and set it to be the victim's IP address, all the DNS replies from the DNS servers are sent to the victim.
The victim is bombarded with a high rate of large DNS replies, where each reply is split over several packets. The attacker achieves an amplification effect because, for each short DNS query it sends, the DNS servers reply with a larger response, sometimes up to 300 or 400 times larger. Therefore, if the attacker generates three Mbps of DNS queries, it amplifies to 900 or 1200 Mbps of attack traffic on the victim.
It requires the victim to reassemble the packets, which is a resource-consuming task, and attend to all the attack traffic. Soon enough, the victim's servers become so busy handling the attack traffic that they can't service any other request from legitimate users and the attacker achieves a denial-of-service.
- NTP Amplification DDoS Attack: NTP stands for Network time protocol. It uses to synchronize the time of all the devices present in the network with some reference (true clock) because if the time of two devices is not synchronized, it will become very difficult to manage the faults in the network. After all, both the devices will show another timestamp for a single fault. The attacker uses the vulnerabilities present in the network to attack the NTP server and sends duplicate requests to the NTP server that eventually bombarded the target computer. The attacker uses a network of the compromised computer (Botnet) and spoofs their IP addresses into the Victim's IP address. Then he asks the NTP server to tell the time with thousands of bots (The compromised computers), the server starts replying to all the requests made by those bots. As the hacker has spoofed the IP addresses of bots into the IP address of the Victim's Computer, all the replies or answers are flooded to the victim's computer. It crashes computers or websites and makes them unavailable for its legitimate user. The process of amplifying the requests using Network Time Protocol (NTP) is known as NTP amplification, and the attack is known as NTP amplification attack or NTP amplification DDoS attack.
- Direct and Reflector-based DDoS attacks: The attacker sends thousands of UDP packets (DNS queries) to multiple DNS resolvers in Reflector-based DDoS attacks. Also, the attacker spoofs the IP address into the victim's IP address. As a result, all the UDP queries sent by the DNS resolvers are reflected in the victim's computer or the targeted server. And in a Direct DDoS attack, the attacker uses the botnet and amplifies the UDP queries by asking for more information. DNS and NTP amplification attacks are examples of Direct DDoS attacks, and we have already discussed this in common types of Layer-3 (L3) attacks.
- Direct and Indirect DDoS attack: Based upon the types of attack, we can classify the attack into direct and indirect attacks. In a direct attack, the attacker attacks the victim's computer or the targeted server and sends all the traffic directly using a zombie Network. And in an Indirect attack, the attackers target the services, links, and servers that are essential for the victim to remain functional instead of directly attacking the victim's computer. Crossfire and Coremelt are examples of Indirect attacks. Crossfire DDoS attack is an indirect target area link-flooding Distributed Denial of Service (DDoS) attack determined to affect the neighbors of the real target, and Coremelt DDoS attack is an indirect attack on the link or channel that traverse the target by sending the traffic through the link or the channel.
- High-rate and Low-rate DDoS attack: Based upon the volume and rate of the traffic sent by the attacker, the DDoS attacks are classified into High-rate and Low-rate DDoS attacks. In a Low-rate DDoS attack, the attacker sends the traffic at a low rate that matches the rate of legitimate traffic. And in High-rate DDoS attacks, the attackers send huge volume traffic that exhausts all the resources, and the computer becomes unavailable for its legitimate users.
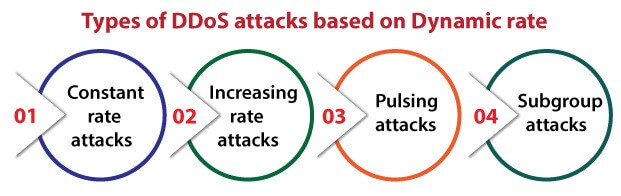
- Types of DDoS attack based on Dynamic rate: In addition, DDoS attacks are classified into different types based on the rate of traffic sent to the victim by the attackers:
- Constant Rate attack: In constant rate DDoS attacks, the attackers command the bots to send the requests at a constant rate to the victim resulting in a sudden flood at the victim’s end.
- Increasing Rate Attacks: In starting, the attackers send the traffic at a low rate instead of sending with full intensity to understand the victim’s responses to those requests so that the attacker can evade the victim’s defense mechanism and increases the rate of the traffic as per needed to make the victim’s computer unavailable.
- Pulsing attack: In this type of attack, the attackers activate a group of bots and command them to periodically send traffic to the victim to remain undetected from the victim's defense mechanism. In a Shew attack, the attackers target the Transmission Control Protocol (TCP) by sending the traffic periodically on the same link to disrupt the TCP connections by exploiting a weakness in the TCP retransmission mechanism. Shrew attack is an example of a Pulsing attack.
- Subgroup attack: In a Subgroup attack or small subgroup attack, just like in a Pulsing attack, the attackers create some groups of bots and activate and deactivate to send a burst of traffic to the victim to remain undetected from the victim's defense mechanism. The groups of the bots are activated and deactivated by different combinations and controlled by the attackers. The attackers use this technique to attack for a long time without detecting the defense mechanism.
With a rapid increase in cyber threats, especially in DDoS attacks, we need a strong defense mechanism to nullify or minimize the effects of DDoS threats. Based on the nature of the defense mechanisms or systems, we can classify them into different categories. Let’s learn about some common types of DDoS defense systems:
DDoS Defense Systems based on the approach
- DDoS Detection: This type of defense system detects all malicious activities, unusual traffics, or network policy violations. The DDoS detection application detects all malicious activities either at the network or the host level. If the application detects such activities, it reports and alerts the defense administration.
- DDoS Prevention: DDoS prevention system is an upgraded version of the DDoS detection system because it detects and prevents all malicious activities or unusual traffic that can damage the system at the network or host levels. It blocks all the malicious activities that are detected. It is commanded or programmed such as it can send alerts to the defense administration, drop malicious packets, reset the connection or block the malicious traffic that is offending the system.
- DDoS Response: The work of the DDoS response system includes monitoring the system and taking action based on the alert generated by a DDoS detection System. An alert generated contains necessary and important information such as source IP address, attack time, and the attacker's account details. The DDoS response automatically executes an appropriate set of instructions based on the type of attack. It takes necessary actions to minimize the detected threats and helps the system return to its normal working form.
- DDoS Tolerance: DDoS Tolerance system is designed to defend the system resources against DDoS attacks so that the system remains functional at a reduced and reasonable level instead of preventing all the intrusions.
- Based on Nature of Control
Based on the nature of control of the system, we can classify the defense system into three forms Centralized, Hierarchical, and Distributed Defense System. Let’s start with the Centralized Defense System:
- Centralized DDoS System: In this type of Defense system, a central server plays the role of correlation handler among all the computers present in the network and solves all the problems happening in the network. All the alerts generated at the individual level are sent to the central server, and the central server takes necessary and accurate actions based on all the available alert information. The main drawback of this type of defense system is that any failure at the central server could collapse the whole correlation process because of the single-point defense system. And the central server should be able to manage a large amount of data generated by the alerts in less amount of time.
- Hierarchical DDoS System: The actions are performed hierarchically in this type of defense system. The alerts generated at the lowest layer are sent to the higher level and then to the highest level with all the information for analysis and furnishing. All the middle layers perform the role of correlation handler. It generated the correlated alerts and sent them to the highest level for further analysis. This type of defense system is more reliable than the Centralized DDoS system but still suffers from the vulnerabilities at the central level.
- Distributed Defense System: In Distributed defense System, all the detection and prevention entities are distributed in the network. There is no centralized unit like in the Centralized and Hierarchical defense system. They all have their components to communicate with each other. All the entities are not aware of the system's topology and are free from the role of correlation handler, making it easy for the scalable design of this type of defense system or network. The alerts generated in this system are quite easy to handle. Still, the main disadvantages of this type of defense system are the accuracy is low as the information of all alerts is not available at the time of decision making, and the alert information contains only the source IP address, which makes it unable to detect large-scale attacks.
Based on the Defense Infrastructure
All the defense systems are developed based on the infrastructure used. We can classify the defense system in two different categories based on the infrastructure used: host-based and network-based defense systems. Let’s jump into it and learn about both types of the defense system:
- Host-based DDoS Defense: In this type of defense system, the computers in the network performing the role of the host analyze the data generated individually. The host-based DDoS detection and prevention system monitors all the resources and systems accessing the resources. It raises a flag when an anonymous system uses the data that violates the protocols of using the resource is detected. Its main purpose is to make the network secure and meaningful and ensure that everything is going perfectly. It plays a crucial role in filtering the network or systems, removing the computers violating the rules.
- Network-based DDoS Defense: The Network-based DDoS detection and prevention system monitors the data exchanges between the computers. It captures the network traffic flowing through the wire in real-time and on a scheduled basis. It maintains the CPU utilization and network overhead and provides a flexible means of secured administration. Certain sensors and computers are designed to monitor network traffic, and they analyze the wire for a particular signature or abnormal behavior. In addition, they generate necessary and appropriate responses. If any suspicious or abnormal behavior is detected, an alarm is sent to the central computer or an administration.
Based on Defense Location
Based on the location of the defense system, we can classify them into three categories: Victim-end, intermediate, and Source-end Defense systems. They all have their advantages and disadvantages.
- Victim-End DDoS Defense: The DDoS defense systems are employed at the victim end means in the network's routers that may potentially become the victims of the DDoS attacks. The detection system detects the attacks that match the reference (information stored) and sends alarms to the central computer. The detection software stores all the necessary data like profiles of normal behaviors, intrusions signatures, and false alarms and updates. The information is updated timely based on the available knowledge. The main disadvantage of this type of defense system is it detects the attack after the attack reaches the victim.
- Source End DDoS Defense: The Source End DDoS Defense system prevents congestion in the whole network. The major issue of this type of defense system is implementation because all the attacking sources are widely distributed in the network, and it becomes very difficult to find such sources acting as the normal traffic and deploying the system at the source end without prescient knowledge of where an attack may generate from in the big networks. And if there is a bad network, why would it allow outsiders to implement their defense mechanism?
- Intermediate Network DDoS Defense: The intermediate network defense system balances detection accuracy and attack bandwidths which are the major issues in the previous approaches. After comparing them with the stored normal profiles applies the rate limits on the connections passing through the routers. This scheme needs to be implemented at all the routers present on the internet because the unavailability of this scheme in a few routers could lead to major issues or failures. Its main disadvantage is its deployment because it requires re-configuration from all the routers present on the internet.
Based on the technique used
There are many techniques used to deploy the DDoS defense system, and we can categorize them into misuse detection and anomaly detection:
- Misuse Detection: The Misuse Detection defense system detects only the known attacks based on the predefined characteristics (abnormal and normal behaviors). As it only detects the known types of attacks, if and novel attack takes place using an unexpected pattern of traffic, then it will be missed. Hence the accuracy of these types of intrusion detection systems (IDSs) decreases and depends on how the knowledge of the attacks are captured, pre-processed, and fed to the IDSs.
- Anomaly Detection: In this type of defense system, we first establish the normal behavior of the system or user, and the behavior of any action that does not match with the normal behavior is treated as an intrusion. As we can establish the normal behavior of a system or user, we can detect all the systems with behavior that vary significantly from the normal profiles. The main advantage of an anomaly detection system is it can also detect unknown attacks, whereas the misuse detection system tries to detect only known attacks or known bad behaviors.
Methods to Stop and Prevent DDoS Attacks
As we have learned, DDoS attacks are one of the most dangerous and real cyber threats. We always need a strong defense mechanism to tackle it. You can use certain methods to stop and prevent DDoS attacks.
- Response Plan: A good plan is the key to success. It is one of the most important points you always need to remember. To stop and prevent DDoS attacks, create a quick response team with predefined agendas which include: clear step-by-step guidelines, all information of necessary tools, essential protocols, responsibilities of each member, and many more details should be there to manage a complete defense system. Your defense team always needs to be ready to tackle and respond promptly and fast so that the system should face less damage. As a result, it will recover quickly and become available for its legitimate users.
- Defense System and Tools: A good and strong defense system will always keep your business and system safe. You must have proper protection tools installed for both your network and applications. Protection tools include software, firewall, anti-virus, specialized DDoS defense system, anti-malware, and monitoring software. These defense tools and systems will monitor the network traffic and generate alerts for suspicious and malicious traffic.
- Multiple Servers: The main objectives of a DDoS attacker are to make your server or system down. You should have distributed server over the whole network instead of a single and central server. Because of distributed servers in the network, if an attacker launches a successful attack on a server, the other server will remain unaffected by the attack. The system will remain functional for its legitimate users. Using a content delivery network (CDN) will help share the load equally across all the distributed servers in the network, and the targeted server will face less traffic.
- Updated Defense System: As we know, prevention is better than cure. Detecting and defending a DDoS attack with vulnerable defense systems could lead to large damage and huge company losses. With a strong defense system, the effects of the attack could be nullified and minimized. So always keep your all defense tools and system up-to-date and fix all the bugs and issues of your system.
- Learn from Mistakes: If an attacker has already launched a successful DDoS attack and you have recovered from it. So, you must be well aware that a DDoS attack can prove to be very dangerous. Do not use the same defense system. You must update your entire defense system or, if possible, change it because attackers can attack you again using old shortcomings like last time.
- Aware of Warnings: It becomes necessary to detect a DDoS attack sign. Your defense team needs to monitor the network from time to time and take quick and appropriate actions against all the suspicious behaviors like poor connectivity, slow performance, multiple requests from a single location, or unknown locations in the network. A DDoS attacker can use less intensity of traffic to attack for less period, so the team should detect those low volume traffics to prevent the attack.
- Define Rules for a Normal User: When you define the normal behavior of traffic and set rules for users to use the services, then the network's abnormal behaviors can be easily detected and easily blocked from using the network or system. This method is very helpful to prevent DDoS attacks before it does too much damage.
- Keep Monitoring the Network: Do not leave your network in a free state or for a long time without monitoring. DDoS threats are minimized by monitoring the network from time to time, and real-time monitoring ensures that you detect attacks before it takes their full swing. Attackers can take advantage of it and attack your network at the right time when the defense team is not monitoring the network.
- Take everything seriously: Once an attacker finds a way to attack the network, he can use it later to attack with a large intensity of traffic and damage the network for a long time. As we have already discussed in different types of DDoS attacks, the attackers can use the traffic of less intensity to attack the network. Neglecting such a DDoS sign could lead to a big problem for you or even worse. Annually, the no of DDoS attacks increases. Every business faces a DDoS at some point, so it becomes necessary to prepare to defend the DDoS attacks in advance to protect the company from threats and minimize losses.