Difference between Network Security and Cyber Security
Introduction
While learning about cyber security, usually terms like information security and network security come to have a familiar ring. Still, they are different from each other on numerous factors.
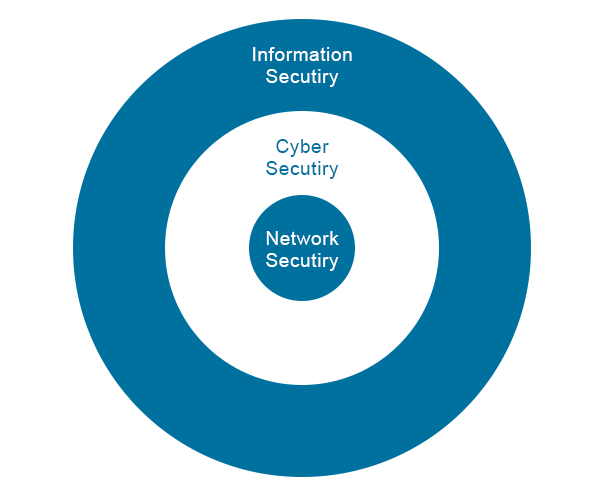
The technology world revolves around these terms, but cyber security & network security are a subset of information security that deals with protecting the data, internet, or internet-connected system, including software, hardware, data, and programs, from potential cyber-attacks.
Cyber security – Cyber security is concerned with the security of all aspects of cyberspace, including devices, the integrity of the networks, and various programs & prevent them from damage, attack, or unauthorized outside access, i.e., against external hostile cyber-attacks.
It collects technologies, techniques, and processes designed to protect networks and systems from potential cyber-attacks. Cyber security is handled by cyber security professionals who monitor all the outgoing and incoming communication or data traffic to reduce the risk of cyber-attacks to protect the organization from unauthorized exploitation of systems.
Network security – Network security is a type of security designed to protect the network-accessible resources and organization’s IT infrastructure from all kinds of cyber threats and attacks like Trojan, viruses, spamware, spyware, malware, etc. network security includes firewalls, ID & passwords, backup, internet access, and encryption.
Network security is handled by security professionals who make the network security with their technical expertise, including support with encryption, intrusion detection system, firewall, and digital certificates.
| Network security | Cyber security |
| Network security protects the flow or travel of data through and across an organization's network. It includes protecting files and directories from being hacked, misused, and unauthorized access to the system. | This security system is an extra layer of defense that protects a company's device and server data against cyber criminals, i.e., it protects the network and inter-connected systems from digital attacks. |
| Network security comes under the cyber security | It comes under information security |
| It provides end-to-end protection to the network of the system | It provides end-to-end protection to everything in cyberspace |
| It protects the data flowing over the network | It protects entire digital data in the devices and servers |
| Types of network security tools are: -- Access control - Antivirus and anti-malware - solutions - Data loss prevention (DLP) - Email security - Firewalls - Mobile security - Network segmentation - Web security - Endpoint security -Virtual private network (VPN) | Types of cyber security are: - Critical infrastructure security - Cloud Security - Network securityInternet of Things (IoT) security - Application security |
| Kinds of a network job offer under this are network security engineer and network security architect | Kinds of job titles it offers are cyber security analyst and cyber security architect |
| It protects the network from viruses, malware, Trojans, and worms | It defends the organization or its data from cyber-crimes and cyber-attacks like pretexting and phishing |
| Network security professionals protect organizations IT infrastructure, including securing financial information, information assets, and other confidential information | Cyber security professional provides cyber security detection, protection, and recovery, and they manage all this by collaborating with different departments in the organizations (coordinating risk management tools and technologies) |
| Method of keeping the network safe and protected: - Setting up a strong password - Password policies - Establishing a firewall - Antivirus protection - Updating softwares - On-time backups - Secure configurations - Smart surfing on websites - Removable media control | It includes these preventive measures: - Securing sensitive data - Up-to-date information - Website authentication - Using a password management tool - Two-factor or multifactor authentication - Knowledge of phishing scams - Protection of sensitive personally identifiable information (PII) - Use of mobile devices securely - Backup of data regularly - Not to use public Wi-Fi, device over a public network - Regular review of bank account and credit and debit card transactions |
Conclusion
The terms network security and cyber security are used in conjunction. One term defines the protection of data, and the other is related to securing the transferring of data in or out of an organization.
Both terms are important and necessary to implement for a successful business. Still, cyber security is a much broader term than network security because network security is just a part of the information/ cyber security.