Types of social engineering attacks
A trap made by hackers by using deceptive psychological manipulation methods (taking advantage of human behavior variations like fear, excitement, or urgency). Social engineering is one kind that covers the massive portion of all cyber-attacks as these are the act of human hacking for committing fraud and identity theft. Just a single error made by humans can be responsible for it being a victim of social engineering attacks. Social engineering attacks are disguised but straightforward, where hackers convince victims of under-informed, stressed, or trusting conditions to do what they say. They take advantage of the heightened emotional state of humans.
These attacks are easy to pull off and worth it as they follow a process cycle to gain the user's trust. Social engineering attacks usually have an attack cycle that is followed by both:-
- Hackers follow this cycle of attacking.
- A well-managed service provider use this cycle to train its team on how to prevent cyber security attacks and risk
Software engineering attack cycle
This cycle has 4 simple steps followed by them:
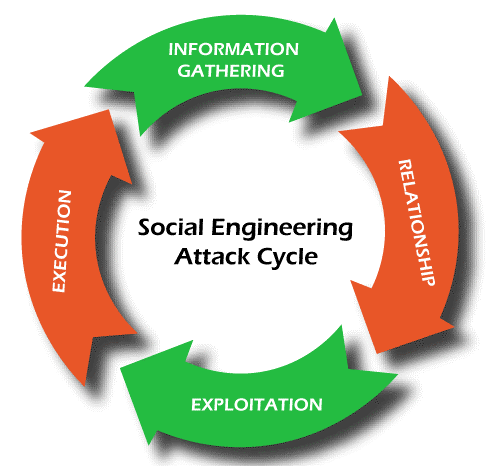
- Information gathering
It is the most time-consuming cycle step as this cyber-criminal gathers all the necessary information. The attacker's success rate depends on this phase as they spend lots of time and resources collecting the information to make further steps easier. The better the information, the better the attack will be. For collecting the information, attackers try to be "friends" to the victim on social media (by scrutinizing your posted photos and finding details that prove reliable information to them). Attackers also use phishing techniques to gather information. - Establishing report and relationship
After gathering detailed target information, attackers tried to connect you and build a working relationship with the target via email, social media, text, or another method. Initially, they act like innocent senders, but they act more dangerous. Hackers can be more familiar with you by sharing stories, family pictures, and even on the phone. In short, with the help of social media, they try to build a trustworthy and undoubted relation to the target. - Exploitation
After making relationships and adapting your trust, it's time to hook you. They try to make you comfortable in sharing your email and password. They trap you by sending a fake link that looks like a legitimate link (something you have an interest in). This step is a great training opportunity and requires some action that makes a big difference. Successful exfoliation happens when the target:- Open an infected mail attachment.
- Share username and password over the phone.
- Please open the door for hackers and let them spoil inside facilities
- Insert malicious pen drive to a company computer
- Sit in the group or “peer” for discussion and reveal all the trade secrets
- Execution
Here the trap has executed that hack you without knowing you as you remain in a dilemma that you have done something good for someone else. Damage makes you realize that you have been scammed. Until then, the criminal cleared his footprint and left no traces behind. Finally, attacker achieves their ultimate goal by attacking and keeping their identity hidden.
Different types of social engineering attacks are:-
- Phishing
Phishing is one of the common cyber-attack that comes under the social engineering attack category that takes place via emails. In this, employees are sent an email that seems legitimate to obtain log-in information and other details that can be used against the company in attacking. These attacks gather the target's personal information (name, address, and social security numbers) or credit card details.
They manipulate the target to make mistakes.
Attacks also send shortened or misleading links to the target, leading them to suspicious websites that host phishing landing pages and creating a virtual fear and a sense of urgency so that users respond quickly. Some of the phishing types are:- In spear phishing, attackers target specific individuals and enterprises, which are much harder to detect and have a success rate.
- Spam phishing or mass phishing targets the mass to catch any unsuspected person because these are non-personalized attacks.
- Angler phishing the attack using spoofed customer service accounts on social media.
Methods used for phishing attacks are:-
- Voice phishing (vishing)
- Email phishing
- Search engine phishing
- URL phishing
- In-session phishing
- SMS phishing (smishing)
- Watering hole attack
In a watering-hole attack, attackers indirectly attack the group through a website. They compromise a website that a particular group of people visits. They try to fetch the data of the employees (employees' credentials or log-in details) who use the website. It also makes individuals and their device to be compromised.
- BEC- Business email compromise attack
In a business, an attacker masquerades as a C-level executive and tricks the target into performing their business function via email. It’s a kind of email fraud for an illegitimate purpose (for money). They also call the target/ individual and impersonate the executive.
- Physical social engineering
With the internal/software protection of data in cyber security, one must focus on protecting the physical aspects of data and assets. Physical and social engineering attack targets some people in the organization, like receptionists, help desk staff, and frequent visitors for the company's data. They can be proved as the weak joint of the company; therefore, their organization must have effective physical controls like maintaining visitor logs, background checks, and escort requirements. Special training is provided to the employees in positions at higher risk for physical and social engineering attacks to benefit the organization.
- USB baiting
In this type of social engineering attack, targets are scammed to provide sensitive information in return for providing some valuable. Attackers offer tempting offers in front of the victim to lure them into the social engineering attack. For example, a scammer offers a free music download or a gift card to trap the victim for providing credentials. At a conference, an attacker may hand out free USB drivers to the users. In this scheme, users are provided a free storage device, but they don't know that attacker loaded it with remote access malware which can infect the system after plugged in. Simply victim's curiosity is exploited via the use of physical media.
- Pretexting
In this social engineering attack, attackers create a pretext or a fabricated scenario for the victim to steal their personal information. An attacker impersonates itself as a trusted individual or entity needing certain details from users to confirm their identity. The attacker commits identity theft after the victim does compliance and uses the data to conduct other malicious activity. Hackers trick victims into doing such things that circumvent an organization's security policies by building a false sense of trust with them. To make them trustworthy, attackers create a credible story that leaves little doubt for them in the mind of their target. For example, attacker contact is an external IT services auditor for the company so that they (the organization's physical security team) allow them into the building. For this scam, attackers choose a suitable disguise not to be revealed easily.
- Tailgating
“tailgating" means being someone's tail. In this type of social engineering attack, an unauthenticated person follows an authenticated employee into a restricted area. To start this following process, the attacker impersonates a delivery driver and waits outside the building to start the things. After gaining the security approval, the employee opens the doors, and the attacker asks him to hold the door to gain access to the building.
Tailgating is not implemented everywhere. I can't work in the presence of security measures like a keycard system. Organizations without these security measures allow attackers to strike up a conversation with employees and use this familiarity show off to get past the front desk.
- Scareware
Victims of this social engineering attack are bombarded with fictitious threats and false alarms. This user is tricked that his system is infected with malware and receives fake pop-ups and notifications to install software that is malware itself and has no real benefit for the user (but beneficial for the perpetrator). Scareware, also known as fraud, deception software, and rouge scanner, is responsible for legitimate pop-up banners appearing in the user's browser during net/ web showing text like " this system is infected with a harmful spyware program." This can take you directly to a malicious site that can infect your computer and offer to install the infected tool on the system. This show bogus warning via spam email and deceives user into buying worthless/ harmful services.
- Honey trap
This attack is also known as a romance scam where the victim is caught in the romance trap. Scammers create fake social media and online dating profiles using fake information and attractive stolen photos. Once they target their victim, they start liking their photos, sending them flirty and provocative messages to trap the victim in their fake love. After some time, they make the victim prove their love by sending gifts, cryptocurrency, or cash. These attacks are most common on social sites like Snapchat etc. the method to avoid them is to stay safe and are aware of the dangers of online dating.
- Quid Pro Quo
The federal trade commission (FTC) detects cases where an attacker designs fake SSA websites to steal people's personal information. This social engineering attack is like a baiting attack where it offers something in exchange for information. This attack happens when an attacker/ fraudster impersonates the U.S Social Security Administration, which personally contacts random people to collect their social security number by stealing the victim's identity. This attack is sophisticated as in some attacks; workers had revealed their passwords for small goods like a bar of chocolate or a pen.