Tunneling Techniques in Cyber Security
What is Tunneling?
Cyber tunneling is a method used in passing sensitive information between two separate networks that are not necessarily trusted or secure. Tunneling involves carrying a packet from a certain protocol as a payload through another protocol, thus forming a tunnel to traverse the data. Tunneling serves mainly to protect data during its travels through networks, particularly across the web.

Tunneling represents the process wherein data is packaged for carriage in the payload of some other protocol. The outer protocol acts as a wrapper of sorts around the private data within, guarding against external hazards and undesired intrusion. Data inside a packet, often termed payload, remains concealed from the outer network while only information necessary for route and packet passage is observable.
Tunneling is used in VPNs, one of its widespread applications – for setting up encrypted channels over an unprotected online environment. These secure pathways are created by employing different tunneling protocols such as Point-to-Point Tunneling Protocol (PPTP), Layer Two Tunneling Protocol (L2TP), and Secure Shell (SSL).
The Significance of Tunneling in Network Communication
Enhanced Security
One crucial way that helps make network communication more secure is tunneling. It secures a route by enclosing data in an outer protocol, thereby keeping outsiders away from interception or alteration of information. This is particularly important in the case of sending confidential details across open or questionable channels.
Cross-Network Compatibility
Many networks deploy various infrastructures and protocols. Tunneling allows inter-networking with diverse architectures by maintaining consistent transmission of information across the web. This is important when networks are heterogeneous, e.g., how to make branch offices talk and enable remote access.
Privacy and Confidentiality
Tunneling is one of the main goals, among others, in which the privacy and security of data are warranted. Encapsulating and protecting the actual payload with data packets is an effective way to ward off any malicious interference that might uncover classified information and expose weaknesses in a network.
Versatility in Protocols
In addition, tunneling supports different protocols; hence, it is convenient to select an appropriate method for a particular case. This versatile nature means that tunneling can be effectively implemented in a wide range of communication networks, including Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), and Secure Shell (SSH) tunnels, among many others.
Secure Remote Access
The concept of tunneling is integral for the basis of securing remote access, particularly when VPNs are concerned. It facilitates a secured connection with a secured network for users to work remotely and maintain the integrity of corporate data.
How does Tunneling enhance Data Transmission
Secure Encapsulation
Tunneling means packaging the data into an outer protocol and forming a tunnel that will guarantee safe communication for the information transfer through insecure channels. This kind of safe communication comes in really handy if you want to send valuable data on unsafe or unsecured networks.
Overcoming Network Heterogeneity
Distinct kinds of infrastructure, protocols, and telecommunications tools usually characterize networks. Tunneling works as a cohesion entity since it makes possible communication across numerous networking structures. This is important when information has to transit via multiple arrangements or architecture systems.
Data Privacy and Confidentiality
Tunneling is meant to keep the information private. Packets are encased such that any intermediate cannot peruse these packets, nor can it edit them. Such sectors are especially important in cases when we talk about the protection of sensitive information, like credit cards or medical data.
Efficient Remote Access
Tunneling is critical for ensuring that secure remote access is possible, most notably through the use of VPNs. It enables the creation of a safe route through which information can be safely sent to a private network utilizing the available internet system.
Versatility in Protocol Usage
Tunneling also supports different protocols, which makes it flexible in selecting the best protocol that fits a certain situation. For instance, Point-to-Point Tunneling Protocol (PPTP) is less complex, making it ideal, while IPsec offers more security and hence can be used depending on the network.
Resistance to Network Interference
Tunneling provides an extra protection layer against interference, which is present when transmitting data. This factor is crucial in networks whose operations could be interrupted by outside elements or interferences since it maintains the quality of forwarded data when they are tunneled through such environments.
PPTP Protocol
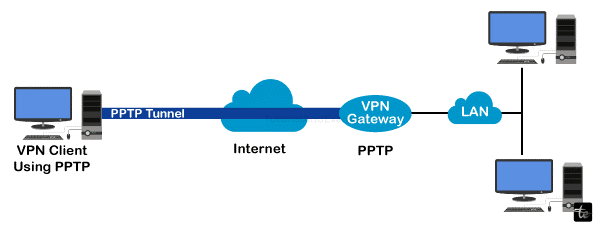
One of the well-known protocols, which can be found within the network’s environment that involves VPNs and tunneling, is known as Point-to-Point Tunneling Protocol (PPTP). Securely transfers data between remote users and the Internet.
Protocol Foundation
PPTP relies on the Generic Routing Encapsulation (GRE) protocol and is carried out at the data link layer. The process involves concealing data in GRE packets that form a tunneling path over which communication is carried out securely.
Ease of Implementation
One common characteristic of PPTP is that it is easy to implement and simple. It has become famous for its simple installation and configuration, even in those networks where one has to set up an instant VPN service. Its simplicity has made it widely used in several networking scenarios.
Compatibility
PPTP is compatible with many of today’s common devices and operating system platforms. The universal support enables the application of PPTP on different OS platforms such as, but not limited to, Windows, macOS, Linux, mobile operating systems, etc., making it more useful.
Performance Efficiency
Performance efficiency makes this protocol best fit when speed is of the essence. The design of this protocol focuses on speedy data transmission; hence, it’s one of the best picks for applications that demand low latency levels, including voice and video streaming.
Authentication and Encryption
Though PPTP offers some privacy and secrecy via encapsulates, it has come under scrutiny against its weaknesses, which are relatively less reliable compared to other VPN authentication methods.
Firewall Traversal
PPTP has a better chance of going through a firewall. It is also able to work with networks that employ NATs at their nodes. The above is what makes PPTP ideal for use across different types of networks.
Secure Shell (SSH) Tunnels
One important feature of network security is SSH tunnels, which allow for building up protected communication channels on supposedly unreliable networks. The data is transmitted through tunnels that utilize the SSH protocol in its encryption process to encrypt different types of data traffic.
Encryption and Authentication
SSH tunnels are useful in offering a secure channel of data communication since they encode all the information sent from the client to the server/remote host. The confidentiality of the data is ensured with this encryption, thus keeping it confidential and secret from other people. Further, SSH has integrated strong authentication schemes for authenticating communicating entities.
Dynamic Port Forwarding
Dynamic port forwarding is one remarkable characteristic of SSH tunnels. This enables one to build a safe tunnel that can convey all kinds of information, including web data. In this regard, dynamic port forwarding can be very useful in situations where users want to browse the Internet safely using a secure tunnel.
Local and Remote Port Forwarding
It allows for the configuration of either local or remote port forwarding. This is called local port forwarding and redirects the access from local machines onto a remote system via an SSL-encrypted tunnel. On the other hand, remote port forwarding sends traffic from a remote server to a local computer through which a secure connection is adjusted conveniently.
Bypassing Firewalls and Restrictive Networks
SSH tunnels can effortlessly get around firewalls operating in strict network situations. Users connect securely through ports and protocols that are usually blocked by encapsulating data inside the SSH protocol. It is, hence, valuable in enabling remote access and bypassing network restrictions.
Application in Virtual Private Networks (VPNs)
The creation of secure VPNs is made possible by the use of SSH tunnels. Users can be provided with a means by which they will be able to remotely access resources within a private network through an encrypted tunnel. Such applications are useful to remote workers as well as users who need to connect in order to be sure about the security of private networks.
Layer 2 Tunneling Protocol (L2TP)
VPNs are created using a widely used protocol called Layer 2 Tunneling Protocol (L2TP). The protocol works in the data link level of the OSI model and, together with Internet Protocol security (IPsec), provides an assured channel to pass information over the Internet. Here's an in-depth exploration of L2TP, shedding light on its key features and functionality:
Protocol Collaboration
L2TP works hand in hand together with IPSec as a means for setting up safe or secured virtual private networks (VPN). The L2TP/IPsec allows interoperability, resulting in the development of a secure and strong VPN solution.
Data Encapsulation
Data is encapsulated in PP frames and transmitted via the Internet with the assistance of L2TP. The frames are put into IP packets that enable safe transmission of information across networks. Encapsulation ensures that the confidentiality and integrity of the message sent are maintained.
Connection Establishment
In order to set up a connection from one endpoint to another, L2TP uses tunnels. These are safe ways of sending electronic signals. Tunneling of PPP frames forms the basis for the encapsulation and secure transmission of user data through the protocol.
Authentication Mechanisms
More so, L2TP is equipped with diverse authentication options, which further strengthen the security of the entire VPN connection. PAP and CHAP are some of the options users have when verifying the parties involved in communication.
Compatibility and Interoperability
L2TP is very compatible with the other platform or operating systems. In other words, its uniformity guarantees interoperability allowing users to easily deploy L2TP-based VPNs on routers, servers, client devices, and other types.
Internet Protocol Security (IPsec) Tunnels
Network security is based on a strong foundation that offers a secure medium of communication among all IP networks through the use of IPsec tunnels. The network security protocol IPsec is designed as a set of protocols that authenticates and secures network data.
Authentication and Encryption
Integrity and the secret of data are guaranteed by using different authentication and encryption processes for IPsec tunnels. Authentication protocols, including HMAC and encryption protocols like AES or 3DES, are used to confirm the originality of data messages sent and safe keeping of the information from wiretapping.
Tunnel and Transport Modes
IPsec supports two operational modes: tunnel mode and transport mode. Tunnel mode involves encryption of one complete IP packet, which acts like a payload for another IP packet. However, the transport mode encodes the payload and preserves the original IP address.
Key Exchange Protocols
This is done through the use of various key exchange protocols in order to create secure data tunnels for communication. For example, methods such as IKE and different protocols like Diffie-Hellman are used for securing key negotiations through the Internet. The main objective of these protocols is to enable communicating parties to develop shared encryption keys safely.
Virtual Private Networks (VPNs)
It is a baseline technology used for setting up VPNs. This technology ensures confidentiality by constructing protected tunnels, which enable their users to browse into their private network resources via the Internet safely. This becomes especially useful in the case of mobile employees or an organization that has distributed offices.
Secure Communication Between Network Devices
IPsec enables secure communications among routers, gateways, and other network elements. It guarantees that confidential information sent among different parts of a network is safe from any risk of eavesdropping or data manipulation.
Virtual Private Networks (VPNs)
VPNs are an integral part of modern networking that ensures secure and private communication across the Internet. In this section, we delve into the intricacies of VPNs, emphasizing their significance, functionalities, and the diverse types available:
Introduction to VPNs
VPNs set up secure and encrypted tunneled paths through not trusted networks like the Internet. They allow users to send and receive data on public networks if they are directly connected to private networks, maintaining privacy and data integrity.
Remote Access VPNs
Remote access VPN allows an individual user to make a secure link between a private network and a place outside of the company. In addition, this is greatly helpful especially for other personnel working away from their corporates and require their resources.
Site-to-Site VPNs
Site-to-site VPNs establish secure virtual links among different remote networks. This is often used by businesses with numerous outlets to maintain secure communication within the firms’ setup.
Client-to-Site VPNs
End-user or client-to-site VNP gives users an opportunity to connect to a private network from different gadgets while keeping secure remote access.
Benefits of VPNs
Enhanced Security
These kinds of networks help in establishing a safe path for data by preventing possible cases of snooping and malicious attempts of entry into computers.
Privacy and Anonymity
VPNs allow the user to hide his address, thus helping to ensure there is privacy and, as a result, accessibility to the Internet.
Global Connectivity
Users will have a chance to share their data with other individuals from any part of the world as long as they are using VPNs.
Challenges and Considerations
- Bandwidth Limitations: Using a VPN might increase the amount of overhead and, hence, affect bandwidth as well as the general network performance.
- Configuration Complexity: However, setting up and managing VPNs could be quite complex; this is a specialty that needs to be handled professionally so as to ensure that there would not be any loopholes that hackers could exploit.
Tunneling for Secure Web Browsing
Web tunneling is one of these technologies that contribute to a safe Internet. In this section, we explore how tunneling is employed to enhance the security of web communication:
Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
- Introduction: Secure Sockets Layer (SSL) and Transmission Security Layer (TLS) are two cryptographic protocols used to create secure communication channels between a web browser and a server. They tunnel their information, ensuring it is safe from prying eyes and ears
- Tunneling Mechanism: The second type of SSL/TLS tunneling, which is known as encapsulation, involves- encrypting HTTP traffic that is, encapsulating it within an SSL/TLS-encrypted tunnel. Such makes sure that secret information like login details and personal information is protected while in transmission.
HTTPS (Hypertext Transfer Protocol Secure)
- Overview: Secure HTTP (HTTPS) builds on HTTP by using SSL/TLS protocols to protect data transmission over the World Wide Web. Data transmission between the browser of a user and a site is safe with this option, thus reducing the danger of leakage of data.
- Tunneling for Encryption: Tunneling in HTTPS encrypts the entire communication session between the browser and the web servers. It ensures that the confidential data are secured from any perpetrators who could capitalize on loopholes in the insecure connection.
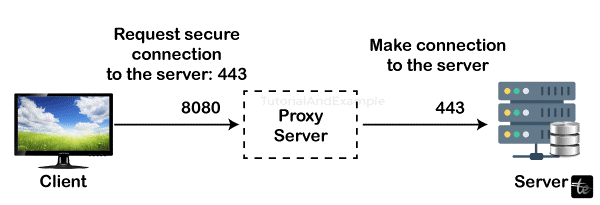
Proxy Servers and Web Tunneling
Proxy Server Functionality: Proxy servers are basically used as relay points between an individual’s browser and the Internet. They work like web tunneling through re-routing the requests as well as responses with an extra layer of encryption.
Anonymity and Filtering: The use of proxy servers allows the anonymizing of IP addresses thus enhancing anonymity. This is because they provide website screening to block harmful pages and illegal entries.
Web Application Firewalls (WAFs)
- Protection against Cyber Threats: WAFs employ tunneling techniques in examining and filtering web traffic for the purposes of preventing a host of cyber attacks, including SQL injection and cross-site scripting.
- Secure Traffic Routing: With this, all internet traffic passes through safe tubes, and all incoming information is scrutinized vigilantly to check whether it has threats in it.
Data integrity in the secure file transfer protocols
In today’s interdependent digital world, confidentiality in file transfers cannot be overlooked. This part examines two hardcore protocols, SCP and FTPS, explaining why they help secure data integrity while transmitting files.
Secure Copy Protocol (SCP)
Network protocols like Remote Copy Protocol (RCP) are usually popular. A more secure alternative known as Secure Copy Protocol (SCP) enables the transmission of files across various host computers. It runs under SSH, exploiting its integrity and confidentiality features.
Data Integrity Measures
Through the utilization of SSH for data encryption, SCP ensures that transferring files is secured from being “eavesdropped” on. The strength of SS’s encryption layer is derived from its cryptographic algorithms
Checksum Verification
During transit, the SCP uses checksums to strengthen data integrity. Before and after the transfer of each file, the checksum is computed, and in case of a difference, it denotes possible tampering or corruption.
File Transfer Protocol over SSL/TLS (FTPS)
FTPS, which is an update of the widely used File Transfer Protocol, is now based on the more secure SSL and TLS. The combination strengthens FTP, preventing weaknesses in text broadcasts.
Data Integrity Measures
- SSL/TLS Encryption: Data is encrypted using SSL/TSL protocols while it is being transmitted in FTPS. The encryption layer is used to secure the files from interception, thus enhancing their safety during transmission.
- Integrity Verification through SSL/TLS Certificates: In the FTPS structure, the integrity of the data is ensured by the SSL/TLS certificate. These certificates enable authenticated communication, providing a safe platform for file exchange between participants.
Enhancing Data Integrity in File Transfer Tunnels
Utilizing Application Layer Tunneling
- Application Layer Security: The tunnels that offer more security are obtained by application layer tunneling protocols such as SSH or TLS. As such, this additional protection guarantees the safety of the sent files.
- Checksums and Hash Functions: Using a checksum, as well as applying hash functions within the file transfer procedure, largely ensures data integrity. Checksums are generated and verified at both ends, thus mitigating the possibility of undetectable errors or tampering.
- End-to-End Encryption Protocols: End-to-end encryption protocols like PGP or GPG give another shield. These protocols make it possible for users to send files over an insecure network confidently, as the cryptographic properties ensure data integrity from the source to the destination.
Challenges and Risks
Potential Misuse
Since they are not visible, people who do not know what these unions stand for could misuse them by engaging in crimes such as cybercriminals, hackers, or unauthorized users. It entails employing strict measures that ensure that anonymous networks are not used to conduct criminal activities.
Regulatory Compliance
However, privacy often clashes with mandatory laws and regulations. Achieving a perfect equilibrium implies that there is a necessity for understanding legal terrain and measures aimed at compliance without compromising users’ privacy.
Network Performance and Latency
This is because of annexed layers of encryptions and redirecting of data traffic on anonymous tunnels, which may add delay and affect the speed of the network. Optimal configuration will help in achieving a balance that minimizes negative impacts on speed and efficiency.
Exit Node Vulnerabilities
Anonymous networks have exit nodes, which make them vulnerable. It is imperative to secure these nodes so that attacks will not compromise users’ anonymity. On this note, an effective exit node security mechanism should be put in place to ensure correct balancing.
Dependency on Encryption
The use of encryption to secure user data is essential; however, relying on encryption exposes businesses to risk by taking advantage of any existing cryptographic vulnerability. To have this effect, it is necessary to remain in touch with current encryption techniques and quickly close discovered faults.
Scalability Challenges
The issue of scalability arises as more people demand anonymity in their messages. This is why scalable infrastructures, which enhance capacity while maintaining performance for an enlarged number of users, have to be deployed and strike a balance.
Future Trends in Tunneling
Quantum-Safe Encryption
The emergence of quantum computing increases the likelihood that current encryption techniques will be breached. The modern-day tunneling solutions in the future are, therefore, expected to use quantum-secure encryption for their protection against quantum attacks.
Decentralized and Blockchain-based Tunnels
Blockchains are being used to create secure decentralized tunneling architectures. These communication systems allow the transmission to be disseminated over a decentralized network, thereby minimizing the risk associated with the weakest link of a centralized point of control.
Improved Performance with 5G Integration
The development and adoption of integration with the 5G network will have an impact on the speed and communication in tunnels. Tunneling solutions of the future are designed to make the most use of the advanced features of next-generation telecommunication systems (5G).
AI-driven Threat Detection
Tunnel security depends on AI. With the help of AI-supported threat detection tools, network traffic will be continually analyzed for threats, and appropriate actions will be taken immediately.
Privacy-Preserving Technologies
Improving user privacy is likely to be the main characteristic of future tunneling technologies. Technologies like zero-knowledge proofs and privacy-preserving protocols shall form the backbone of such applications, allowing users to have more control over their personal information.
Integration with IoT Security
In essence, future tunneling solutions will easily interface with the Internet of Things (IoT) security frameworks as IoT continues expanding. The goal is to ensure secure and private communication between a rapidly growing numbers of connected devices.
Conclusion
In Conclusion, the era ahead for secure tunneling protocols in cyber will show up as ever-evolving technology, including secure encryption, distributed Blockchain solutions, incorporation with 5G networks, artificial intelligence-enabled threat identification, and privacy advancements. With the advancement of technology, IoT security, post-quantum cryptography, and a friendly user interface will be crucial in this regard. The combination of edge computing and high-end anonymization procedures is demonstrative of a focus on minimizing response time and protecting users’ confidentiality information.