Role of artificial engineering in cyber security
Introduction
In dealing with and surviving in the digital era, cyber security is the major requirement in protecting confidential data and providing integrity and availability of data. Cyber security is designed using artificial technology that makes it interactive and usable to the user.
Artificial intelligence is making a new and irreplaceable place in cyber security & becoming more and more prevalent in society. An organization that implements AI systems can increase its detection speed, become more proactive in predicting threats and be responsive in handling emerging threats. AI also helps in identifying vulnerabilities and improving network efficiency.

Artificial intelligence (AI) Definition
“Artificial intelligence technology can be considered as computerised human abilities applied in the computer world to work same as human does in real world. AI is used in machine which enable them work like natural intelligence displayed by humans and other animals.”
Using artificial intelligence, applications are created that analyze data and make their own decisions without human intervention. Applications are designed with complex algorithms that allow the computer to solve such problems only solvable by humans.
The main aim of artificial intelligence in cyber security is to standardize security measures by using such software or application in systems with AI capabilities to augment human expertise by quickly recognizing new hacking attempts or malicious traffic.
Artificial intelligence came into existence in the computing world when Alan created his AI test in 1950 with a proposal to determine whether a machine could have human cognition.
Artificial intelligence includes three main components:
- Learning – Method of acquiring new skills and knowledge from experience.
- Reasoning – Drawing a logical conclusion from a set of premises
- Self-correction – Ability To identify and correct errors
Working on AI in cyber security?
Artificial intelligence has proved itself as an independently working application without human workers, but these workers are still responsible for overseeing AI projects. AI has grown as computer intelligence to significantly benefit cyber security operations in various machines and organizations.
In machine learning, artificial intelligence learns to complete a task through a large amount of independent data. In cyber security, artificial intelligence does not need large clusters of high-end servers with expensive processors as it can work relatively with small databases (this further help in processing with standard GPUs or CPUs).
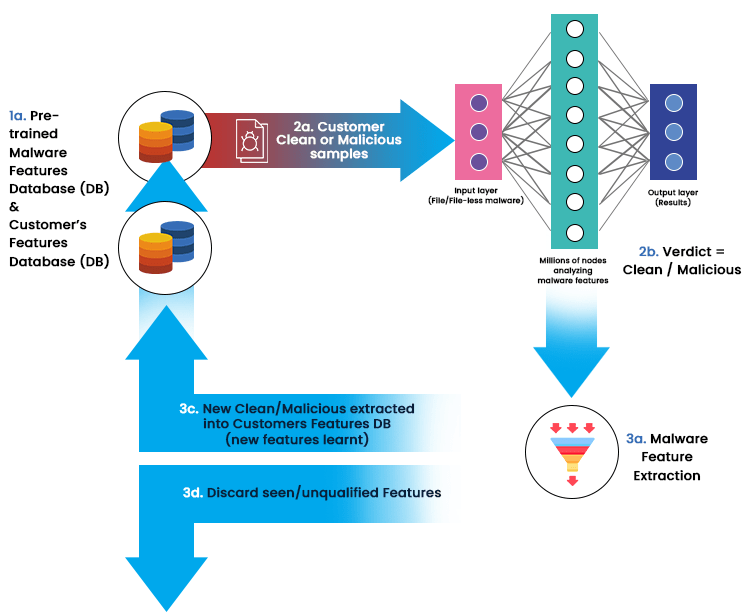
Artificial intelligence is getting smarter daily and improving its risk-identifying abilities using machine learning. With this, AI can find vulnerabilities that attackers can exploit by identifying outliers from typical behavior or traffic. AI help in detecting anomalies in the system that humans further analyze for validity or other clues about what caused them. AI does everything accurately, so analysts will no longer need to double-check everything. AI mainly performs these functions:
- Anomaly detection – In cyber security, machine learning detects anomalies automatically, like unexpected network activity or unusual user behavior, which indicates a security threat. For example, some products like dark trace, crowd strike, and many others use this.
- Classification – Machine learning automatically classifies data, including emails or files, dealing with malware or spam more efficiently.
For a running and growing business, the companies must use artificial intelligence to fight against cyber-attacks, and cybercriminals, identify malicious behavior, preventing attacks through anomaly detection with machine learning-assisted tools in an automated way. A combination of four methods is used in a company of artificial intelligence:
- Spear Phishing defense artificial intelligence
This artificial intelligence defense system fights phishing attempts against email accounts. In this spear phishing defense system, NLP algorithms are used for text generation applied to the huge amount of data consisting of real email and spammy content to understand the difference between spam and normal email communications.
Artificial intelligence tools are utilized in security systems for fighting spam by detecting suspicious phrases & cut down on the amount of spam we have to sift through. All cyber security companies use artificial intelligence to fight back against scams.
- Vehicle security artificial intelligence
Vehicles like cars, airplanes, ships, etc. security systems use artificial intelligence to monitor everything about the vehicle without needing manual monitoring. Artificial intelligence is implemented to make them automated & play a big role in keeping our vehicles safe and secured. The cyber security researchers at the University of South Florida (USF) designed an artificial system for vehicles that analyze data from car sensors to detect something wrong or not with the vehicle.
- Badoo artificial intelligence
Various companies use artificial intelligence in their services to make them easier for the user. Badoo uses artificial intelligence to match up people by interest and location. People have a common interest and are closer than their profile appears on their feed. It is a well-defined method of connecting with people online with common interests instead of wasting time messaging someone who has a different religion and doesn't speak the same language. AI highly supports this concept in security to reduce the time and effort required to find someone with commonalities while connecting online.
In an organization, AI is used in several ways and in different areas like:
- Network security
- Data security
- IoT security
- Application security
- Identity and access security
- Cloud Security
- Endpoint security
Threat detection – In an organization, artificial intelligence and advanced machine learning algorithms are utilized in identifying threats, malicious activities, and intrusion. Various cyber security firms deployed AI algorithms to investigate and identify indicators of attacks. Changes in behavior and real-time detection of deviation occurrence help an organization respond intelligently and faster.
Network security – For the assurance of better network security, organizations use AI-enabled software at the network level. Artificial intelligence tools are used to read data which also include:
- Understating and identifying patterns
- Detect hundreds of objects, including
- Various files
- IP addresses
- Links to identify thefts
- A large amount of data
Humans can scan millions of websites and addresses. Still, AI can do this much faster than human detection with real-time detection and automated processes that help organizations respond more efficiently and faster.
Prevention of attacks- Cyber-attacks are the main reason for cyber security requirements, and in business, reducing the risk of cyber-attack is a top priority. Traditionally, measures like humans can take days or months to find a breach and take responsive action, but using artificial intelligence tools can reduce the searching and responsive time. AI tools are widely used for anomaly detection in applications, software, or system as algorithms can process a large amount of data per second which is next to impossible for humans. Companies or businesses develop themselves as more automated by using AI-driven security measures as a more effective method of preventing an attack before or after it does potential damage.
Predictive analysis - With the identification or detection of anomalies, it is mandatory to do analysis (user behavior) to prevent cyber-attacks. AI algorithms learn user behavior (login times, typing and scrolling patterns, IP address, and timing) and create patterns about platforms, usage, and timing. Tools in AI quickly detect errors in data and behavior by constantly monitoring real-time data, which also helps reduce the possibilities of potential damage.
List of AI applications used in cyber security today
| IDS (AI-based Intruder Detection System) | The intrusion detection system is designed to detect potential cyber threats by learning the difference between malicious and normal traffic patterns. It looks for something suspicious or unusual happening in the system or application. |
| AIOps Platforms | AIOps is a cloud-based system to fight cyber threats before they happen. It can run AI algorithms over massive amounts of data containing real-time malicious and normal traffic patterns. |
| Machine learning-assisted hacking tools | Highly advanced hacking tools are created with the help of artificial intelligence, which is more powerful than anything. For example, machine learning assisted malware analysis of artificial intelligence in creating highly sophisticated hacks. |
| Machine learning-assisted malware analysis | Advance malware analysis tools are created with the help of artificial intelligence, which is useful in fighting cyber criminals and their increasingly complex hacks and scams. These tools allow AI to scan huge amounts of data in search of patterns. AI does this work rapidly compared to humans who tried it manually and find signs of unusual behavior. |
Advantages and disadvantages of AI in cyber security
| Advantages | Disadvantages |
| It provides human accuracy (Humans couldn't be able to provide as much accuracy as AI can because it use millions and thousands of data points to find pattern and anomalies) | Artificial intelligence can be manipulated. (AI works on the fed information & if this information is false or misleading, then cyber criminals can take advantage of it to carry out attacks and evade detection) |
| In terms of speed (artificial intelligence detect the problems at a tremendous speed and create alert to potential problems before or early they arise or later when damage has already been done) | Artificial intelligence can be fooled. (cyber-criminals know about hacking because they can hack the user using AI. A denial of service (DoS) attack launched using AI against a company's server is an example. |
| It works 24/7 (AI systems can't take rest –sleep or take off to be with their families. It is an ideal solution to the business as it operates 24/7 and gives peak performance every time) | It can be easily hacked . (humans also design AI. Therefore, it can be hacked by experts and used to carry out cyber-attacks) |
| It detects changes and keeps alert. (AI detects the changes in the network, including physical and digital ones. It monitors the activities of a system like the second set of eyes) | It can be used for surveillance. ( AI is used to track individuals' online activities & for surveillance that has a serious impact on privacy and freedom of speech) |
| It provides no boredom and no interruptions. (AI performs all the functions without human interactions, interruption, or distractions) | It cannot be very objective. (Sometimes AI results in biasness against certain individuals or groups of people) |
| Include better risk assessment (AI shifts far more information than a human does and interprets all the data to make a risk assessment. AI provides better risk assessment and a more holistic view of threats) | Still surviving in its infancy. (AI is a vast field. Therefore, one should be careful about using it in critical systems like cyber security) |
Benefits of artificial intelligence in cyber security
- Artificial intelligence learns more over time
With time technology aspects changes, and it is becoming more intelligent by improving its ability to improve network security over time. It uses deep learning and machine learning to recognize patterns on the network and cluster them. Artificial neural networks learn new patterns over time that can help improve future security by detecting deviations or security incidents from the norms before responding to them. Being learning with time, AI tries to keep itself updated and make it difficult for hackers to beat its intelligence.
- It can handle a lot of data.
An average mid-size company has huge traffic and many activities on its network. AI tracks the data transferred between business and customers daily and protect malicious software and people because cyber security personnel can't check all the traffic for possible threats. Automation in AI makes it to skim through massive chunks of data and traffic. For example, Residential proxy technology uses AI that helps the user to transfer data and detect and identify threats hidden in the deep sea of chaotic traffic.
- Help in identifying unknown threats
Humans couldn't track all the threats faced by the company because hackers launch millions of attacks every year with different motives, which can cause massive damage to the system and network. AI is the best security technology to detect, identify, and prevent unknown threats from ravaging a company beyond cyber security experts or human imagination.
- Provide better vulnerability management
A company deals daily with many threats which need to be detected, identified, and prevented, and this company implements vulnerability management to secure the company's network. Artificial intelligence research help in vulnerability management by analyzing and assessing the existing security measures & increasing problem-solving ability. The vulnerability management system is a structured process that identifies weak points in business and computer systems. It also helps businesses to focus on important security tasks. Cyber security experts manage the vulnerability management system in the business.
- Overall better security on the inside and outside of the system
With time new threats arise in the system because hackers regularly change their attack tactics. All the systems must deploy AI on the network to detect all types of attacks and prioritize & prevent them.
- Reduce the duplicate processes
Cyber security experts get bored by applying the same security best practices, but attackers change their tactics regularly. After feeling tired and complacent, the security experts miss an important security task and expose the network. Ai will easily deal with this as it mimics the best human qualities and handles the duplicative cyber security processes. AI analyses the network in depth without getting bored with regularly finding the security holes and preventing them.
- Securing authentication
Now, every website or application needs login credentials to sign up or create a user account for further access, which hackers smartly or easily exploit to gain sensitive information. To deal with this, cyber security needs an extra layer to protect the sensitive data or personal information on these sites. This can be done by using artificial intelligence with cyber security that secures the authentication anytime the user wants to log into their account. AI tools like CAPTCHA, facial recognition, and the fingerprint scanner can provide a double security layer by detecting whether a login attempt is genuine or not. The whole company's network would be at risk if an attacker could enter a user account, and for this, hackers use brute force attacks and credential stuffing to access the company network.
- Accelerates detection and response time
The company's security depends on the threat detection procedure and the time taken to fix them. Therefore, AI integrated with cyber security detects threats by scanning the system and extremely early response to them to simplify your security tasks. It shows the company's CIA (confidentiality, integrity, and authentication) feature.
Conclusion
Artificial intelligence is the future of cyber security because real-world examples depict how AI uses to defend our networks today. Every technology has some pros and cons; therefore, security analysts have to decide whether AI should be part of cyber security strategy or not. With time hackers are getting smarter, so to tackle them, AI will become an increasingly important tool to fight against cybercrime. With several benefits, AI strengthens the security infrastructure, will become an integral part of business cybersecurity in the future, and will continue to grow its utility among companies.
Here are some of the artificial intelligence security services and cloud services:
- Same person identification
- Identity proofing
- Web content visual analysis
- Account takeover identification
- Transaction fraud detection
- File-based malware detection
- Abnormal behavior analysis
- Security posture and risk scoring
- Hazard intelligence
- Event correlation
- Policy recommendation engine
- Business data risk classification
- Security operation task automation
- Adaptive runtime access & entitlement
- Asset inventory and dependency mapping optimization
- Web, domain, and reputation assessment
- Process behavior analysis