Blockchain - Public Key Cryptography
Among the most significant inventions of the twenty-first century is blockchain technology. The idea of cryptography, specifically public-key or asymmetric-key encryption, will be the main topic of this essay.
A Brief Overview of Public-Key Cryptography
Public-key, the use of cryptography, sometimes referred to as asymmetric-key encryption, is what blockchain technology uses most of the time. Data encryption and decryption in cryptography with public keys employ both private and public keys. While the private key is not possible to share with anybody, the public key may be freely spread out. It is frequently used securely for a couple of users or two computers.
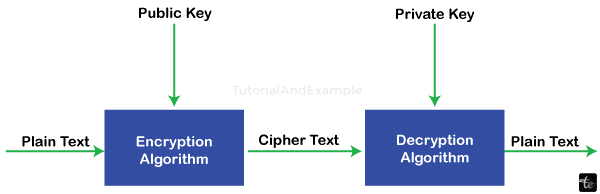
A security mechanism called public key cryptography makes sure that the information we transfer in the network of blockchain transactions is secure. Security is an important consideration in point-to-point networks such as blockchain. Since nodes in such a system do not have confidence in one another on an individual basis. A strong security system must be put in place. One that guarantees the security of the data they send and receive without having to worry about security lapses. This also removes the requirement that every node physically be acquainted with every other node.
A pair of keys is used in cryptography with public keys, an unequal form of encryption (public key and private key). They are used to verify user identities and encrypt/decrypt the data. Two things are guaranteed by the cryptography with a public key process. that is,
- Information is encrypted at the sender's end utilizing the recipient's public key. By doing this, it is made sure that no unauthorized person is able to view or decipher encrypted data entering or leaving the network. Utilizing its key, the electronic communication can only be decrypted and read by the person who wrote it.
- Using the sender's private key to sign the communication or data in order to verify it. This confirms the authenticity of the sender and establishes his legitimacy as a node within the distributed ledger network. The recipient uses the public key provided by the sender to confirm this. Digital signatures are used in that network's user identification procedure.
Cryptography using public keys is, therefore, a means of giving the user an online identity. This allows for safe transactions to be conducted within the framework of a blockchain. Let's examine the precise mechanism by which this occurs.
Public-key cryptography consists of three main components: (i) a pair of keys (private and public), (ii) a cryptography wallet and wallet location, and (iii) an electronic signature. Similar to our financial institution's number for the account and password, each of the elements above plays a vital role in establishing a reliable online identity. Here, the sole distinction is that data or cryptocurrency are being exchanged inside a distributed ledger system.
These keys are generated by unique algorithms in public key cryptography. These algorithms are bidirectional, meaning that they generate a public key, a private key, and an address that is publicly accessible first. It is not possible to calculate the wallet address from a public key or the private key from the public key in inverse the sequence of creation.
This further guarantees the public key encryption system's integrity. This is due to the fact that the transaction and verification procedures require the public key and public IP address to be disclosed.
As a result, public-key cryptography guarantees the accuracy of the data, the user's identity, and the exchange's validity. For a user, a private key is comparable to an account password. A coded communication can be decrypted and used to create a digital autograph for confirmation.
To validate an exchange and secure an email, other users can access an open secret key on the network. As a result, both the private and the public keys of both nodes participate in securing any transaction that occurs between them. It accomplishes this by encoding the data and using the user's encrypted signature to confirm identity. The most effective protection mechanism for blockchain technology is encryption with public keys because of an additional layer of defense.
Key concepts: Public and Private keys
In public-key cryptography, cryptographic keys are an especially important component. In the field of public-key cryptography, there's little left to learn without understanding the purpose and importance of keys. Let's study the idea of keys now!
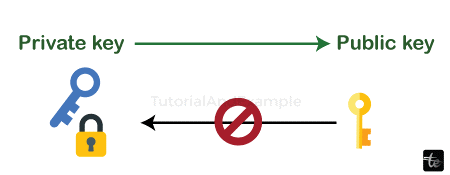
In public-key cryptography, as is well known, we employ a pair of keys, namely the public and confidential keys. These two keys are produced by employing the Elliptic Curved encryption technique. It first generates the private key, and then it uses the Elliptic Curve Algorithm (also known as ECDSA) to generate the public key using the private key. Consequently, there is a logical and cryptographic relationship between the two types of keys.
This is a crucial point to remember: creating a publicly accessible key from a private key is an irreversible process. In other words, we are able to acquire the matching public key from the private key that it holds, but not the other way around. The technique was constructed in a way that makes brute forcing the secret key extremely difficult and demands a significant amount of computing power and time.
The private key is kept secret and unidentifiable from the publicly accessible key with the aid of this method.
Public key:
The public key is intended to be accessible to all. They are able to freely distributed to individuals or shared online. The unprotected text message can be encrypted into a cipher code through the use of the public key. Additionally, it is employed to confirm the sender's identity. To put it plainly, a public key is required to close the lock.
Private Key:
The general key and the private key are completely different. The private key is never disclosed and remains perpetually private. We can convert ciphertext communications into plain text by using this key. To put it simply, the doorknob can be opened with the help of a private key.
Blockchain-based Digital Signatures
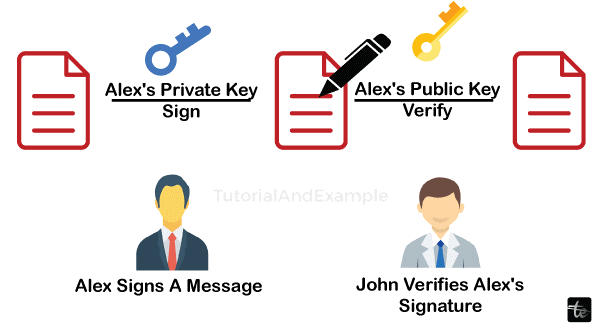
The digital signature is a crucial component of public-key cryptography, following the private and public keys. If an exchange in a distributed ledger system isn't digitally signed with the private key used by the sender, it's not safe. By encrypting data with public and private keys, encryption guarantees that the data we send to different nodes is secure and that nobody in the receiving node can read or alter it.
In a similar vein, one indicates that they are an authorized node in a distributed ledger network by electronically signing the data they send. Additionally, the tokens or money you want to donate to a network member are legally yours. Consequently, the digital signature guards against fraud and demonstrates who owns the money and account.
Why Is Public-Key Cryptography Required?
Symmetric-key cryptography encrypts and decrypts messages using a single key. There is a significant chance of losing information or illegal access in this situation. We use cryptography with public keys to prevent unwanted utilization of data and to ensure that data is sent safely without experiencing loss.
Although a common key requires two keys to both encrypt and decrypt data, cryptography using public keys is more reliable than symmetric-key encryption.
With public-key cryptography, users can transmit data while keeping it anonymous. Data is encrypted by the sender and decrypted by the recipient. Users who are not authorized cannot decipher the message that has been compressed.
Working with Cryptography on a Public Key
Let's say the sender wishes to convey to the recipient a crucial message.
- Initially, the message is created by the sender in legible plain text format.
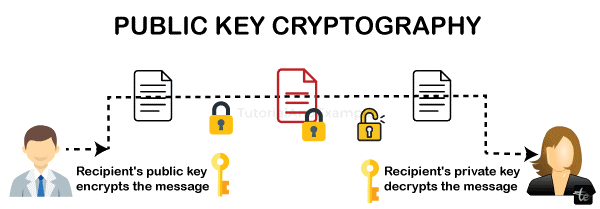
- Because the recipient maintains his password secret, the sender is aware of the recipient's public key but not his confidential one. The sender creates a message that is encrypted, also known as a cipher text, with the aid of the public key of the target from the private key belonging to the sender. The format of the cipher text is illegible. This stage transforms ordinary text into encrypted text.
- The recipient end now receives the encrypted text. The recipient decrypts the code into understandable form, or plain text, using its key, which it possesses.
The instance below demonstrates how public-key cryptography operates.

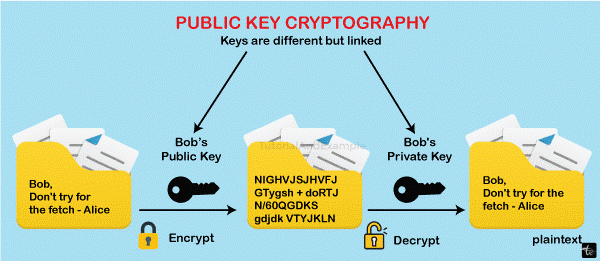
Let's attempt to explain how public-key cryptography functions using an example. Assume that Sachin is the one wishing to communicate with Anurag. Here, the recipient is Anurag.
- The communication is encrypted by Sachin using Anurag's public key, and it is decrypted by Anurag using his private key.
- Sachin starts by writing plain text. Sachin has the cipher text and Anurag's private key. Sachin will produce an unintelligible encoded message, or a cipher text, using Anurag's private key and his particular public keys. After the encryption procedure is applied, plain text becomes cipher text.
- Anurag now gets a text message encrypted. Anurag will start by translating the encrypted text communication into a legible format. Anurag is going to use the secret key to decrypt. The recipient is able to view the cipher text once it transforms into plain text. Anurag is aware that no one else could have sent this message since Sachin maintains a secret key to himself. Another name for this is a digital certificate.
Public-key Cryptography's Advantages
- Verification: It guarantees that the recipient got the data from only one verified source.
- Data integrity: It makes sure only specific, permitted modifications are made to the program and data.
- Data confidentiality: It makes sure that a third party cannot access an encrypted message. It's known as confidentiality or privacy.
- It is the guarantee that the information's original author cannot retract the communication to another party.
- Key administration is made possible by the use of public-key cryptography since private keys cannot be exchanged or sent. This does away with the symmetrical key encryption requirement for a safe channel to transfer a private key.
- Digital signatures: Digital signatures, which offer non-rep and may be used to confirm the reliability and integrity of data, are made possible by the use of public-key cryptography.
- Key exchange: Absent a pre-shared hidden key, public-key cryptography allows both parties to swap keys securely. In the event that both individuals have never spoken before, this enables confidential interaction.
- Secure communication: By encrypting information with the recipient's public key, which may only be decoded with the recipient's private key, cryptography using public keys provides safe interaction over an unreliable channel, like the internet.
- Versatility: Electronic signatures, safe communication, and verification are just a few of the uses for the use of public-key cryptography, which makes it an adaptable tool for communications and data security.
Public-Key Cryptography's Drawbacks
- Data or messages with a fixed size can be encrypted and decrypted. The algorithm requires a lot of processing capacity if a large message is being attempted to be encrypted or decrypted.
- The primary drawback of this method is that the data and message will be permanently lost if the person receiving it misplaces their private key.
- All of the data could end up in the wrong hands if a person manages to obtain the private key.
- Many secret keys exist, and they're able to operate more quickly than public keys in encryption.
- Distribution of keys: It can be difficult and costly to securely distribute common keys to all those with authorization, particularly in large networks.
- Performance: Because of its more complicated computations, public-key cryptography is typically slower than symmetric-key cryptography, which makes it less appropriate for applications that demand immediate execution times.
- Assumptions made about security: Public-key cryptography depends on theoretical presumptions about how hard it will be to solve specific issues, like factoring big numbers, in the years to come. Public-key cryptography is, therefore, susceptible to future improvements in processing power and algorithm discoveries.
- Private-key encryption is susceptible to attacks known as man-in-the-middle, in which a hacker captures and modifies the public key after it gets to the intended receiver. Because of this, the attacker might be able to decode the communication or pretend to be the sender.
- Complexity: Compared to symmetric-key the use of cryptography cryptography that uses public keys can be more difficult to comprehend and use, requiring a high level of expertise.
Conclusion
Our discussion of public-key cryptography is now complete. We have discussed a wide range of PKC-related topics here. For example, what is an electronic signature, how PKC operates, what is PKC, the idea of public keys as opposed to private keys, and finally the advantages and restrictions of PKC. We hope that the details that we supplied helped you gain an adequate grasp of the cryptography using public keys.