HMAC Algorithm in Cryptography
HMAC stands for Hash-Based Message Authentication Code. It is a type of message authentication code that is obtained by executing a cryptographic hash function that is used to be authenticated and secretly share the key. HMAC is used for authentication and data integrity, similar to other Message authentication codes (MAC). The vital function of the HMAC algorithm is to check the data integrity involved in the communication process. HMAC uses transmission protocols like SFTP, HTTPS and FTPS. The cryptographic function used in HMAC is SHA-1, MD-5 and SHA-256. The HMAC algorithm is very similar to digital signature because both use a shared key and hash function. The only difference is that HMAC uses a symmetric key, whereas digital signature uses an asymmetric key.
History of HMAC
The process and decision depend on data integrity. If the hacker damages the data, it affects the data's function and conclusion. So we must ensure our data integrity during working over the internet. To overcome this problem, HMAC comes to the world of cryptography.
Application of HMAC
There is various use of HMAC in the field of cryptography and network security. These are as follows.
- With the help of HMAC, we can verify the details while logging in or creating an account.
- The data is then authenticated and sent back to the browser with the help of HMAC.
- Due to less cost, HMAC is used in the field of the Internet of Things (IoT).
- When the user needs to reset their password, then with the help of HMAC, the server sends a verification link to the user.
- With the service of HMAC, the user can convert any data length to a fixed-length message.
Objectives of HMAC Algorithm
- The main aim of HMAC is to quickly generate the output from the input text.
- The HMAC algorithm is less affected by collision in comparison to the hash function.
- HMAC has the ability to reuse algorithms like SHA-1 and MD5 and then replace these with embedded hash functions.
- HMAC tries to handle the key very simply.
Working of HMAC
HMAC provides a private key, which is known to both the server and the client. The client generates a hash key for every request. There are three types of authentication functions. They are message encryption, message authentication code, and hash functions. The significant difference between MAC and hash (HMAC here) is the dependence on a key. In HMAC, we have to apply the hash function along with a key on the plain text. The hash function will be used for the primary text message. But before applying, we have to compute S bits and then append them to plain text and apply the hash function. For generating those S bits, we use a shared key between the sender and receiver.
HMAC Algorithm
The work of the HMAC algorithm starts by taking the message M from the block of length L bits. Then the input signature is merged with the left message and the whole input gives the output of the embedded hash function. Then the entire hash function is again applied with the complete message. After this, the final note has come.
Here is the diagram for the HMAC algorithm.
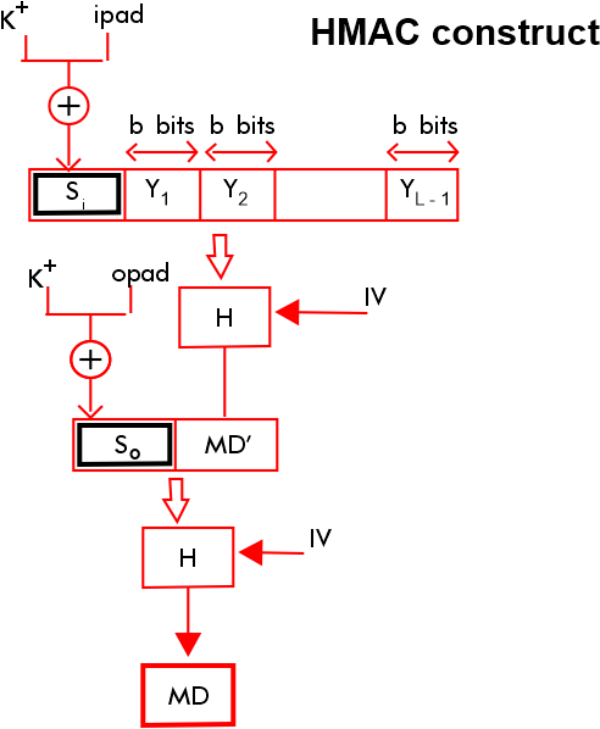
Here H = hash function.
M = original message.
Si = Input signature.
So= output signature.
Yi = ith block of the message M whose length range from 1 to L.
L= number of blocks in message M.
K= secret key used for the encryption process.
IV = initial vector.
Advantages
- HMACs are ideal for high-performance systems like routers due to the use of hash functions which are calculated and verified quickly, unlike public key systems.
- Digital signatures are more significant than HMACs, yet the HMACs provide comparably higher security.
- HMACs are used in administrations where vital public systems are prohibited.
Disadvantages
- HMACs use shared keys which may lead to non-repudiation. If either sender or receiver's key is compromised, it will be easy for attackers to create unauthorized messages.