Data Compression Techniques
Introduction
In information theory, encoding information using less data than the original presentation is called data compression, source coding, or bit-rate reduction. Compression comes in two flavours: lossy and lossless. By identifying and removing statistical redundancy, lossless compression reduces the bit count. Knowledge is not degraded by lossless compression.Reducing the size of an information-containing file is known as "data compression." In Under the overall architecture of data transmission, encoding takes place at the data's point of origin before being stored or sent; this is called source coding.
Because it requires less equipment for data transmission and storage, compression is beneficial. Both the compression and decompression operations use up computer resources. Space-time complexity and data compression are mutually exclusive.
Purpose of Compression
Compressing a file, message, or other piece of data aims to reduce its size. A file's storage space requirements can be greatly reduced by using data compression. Given that the reduced file size of 5 MB is half of the original 10 MB file, we would compress the smaller file using a compression ratio 2. The new file is a tenth the size of the original, so if we compressed the 10 MB file to 1 MB, the compression ratio would be 10. The quality of the compression increases with the compression ratio. Using compression instead of other methods, administrators save time and money on storage.
Compression has an impact on main storage data reduction as well as improving backup storage performance. Compression will remain a key component of data reduction as data continues its exponential rise.
It is possible to compress almost any file, but choosing which files to compress requires careful consideration of best practices. For instance, compressing already compressed files won't significantly affect them.
Types of Data Compression Techniques
Although this PDF [source] data compression approach can be consulted to learn about the various types of technologies available, two common characteristics continuously stand out:
- Lossy
- Lossless
Lossy Compression
Before fully comprehending the lossy compression technique, we must understand the difference between data and information. Numbers, words, symbols, or any other information or value in its unprocessed, often messy form can all be called data. On the other hand, information carefully arranges the data to provide perspective. Lossy audio compression uses psychoacoustic techniques to eliminate undetected (or less invisible) audio signal parts. Beyond flexible audio compression, speech coding is a separate topic that frequently needs aid from more specialized techniques. For example, players decode audio compression; a method for ripping CDs. Internet telephony makes use of speech coding. The outcome of lossy compression could be generation loss.
Early in the 1990s, lossy compression techniques gained popularity. Certain schemes allow for a certain amount of information loss because eliminating unnecessary details might free up storage space. The trade-off between shrinking size and maintaining information is similar. Research on people's perceptions of the data under consideration is used to build lossy data compression algorithms. The human eye, for instance, is more sensitive to minute changes in brightness than it is to colour variations. One method of JPEG image compression is to round off unnecessary information. Numerous widely used compression formats, such as psycho-visuals for images and video and psychoacoustics for sound, use these perceptual variations.
Digital cameras employ lossy picture reduction to boost storage capabilities. Similarly, lossy video coding formats are used by Blu-ray, DVDs, and streaming video. In the video, lossy compression is widely utilized. Psychoacoustic techniques are employed in lossy audio compression to eliminate inaudible or less audible parts of the audio stream. More specialized methods are frequently used to compress human speech; speech coding is unrelated to general-purpose audio compression. For example, audio compression is used for CD ripping and is decoded by audio players; speech coding is utilized in internet telephony.
Advantages of Lossy Compression
The technique known as lossy compression offers the unique advantages of being comparatively quick, having the ability to significantly reduce file sizes, and giving the viewer the option to select the right compression rate. This has the advantage of compressing data such as images, videos, and music by taking advantage of the limitations of human vision.
Disadvantages of Lossy Compression
One drawback of lossy compression is that, when decompressed, it does not yield the same information (quality, size, etc.). It will, nevertheless, keep containing comparable data (which is useful in some circumstances, such as while streaming or downloading information from the internet).
Lossless Compression
Lossless data compression methods are reversible because they transfer information without erasing data using statistical redundancy. Lossless compression is possible because statistical redundancy characterizes most real-world data. For example, a colour that appears in multiple pixels in a picture can be encoded as "279 red pixels" instead of "red pixel, red pixel,..." This is a simple example of run-length encoding; there are also other ways to reduce the size of a file by eliminating unnecessary information.
In contrast to lossy compression, which eliminates data, lossless compression alters data instead of eliminating it to reduce its size. To enhance comprehension of the idea, let us examine a basic example.
The most robust lossless compressors available today use probabilistic methods like prediction by partial matching. Another way to think about the Burrows-Wheeler transform is as a subliminal kind of statistical modelling. An approach known as arithmetic coding can be used with statistical estimates to further improve the direct application of probabilistic modelling. More recently, a method called arithmetic coding takes advantage of the mathematical operations of a finite-state machine to generate a string of encoded bits from a sequence of input data symbols. It can achieve better compression than other methods, such as the more well-known Huffman algorithm. Since arithmetic coding is easily combined with an adaptive model of the input data's probability distribution, it works particularly well for adaptive data compression jobs where the statistics are context-dependent and fluctuate. An optional (but seldom utilised) component of the JPEG image coding standard was an early illustration of arithmetic coding. Since then, it has been used in several other designs, such as the video coding standards H.263, H.264/MPEG-4 AVC, and HEVC.
Advantages of Lossless Compression
Lossy compression is not compatible with all data types. Since the document may be unpacked and compressed back to its original state without losing any information, lossless compression is still required in these situations.
Disadvantages of Lossless Compression
There is a limit to how much space can be used for data compression. If the data has already been compressed, adding more compression won't make a difference. It also becomes less effective when the file size is bigger.
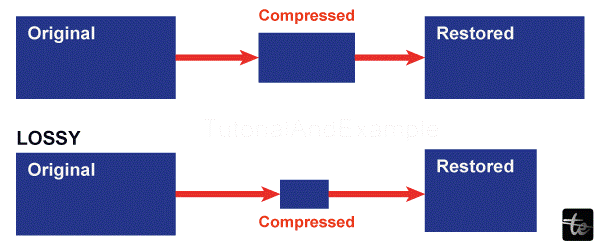
Difference between Lossy Compression and Lossless Compression
The key distinctions between Lossy and Lossless compression are shown in the following table.
| Key | Lossy Compression | Lossless Compression |
| Data Elimination | By using lossy compression, you can get rid of bytes that are regarded as unnoticeable. | Even unnoticeable bytes are retained with lossless compression. |
| Restoration | After lossy compression, a file cannot be restored to its original form. | After lossless compression, a file can be restored to its original form. |
| Quality | Quality suffers as a result of lossy compression. It leads to some level of data loss. | No quality degradation happens in lossless compression. |
| Size | Lossy compression reduces the size of a file to a large extent. | Lossless compression reduces the size but less as compared to lossy compression. |
| Algorithm used | Transform coding, Discrete Cosine Transform, Discrete Wavelet transform, fractal compression, etc. | Run length encoding, Lempel-Ziv-Welch, Huffman Coding, Arithmetic encoding, etc. |
| Uses | Lossy compression is used to compress audio, video and images. | Lossless compression is used to compress files containing text, program codes, and other such critical data. |
| Capacity | The data holding capacity of the lossy compression approach is quite significant. | Lossless compression has low data holding capacity as compared to lossy compression. |
Importance of Data Compression
Administrators can save money and effort on storage by using data compression, which can significantly reduce the amount of storage a file requires. For instance, a 20 megabyte (MB) file compressed to a 2:1 ratio only takes up 10 MB of space.
Compression improves backup storage speed and has been demonstrated recently in primary storage data reduction. With data growing exponentially, compression will become a crucial data reduction technique.
Almost any kind of file can be compressed, but choosing the right ones to compress is crucial based on best practices. For instance, some files might already be compressed, so compressing them won't make much difference.
Compression vs. Data Deduplication
The bit strings in a data stream are made smaller using data compression techniques, which usually only recall the last megabyte or less of the data. Although the two techniques are frequently used interchangeably, compression and data deduplication work differently. A sort of compression called deduplication finds redundant data chunks throughout a file system or storage device and replaces each one with a pointer to the original.
Block-level deduplication finds duplicate data at the subfile level. To save the unique occurrences of each block in an index, the system produces a unique identifier, processes them using a hash technique, and stores them. File-level deduplication replaces unnecessary files with stubs that refer to the original file instead of the extra files. Systems can use a fixed or variable-sized chunk for deduplication, often searching for bigger chunks of duplicate data than compression.
When minimizing the amount of unique information-like pictures, audio, videos, databases, and executable files-data compression usually outperforms deduplication. Compression and deduplication are both supported by many storage systems. Environments with highly redundant data, such as virtual desktop infrastructure or storage backup systems, are best suited for deduplication.
File System Compression
By dynamically compressing all newly created files as soon as they are produced, file system compression employs a pretty simple strategy to minimize the amount of content that needs to be stored. Most of the well-liked Linux file systems, such as Reiser4, ZFS, btrfs, and Microsoft NTFS, offer the possibility of compression. A file's data segments are compressed by the server that hosts it and subsequently stores the smaller pieces. Compression is rarely recommended for volatile data because read-back has a comparatively small delay for expanding every component, whereas publishing places a heavy burden on the server. Administrators should use file system compression sparingly and only on documents that aren't regularly retrieved because it can reduce efficiency. Data compression software, like DiskDoubler and SuperStor Pro, became common and contributed to the mainstreaming of file system compression due to the pricey hard drives that came with early computers. Memory controllers might additionally use the approach of applying compression and deduplication over better data reduction.
Technologies and products that use data compression
Compression is a feature of several technologies that include storage systems, databases, operating systems, and software programs employed by commercial enterprises. Consumer electronic gadgets like laptops, desktop computers, and cell phones frequently compress data as well. Although numerous devices and gadgets conduct compression invisibly, few allow consumers to toggle compression on or off. It might be done multiple times on an identical file or portion of data, though successive compressions produce no or little extra compression and, based on the information's compression techniques, could slightly raise the size of the file. A well-known Windows software program called WinZip compresses files when it stores them as part of an archive. ZIP and RAR are two archive file types that provide compression. A single file can be compressed using the BZIP2 and GZIP formats. Other manufacturers of compression consist of Silk (formerly Kaminario), with its K2 all-flash array, and Dell, with its XtremIO all-flash array.
Data Differencing
"Data differencing" is a general term that compares the specifics of two data collections. In the context of compression, it means continuously searching the destination file for similar portions to replace with references to library items. Repeat this process until no more identical objects are found. The same library component could represent each duplicate item due to information differentiation, potentially resulting in several compressed files.
On virtual desktops, this technique can achieve a compression ratio of up to 100:1. Deduplication is more closely related to this process, as it looks for similar files or objects rather than within the information of each object. Data differencing is also known as deduplication.
Conclusion
After reviewing the material above, we can conclude that while lossy compression causes some degree of data loss and quality degradation when a file is being decompressed back to its original state, it can be a useful tool for greatly reducing the size of multimedia and image files so they can be easily transferred over the Internet. Furthermore, multimedia files may tolerate some degree of data deterioration. On the other hand, files, including text, program codes, and other types of data, are compressed using lossless compression because any loss of data would render the files unusable.