Kali Linux Tutorial
What is Kali Linux?
Kali Linux is the Debian-derived based on Linux distribution for digital forensics and penetration testing. It is maintained and funded by Offensive Security. It is an Open-source project which is the provider of world-class information security training and penetration testing services. The Offensive Security also maintains the Oppressed Database.
The Kali Linux is the best open-source security packages of the ethical hacker, such that it contains the set of tools which is divided into categories. We can install the Kali Linux in every type of machine. It is the secure distribution of Linux, primarily designed for digital forensics and penetration testing.
The Kali Linux is an operating system, as well as a distribution of GNU / Linux. It was developed for some specific purposes. If we want to install Kali Linux, we will have an operating system pre-configured for the “penetration testing” to the general computer security use.
History of Kali Linux
The Kali Linux is the Security Distribution of Linux and was developed by the "Mati Aharoni," "Devon kearns” and "Raphael Hertzog."These developers develop the Kali Linux to the Offensive Security through the rewrite of Backtrack. The Backtrack was their previous information security operating system. The first iteration of Kali Linux was 1.0.0 developed in March 2013. The Offensive securities are currently funding and supporting the Kali Linux.
This operating system has 600 preinstalled testing applications to discover. Every program exists in Kali Linux with its unique Flexibility and use cases. It does an excellent job of separating those useful utilities.
Kali Linux Core Developers
“Mati Aharoni” is the lead developer of Kali Linux, trainer and founder of the offensive security. Mati Aharoni has ten years of experience as a professional penetration tester. “Aharoni” has uncovered several security flaws and actively involved in the offensive security arena.
“Devon Kearns” is an offensive security instructor, Kali Linux developer, the administrator of the Exploit database, co-creator of the “Metasploit unleashed project," exploitation Fanatic and co-author of Metasploit: The penetration tester’s guide.
“Raphael Hertzog” is the experienced Debian Developer and consultant, and author of the well-known Debian Administrator’s Handbook. He is also the packaging wizard in his team and manages the continuously growing development infrastructure.
Features of Kali Linux
Kali Linux is the full disk encryption and has the ability to perform the full disk encryption of the sensitive penetration testing. The computer drive is an essential feature needed in several industries. There are some unique features of Kali Linux, which are given below:
1. The Live system
The Kali Linux is the live system which contains the tools that are most commonly used by the penetration testers. This operating system is also used as the bootable live system.
In other words, we can say that the Kali Linux is used without installing at the machine, the user needs to boot the ISO image only for the use of this operating system. We need to copy the ISO image onto the USB key.
2. Forensics Mode of Kali Linux
If we are doing any forensic work on the computer system, so we need to ignore any activity that would alter data on the analyzed system in any way. The modern desktop environment is interfering with this objective by trying to automount any disk which they detect.
To avoid this behavior, Kali Linux has the forensic mode that can be enabled from the boot menu. The forensic mode disables all such features. The live system is useful for forensic purposes. Just because it is possible to reboot any computer system into the Kali Linux system without accessing or modifying its hard disks.
3. The Custom Linux Kernel
Kali Linux always provides the customized recent Linux Kernel which, is based on the version in Debian unstable. This feature ensures solid hardware support, especially for the wide range of wireless devices.
This Linux kernel is patched for wireless injection support since some wireless security assessment tools rely on this feature. Many hardware devices require up-to-date firmware files, and Kali installs them by default, including the firmware available in Debian's non-free section.
4. Completely customizable
Kali Linux is a completely customizable operating system for security purposes. The penetration testers build it. It always ensures that the Kali Linux is easy to customize based operating system for the user's needs and preferences.
The user can publish the live-build configuration, which is used to build the official kali images so the user can customize it according to the user's liking. It is very simple to start from this published configuration and implement several changes as per the user’s requirement.
5. The Trustable Operating System
The Kali Linux is a trustable operating system developed in plain sight that allows the user to inspect the source code. This operating system is developed by a small team of knowledgeable developers, working transparently, and following the best security practices. They can upload signed source packages that are built on the daemons.
The work done on these packages can be fully reviewed through the packaging Git repositories, which are used to build Kali source packages. The evolution of every package can also be followed through the Kali package tracker.
6. Usable on the wide range of ARM (Advanced RISC Machine) devices
The Kali Linux provides the binary packages for the armel, armhf and arm64 ARM architectures. These are easily installable images provided by Offensive Security. The Kali Linux can be developed on many types of interesting devices.
Who uses Kali Linux and Why
The Kali Linux is a unique operating system, and both good guys and bad guys use this platform. The Security administrators and black hat hackers both use this operating system for various tasks. One is used to detect and prevent security breaches, and the other is used to identify and possibly exploit security breaches.
Professional Users of Kali Linux
There are several users of Kali Linux, which are described below:
1. Security Administrators
The security administrators are responsible for safeguarding the information and data of their institutions. These administrators use the Kali Linux to review their environments and ensure that there is not any easily discoverable vulnerability.
2. Network Administrators
They are responsible for maintaining an efficient and secure network. The Network administrators are using Kali Linux to audit their network. Kali Linux can detect rogue access points.
3. Network Architects
Network Architects are responsible for designing secure network environments. They also utilize the Kali Linux to audit their initial designs and ensure that nothing was overlooked or misconfigured.
4. Pen Testers
These testers can utilize Kali Linux to audit the environments ad performance investigation in corporate environments. They have been hired to review all this work.
5. CISO (Chief Information Security Officers)
The Chief Information Security Officer is also using the Kali Linux to audit their environment internally. It is also discovered if any new application or rogue configuration has been put in that place.
6. Forensic Engineers
The Kali Linux has a “Forensic Mode," which allows the forensic engineers to perform the data discovery and recover in some instances.
7. White Hat Hackers
The white hat hackers are like pen testers, and these testers use Kali Linux to audit and discover vulnerabilities that may be present in the environment. The white hat hackers are the computer security specialist, who can break the security of any protected system and networks for testing purpose.
These types of hackers use their skills to improve security by exposing vulnerabilities before malicious hackers can detect and exploit them. The white hat hackers have specialization in penetration testing and in other testing methodologies, which ensure the security of an organization's information system. These white hat hackers are also known as ethical hackers.
8. Black Hat Hackers
The Black hat hackers utilize the Kali Linux to discover and exploit vulnerabilities. The kali Linux has social numerous engineer applications which are utilized by the black hat hackers to compromise with any organization or individual.
These Black Hat Hackers violate computer security for personal gain or maliciousness. The Black Hat refers to those hackers who can break the security of the computer system or network with malicious intent.
They may exploit security vulnerability for money gain to steal or destroy the private data. The black hat hacking is the stereotypical illegal hacking group. They are illegally permitted to harm the individuals.
9. Grey Hat Hackers
The Grey hat hackers are lying in between the white hat and black hat hackers. These hackers are computer security experts who may sometimes violate laws or typical ethical standards but does not have the malicious intent of the black hat hacker.
10. Computer Enthusiasts
Computer Enthusiasts is a generic term if anyone can be interested in learning more about networking or computers, so Kali Linux is used for this purpose.
An Installation Guides to Kali Linux Step By Step
The installation of kali Linux is an easy process. First, the user needs compatible computer hardware. Kali Linux is supported by i386, amd64, and ARM platforms. Better hardware will naturally provide better performance. The i386 images have the default PAE Kernel so the user can run them only on the systems, which are over 4GB of RAM.
Download the Kali Linux and either burn the ISO to DVD or prepare the USB stick with the Kali Linux Live as the installation medium. If the user does not have the DVD drive or USB port on his computer system, then the user needs to check out the Kali Linux Network Installation.
Installation prerequisites
1. Minimum 20 GB disk space to install the Kali Linux.
2. The user needs a minimum of 1 GB RAM and recommended 2GB or more for the i386 and amd64 architectures.
3. CD-DVD Drive /USB boot support.
Preparation for the installation
1. Download the Kali Linux from its official website www.kali.org.
2. The user needs to Burn the Kali Linux ISO to DVD or Image Kali Linux Live to USB.
3. Ensure that the computer system is set to boot from the CD / USB into the user’s BIOS.
Steps for Installation Procedure
Step1. To start the installation of Kali Linux, boot with the installation medium, which chose by the user. Select the Graphical Install option according to the screenshot which is given below:
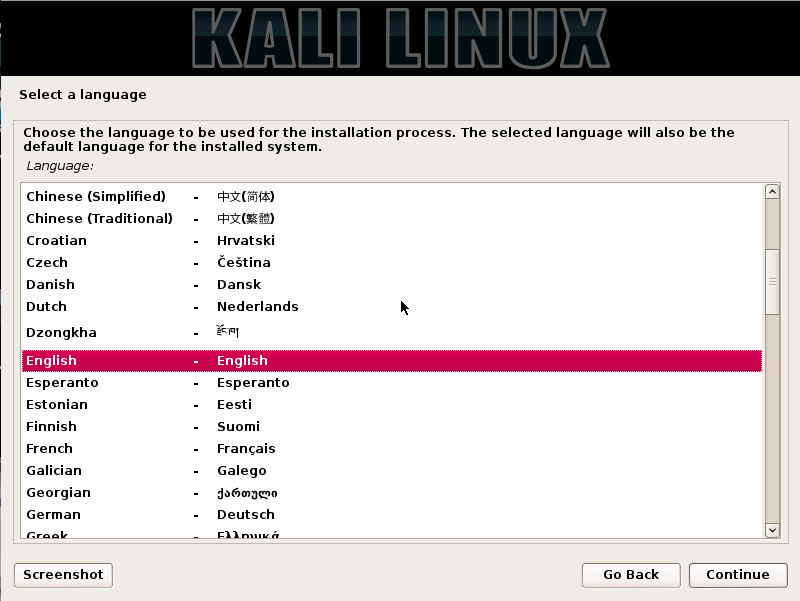
Step2. Select the preferred language and counter the location of the user and click on the continue button.
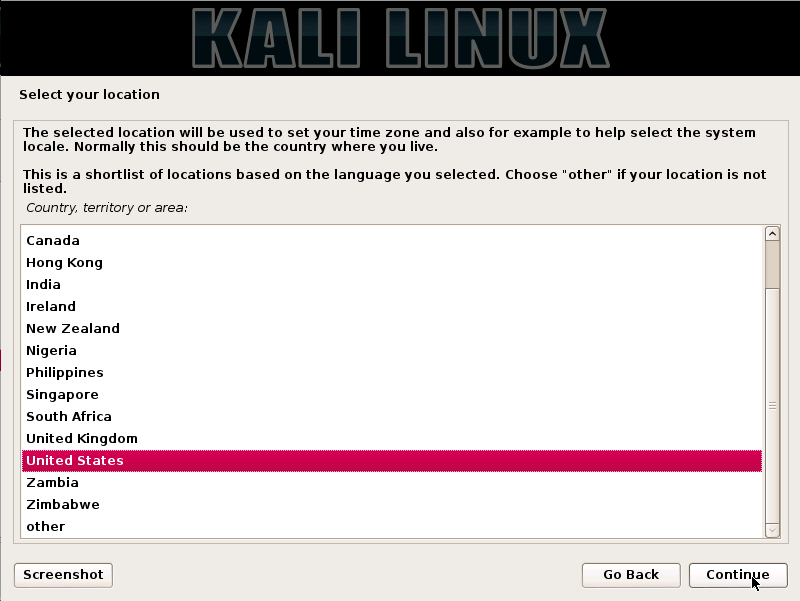
Step3. Specify the user’s geographical location and click on the continue option.
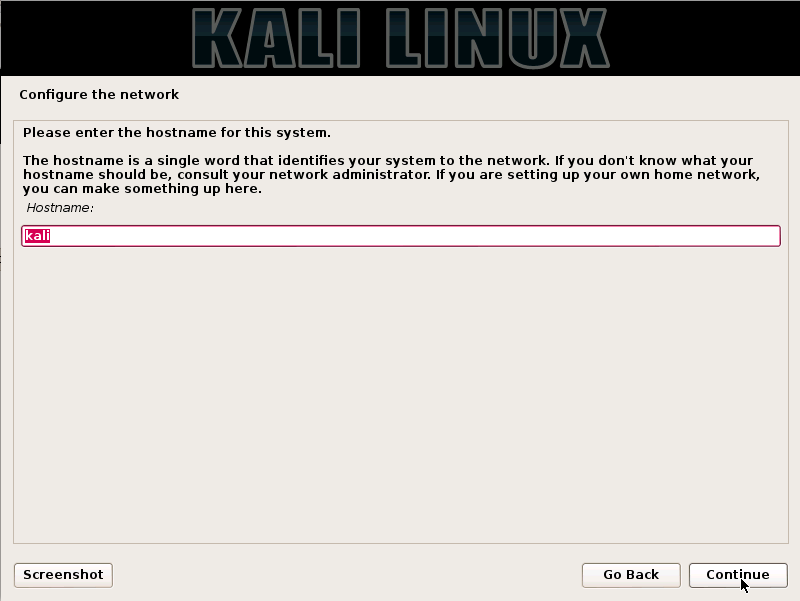
Step4. Enter the hostname for the user's system in the given option, in the screenshot given below we have entered "Kali" as the hostname and click on the Continue option.
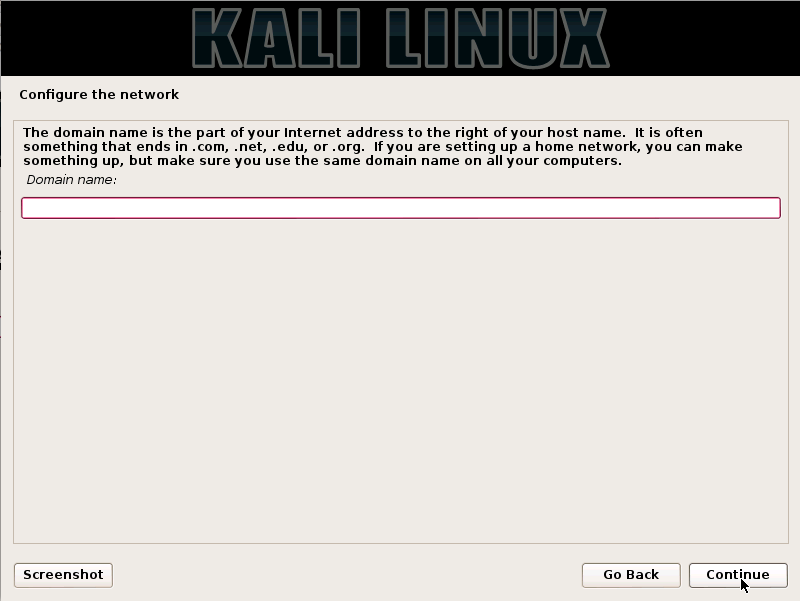
Step5. The user may optionally provide the default Domain name for the computer system to use and click on the continue button.
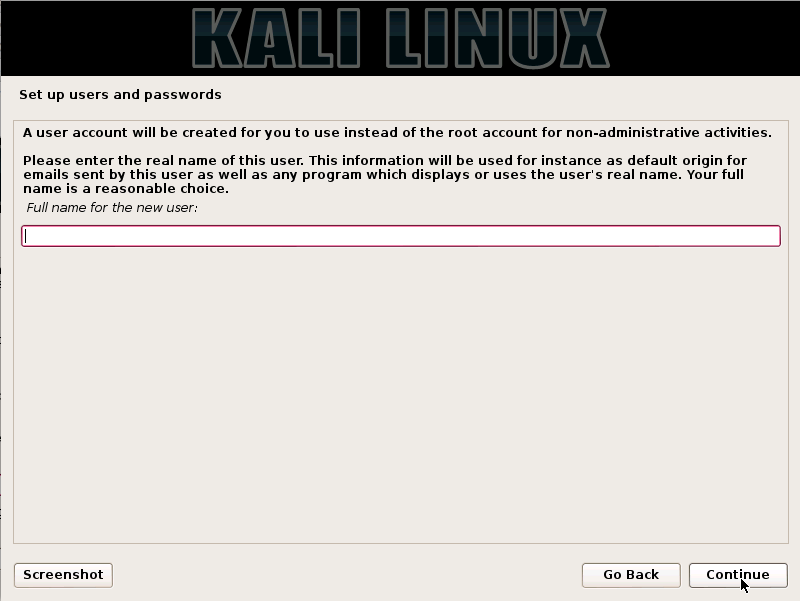
Step6. The user needs to provide the full name for the non-root user to the computer system and press the continue button.
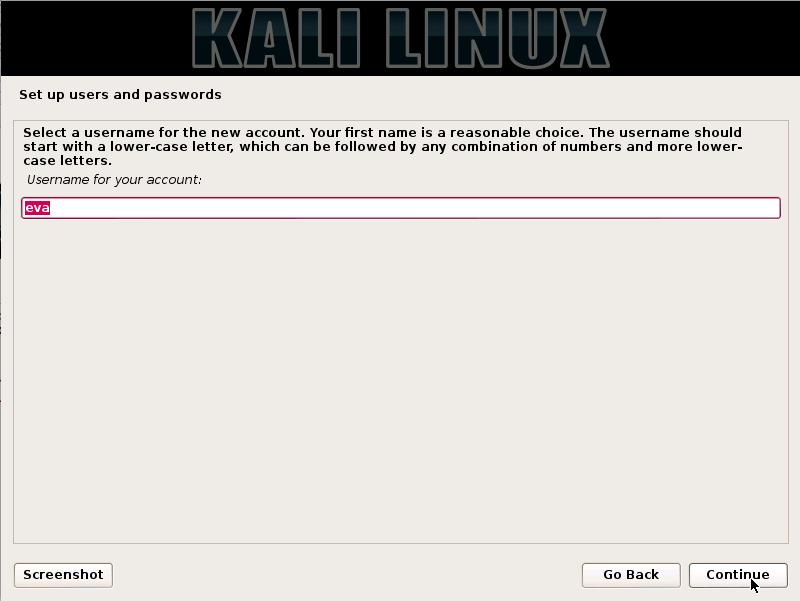
Step7. The Default user ID will be created, based on the full name provided by the user, also the user can change its name later on if wanted. And then, the user should click on the continue button.
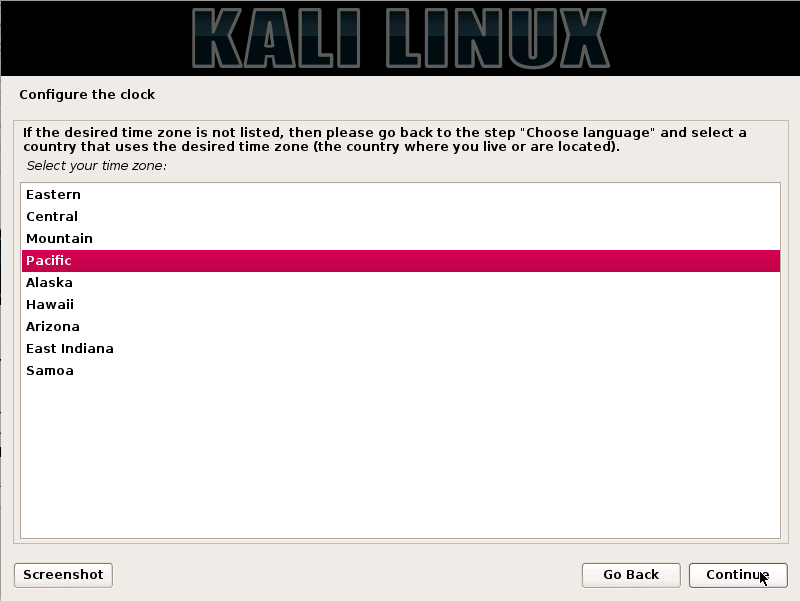
Step8. Set the time Zone in this Step and press on the continue option.
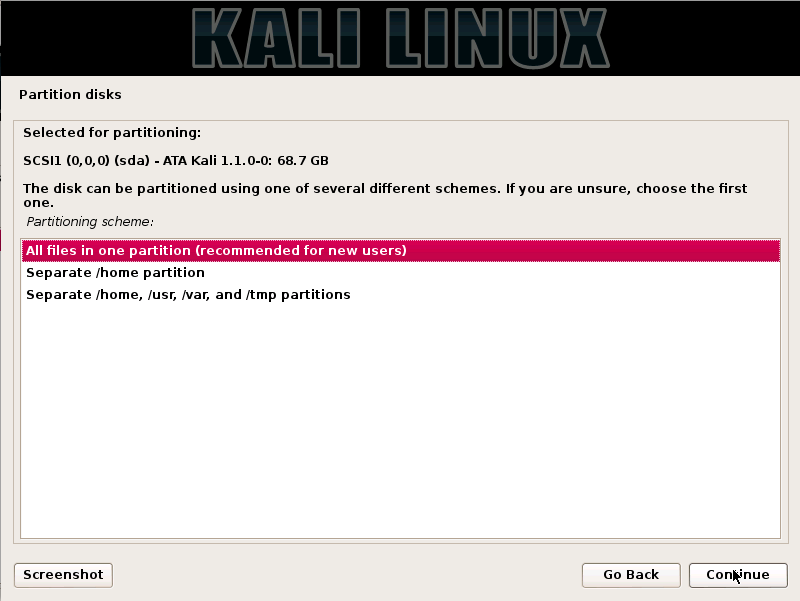
Step9. Select the option “guided –use the entire disk” and click on the continue button as given below in the screenshot:
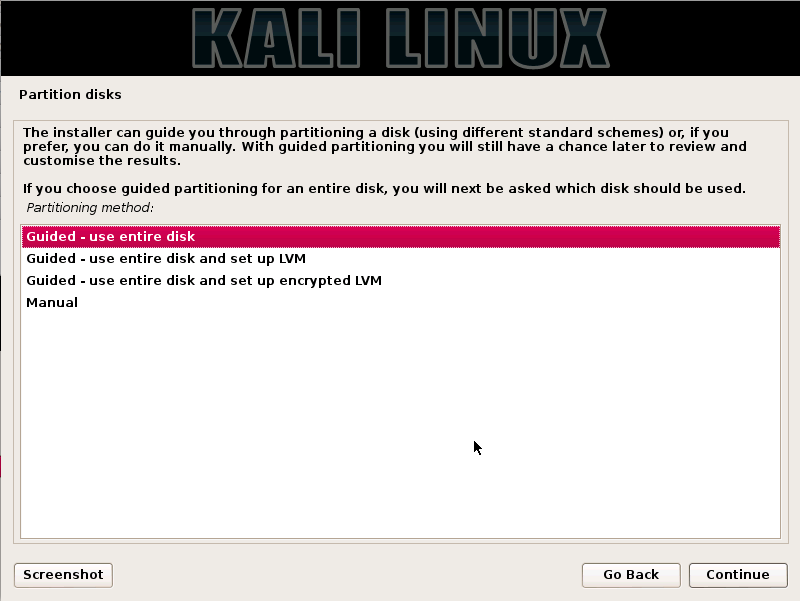
Step10. Select the disk to be partitioned in this Step and press the continue option.
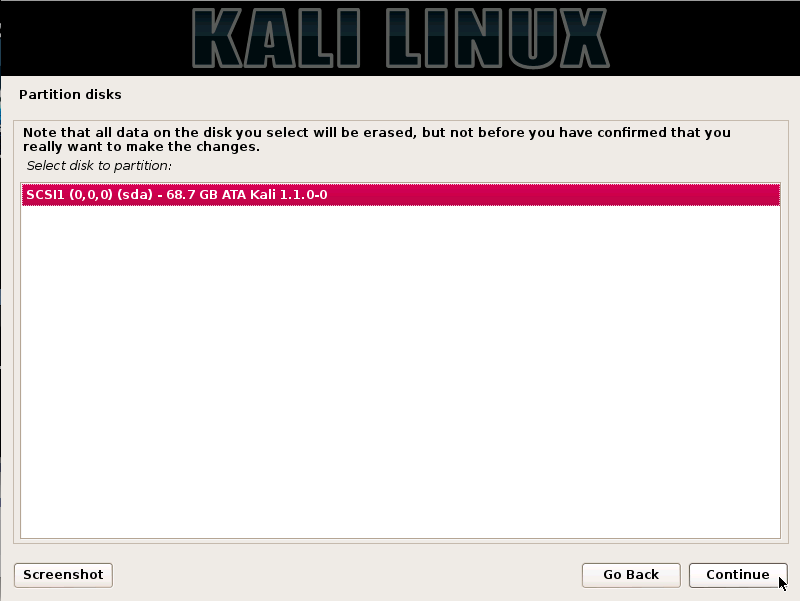
Step11. Depending on the user’s need, the user can choose to keep all the files in a single partition, and for that, the user should select the option "All the files in one partition" and click on the continue button.
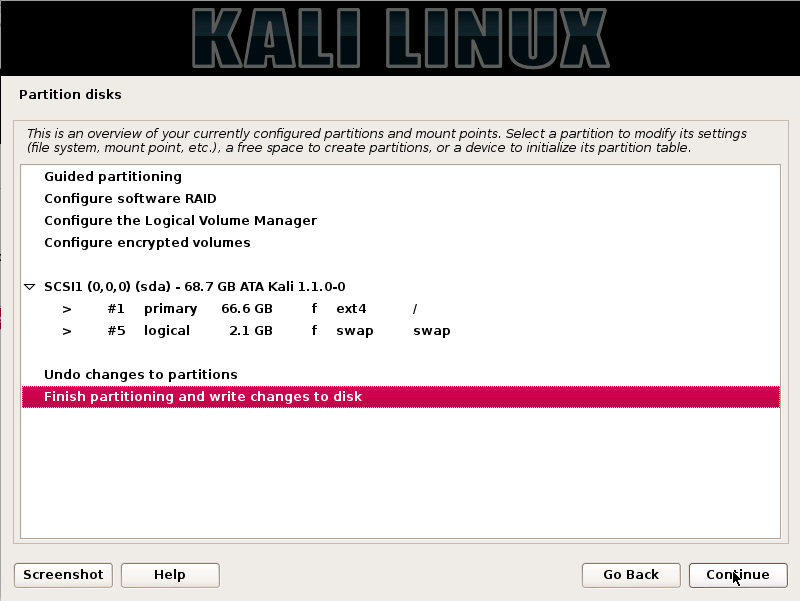
Step12. Press the continue button. The user has one last chance to review the disk configuration after a click on the continue button. The user will not be able to make any change.
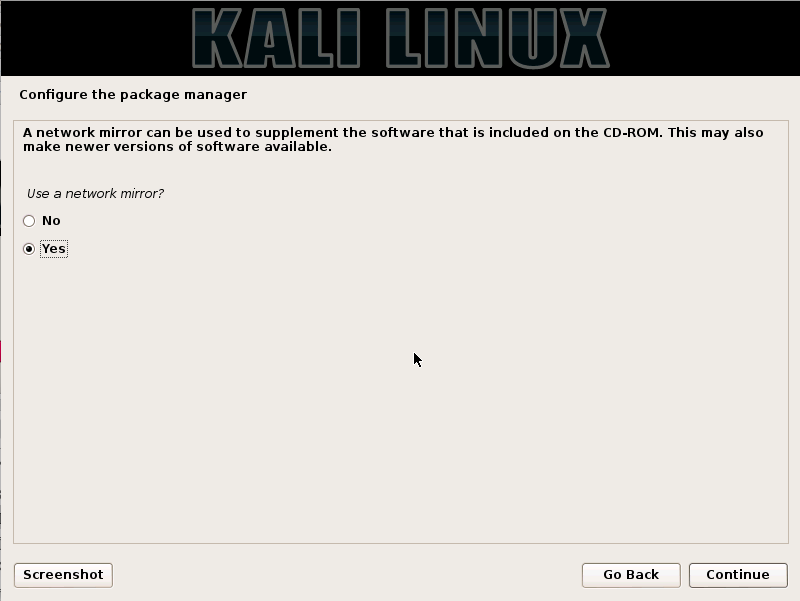
Step13. Click on the "Yes" option to configure the package manager and press the continue button.
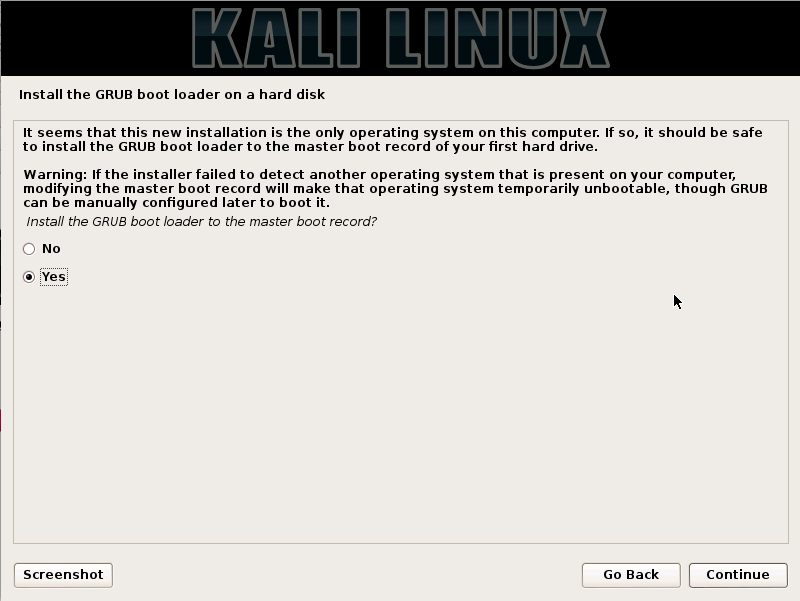
Step14. Click "yes" to install the GRUB boot loader on the hard disk.
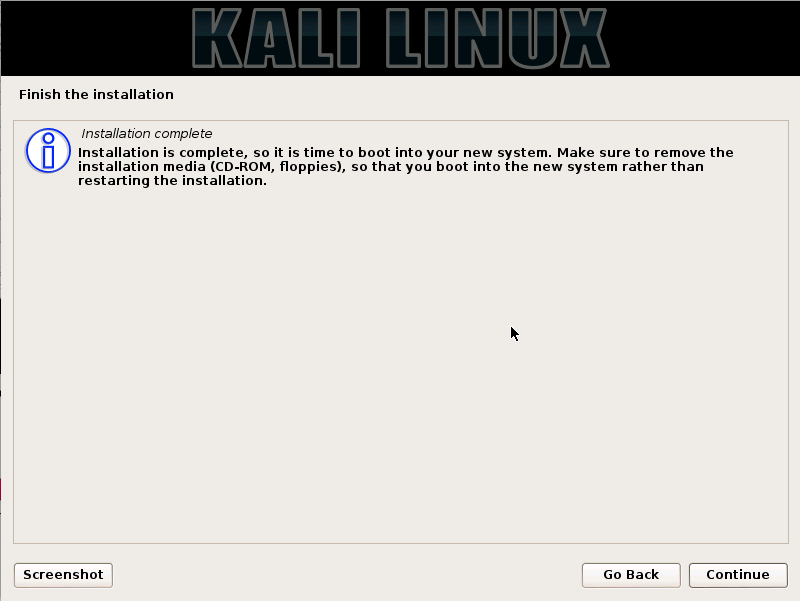
Step15. Installation is complete now, click on the continue button to reboot Kali installation.
Step16. End.
Advantages of Kali Linux
There are various advantages of Kali Linux that are given below:
1. The Kali Linux gives the most significant and best GUI (graphical user interface) platform for the Linux operators. It is a most custom modified version of Linux, which helps in Sniffing, cloning the web pages, Penetration of Wifi, receiving data packages, and lots of things that are related to the hacking and cracking.
2. It is easily available on the internet so the user can download the Kali Linux from its official website.
3. Kali Linux also provides the best security of data.
4. It is an open-source, and it does not dominate the market like windows.
Disadvantage of Kali Linux
- It is more difficult to find the applications which are supported Kali Linux as per the user's need; this is an issue mostly for business.
- The drivers in Kali Linux are the main issue, so before the installation of any hardware component in the computer system, make sure that the hardware has drivers available.
Vulnerability Analysis tools
There are some vulnerability analysis tools which can help us to exploit the devices or application to gain access. There are different types of Vulnerability analysis tools which are given below:
1. Cisco tools
Kali Linux has some tools which can be used to exploit the Cisco router. One such tool is Cisco-torch, which is used for mass scanning, fingerprinting, and exploitation.
Open the terminal console after clicking the left pane.
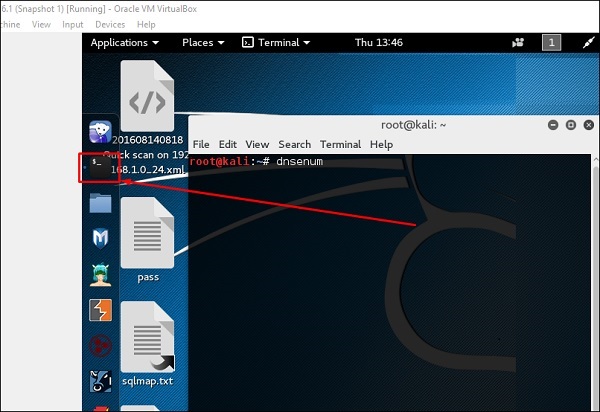
If there is nothing found to be exploited after typing the command "cisco-torch-parameter IP of the host," then the result will be shown as:
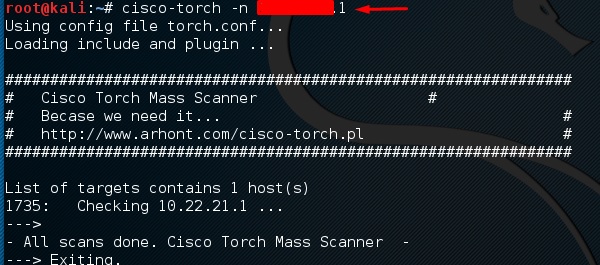
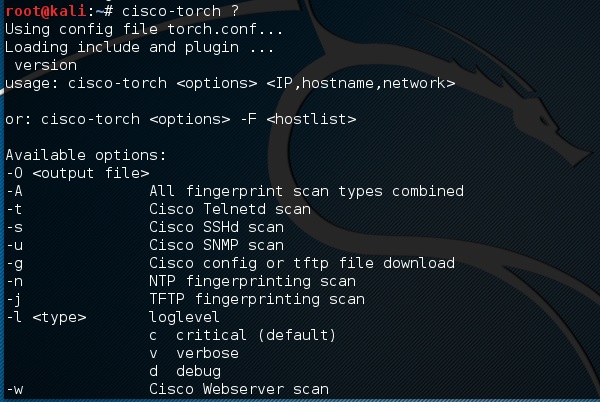
If the user wants to see what are the parameters that can be used, then type this command “cisco-torch?”
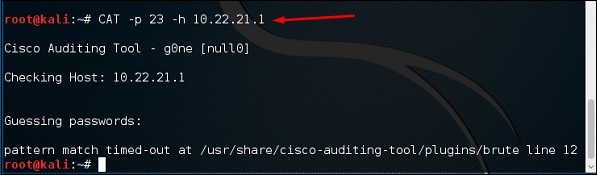
Cisco Auditing Tool
The Cisco auditing tool is a PERL script, which is used to scans routers for common vulnerabilities. To use this tool, we need to open the terminal again on the left pane, which is shown above, and type this command "CAT-h hostname or IP."
Now, the user can add the port parameter “-P” which is shown in the given screenshot.
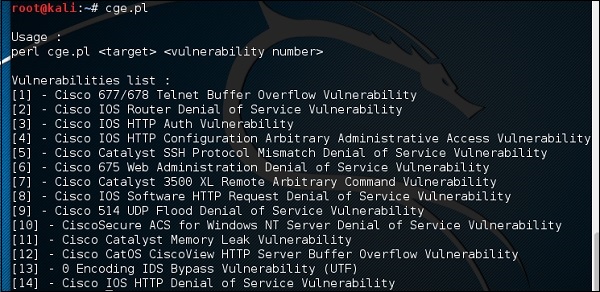
Cisco Global Exploiter
The Cisco Global exploiter is an advanced, simple, and fast security testing tool. The user can perform several types of attack with the help of this tool. The option [2] in the given screenshot is used to stop the services.
Information Gathering tools
Kali Linux penetration testing platform contains a vast array of tools and utilizes from the information-gathering tools to the final reporting. This reporting enables security and IT professionals to assess the security of their systems. There are various types of information gathering tools that exist in Kali Linux, which are given below:
1. NMAP and ZenMAP
The NMAP and ZenMAP are useful tools for the Scanning phase of Ethical hacking in the Kali Linux. These tools are practically the same; however, NMAP uses the command, while ZenMAP has the Graphical user interface.
The NMAP is the free utility tool for network discovery and security auditing. Several systems and network administrators also find this tool useful for different tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. This NMAP tool uses raw IP packets to determine the hosts which are available on the network.
2. Stealth Scan
The Stealth Scan or SYN is also called a half-open scan. The hacker sends an SYN packer to the target. If the SYN/ACK frame received that packet back, then it is assumed that the target would complete connection, and the port is listening. If the RST received the packet back from the target, then it is assumed that the port is not active or closed.
3. Search sploit
The Search sploit is the tool that helps Kali Linux users to directly search with the command line from the exploit database collection.
4. DNS Tools
The user can learn in this section, how to use some DNS tools that Kali Linux has incorporated. These tools are mainly used for help in zone transfers or domain IP resolving issues.
5. LBD (Load Balancing Detector) Tools
The LBD (Load Balancing Detector) tools are very attractive because they can detect if the given domain uses DNS or HTTP load balancing. This tool is important because if the user has two servers, and both servers may not be updated, and the user wants to exploit it. There is not any issue to the user, and he can easily exploit.
6. Hping3
This tool is widely used by Ethical hackers. The Hping3 is nearly similar to ping tools, but it is more advanced, as it can bypass the firewall filter and use TCP, UDP, ICMP, and RAW-IP protocols. It has the traceroute mode and the ability to send files between the covered channels.
Website Penetration testing
The sqlmap is an open-source penetration testing tool that automates the process of detecting and exploiting the SQL injection flaws and taking over the database servers. The Vega usage is also the free and open-source scanner for the testing to test the security of web applications.
It can help the user to find and validate the SQL injection, cross-site scripting inadvertently disclosed sensitive information and other vulnerabilities. It is written in java, Graphical user interface based, and run on the Linux and windows.
Wireless Attacks
The Kali Linux contains various types of wireless attack tools which are used for the wifi hacking. There are top ten wifi hacking tools which are given below:
- Aircrack-ng
- Reaver
- Pixiewps
- Wifite
- Wireshark
- oclHashcat
- Fern Wifi Cracker
- Wash
- Crunch
- Maccchanger
Sniffing and spoofing
Spoofing and sniffing are types of cyberattacks. Spoofing means to pretend to be someone else, and sniffing means illegally listen to another's conversation. The Sniffing tool is as simple as the wiretapping. There are several types of sniffing and spoofing tools are available in Kali Linux, which is given below:
- Burpsuite tool
- Mitmproxy
- Wireshark
- Sslstrip
Exploitation tools
There are various types of exploitation tools which exist in Kali Linux:
- Metasploit
- Armitage
- BeEF
- Linux Exploit suggester
Reverse Engineering
There are some essential tools which are used to perform reverse engineering in Kali Linux, which are given below:
- OllyDbg
- Dex2jar
- jd-gui
- apktool
Reporting tools
The Metagoofil is an information-gathering tool that is designed to extract the metadata of public documents that belongs to the target company. This tool is part of the reporting tool under the Kali Linux framework. There are various types of reporting tools are existed, and some important tools are given below:
- Dradis
- Metagoofil
- magictree
Conclusion
Kali Linux is a convenient package of security and forensic tools. It is distributed and aimed at advanced penetration testing and security auditing framework. The Kali Linux is developed, funded, and maintained by offensive security, which is leading the information security company.