Data Security Requirements in DBMS
Database security is a critical component of modern business and technology. As companies continue to collect, handle, and store massive amounts of data, the risk of an information breach or cyber attack grows. A data breach can result in financial damages, reputational harm, and legal ramifications. As a result, it's critical to put in place robust database security measures to secure sensitive data while also maintaining its integrity and confidentiality. In this article, we will go over some best practices for keeping our database safe, as well as the many aspects of database security.
Because the information held in a database is a very valuable and, at times, quite sensitive commodity, security is a significant concern in database administration. As a result, the data in a system for managing databases must be safeguarded from misuse and illegal access and modifications. Although most security breaches are caused by hackers, insiders account for 80% of data loss.
Importance of Data Security in Database Environment
Security of databases is the protection of a database against both deliberate and inadvertent dangers, which might be computer-based or not. Database security is a duty for the whole company since all individuals rely on the data stored in the organization's database, and any corruption or loss of data would have an impact on the organization's day-to-day operations and people's performance. As a result, database security involves the organization's hardware, software, infrastructure, people, and data.
As the volume of data kept in corporate databases grows and individuals rely increasingly on company information for making choices, client management, supply chain management, and so on, there is a higher focus on security of databases than in the past. Any loss or availability of business data would cripple today's corporation and have a negative impact on its performance. Now, even a few minutes of database downtime might result in significant costs for the firm.
Data Security Threats
We've observed that database security is a top priority for the whole firm. From a database security standpoint, the company should identify all potential hazards and weak aspects and devise methods to fight and eliminate each such threat.
A threat is any condition, event, or person that will have a negative impact on the security of databases and the organization's smooth and efficient operation. A danger might arise from a situation or occurrence involving a person, activity, or condition that is likely to harm the organization. The harm may be concrete, such as data loss, hardware damage, or software loss, or intangible, such as loss of consumer goodwill or credibility, and so on.
Tampering with Data
Communication privacy is critical to ensuring that information cannot be manipulated or seen while in transit. Data manipulation is more likely in dispersed setups since data flows across locations. An unauthorized person on a network intercepts information while it is transit and modifies it before re-transmitting it in a data manipulation attack. Raising the amount of an investment from one thousand rupees to Rs. 10000 is an example of this.
Theft of Data
Data must be securely kept and sent so that sensitive information, such as numbers for credit cards, cannot be stolen. Both public carriers or private network owners frequently route parts of their networks across the web and Wide Area Network (WAN) settings via unsecured landlines, severely sensitive microwave and satellite connections, or a number of servers. This circumstance exposes vital data to any interested party. Insiders having physical access to the wiring in LAN settings within a structure or campus may be able to read data that is not meant for them.
Creating false user identities
In a dispersed system, it is easier for a user to forge an identity in order to obtain access to delicate and critical information. Criminals try to steal consumers' credit card credentials and then use them to make transactions on their accounts. Or they take other people's personal information, such as financial account information and driver's license numbers, and open fraudulent credit accounts in their place.
Password-Related Dangers
Users in big systems must remember many passwords for the various programs and services they utilize. Users generally respond to the issue of managing several passwords in one of three ways:
They may use a password that is simple to guess. They may also want to standardize credentials so that these are consistent across all workstations or websites.
All of these methods jeopardize password confidentiality and service availability. Furthermore, managing many passwords and user accounts is difficult, time-consuming, and costly.
Tables and Columns unauthorized Access
A database may contain secret tables or confidential columns within tables that should not be accessible to all users who are authorized to view the database. Data protection at the column level should be possible.
Unauthorized Data Row Access
Some data rows may include private data that ought not to be made visible to all people with access to the database. In a shared environment, for example, companies should only have access to their own data, and customers should only be able to see their own orders.
Lack of Accountability
Users won't be held accountable for their conduct if the system's admin is unable to trace their activity. There has to be some trustworthy way to track who is doing what with the data.
Requirements for Complex User Management
Because systems must frequently handle a high number of users, they have to be scalable.
The effort of handling passwords and user accounts in such large-scale setups renders the system vulnerable to mistake and attack.
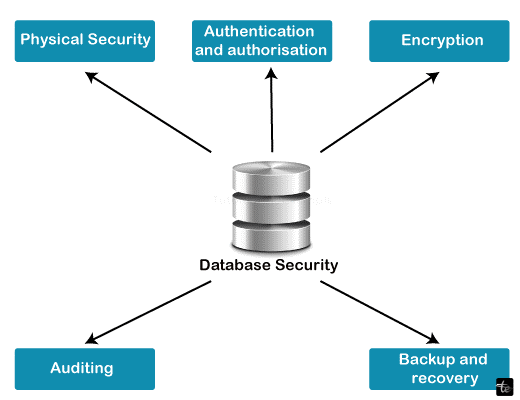
Levels of Security
To safeguard the information in the database, you must implement security measures at many levels:
- Physical: The locations of computer equipment must be guarded against armed or covert entrance by attackers.
- Human: Humans must be carefully approved to reduce the possibility of any such user providing access to an invader in return for payment or other benefits.
- Operating System: Regardless of how secure a database's system is, flaws in the security of the operating system can allow unauthorized entry to the database.
- Network: Because practically all databases allow access from afar via terminals or systems, software-level security inside network software is as critical as physical safety, both on the World Wide Web and in workplace networks.
- Database System: Many data-system users may be granted access to only a subset of the database. Others may be permitted to perform queries but not edit the data. It is the database system's job to guarantee that these authorization limitations are not breached.
If database security needs to be secured, security at all levels must be maintained. A flaw at the lowest possible level of safety (physical or human) permits rigorous high level (database) safety precautions to be circumvented.