Types of files in OS
Introduction
An operating system employs a file system to store, arrange, and control directories and files on a storage medium. Several typical file system types are as follows:
- FAT (File Allocation Table): Windows and other operating systems from earlier eras used the outdated file system known as FAT (File Allocation Table).
- NTFS (New Technology File System): Windows uses the New Technology File System (NTFS), a contemporary file system. Features like encryption, compression, and file and folder permissions are supported.
- ext (Extended File System): The Extended File System (ext) is frequently found on operating systems based on Linux and Unix.
- HFS (Hierarchical File System): MacOS uses a HFS (Hierarchical File System) file system.
- APFS (Apple File System): Apple started a new file system for both iOS and Mac computers.
A file is an assortment of connected data stored on secondary storage media. A group of logically connected items is called file. As far as the user is concerned, a file is the smallest possible allocation of logical secondary storage.
The file name is split into two parts, as indicated below: name and extension, separated by a period.
Objectives of File management System
The following are the primary goals of file management system:
- It supports a range of storage devices in terms of I/O.
- It reduces the possibility of corrupted or lost data.
- It aids in the OS's standardization of I/O interface procedures for user programs.
- In the context of a multiuser system, it supports numerous users' I/O needs.
File Structure
An operating system-understandable predetermined format is required for a file structure. Its unique structure is determined by its classification.
OS files are categorized into three types:
- Text file: It is a line-by-line arrangement of characters.
- Object file: An object file is a block-organized collection of bytes.
- Source file: It is a collection of procedures and operations.
Functions of File
- Create a file, locate available disc space, and add something to the directory.
- Write to file; needs to be positioned inside the file
- It requires a location within the file to read from it.
- Reclaim disc space by deleting the directory entry.
- Adjust and shift the read/write position.
Types of files
The system can recognize the three sorts of files: special, directory, and regular. The operating system, however, makes extensive use of these fundamental kinds.
There are the following fundamental file types:
| Item | Description |
| regular | It stores data (text, binary, and executable). |
| directory | It contains information used to access other files. |
| special | It defines a FIFO (first-in, first-out) pipe file or a physical device. |
Each file type the system can recognize belongs to one of these groups. The operating system, however, makes extensive use of these fundamental kinds.
Regular files
Regular files are the most often used file type used to hold data. Text files and binary files are examples of regular files.
Text files
Text files are standard files that may be viewed by the user and hold data in ASCII format. These files are printable and displayable. A text file's lines cannot have NUL characters, and none not even the newline character may be longer than {LINE_MAX} bytes.
The term text file does not prohibit control and other nonprintable characters (apart from NUL). As a result, most programs that list text files as inputs or outputs can either handle unusual characters or note their limits clearly in the relevant parts.
Binary files
Binary files are just regular files with computer-readable data inside of them. Binary files can also be executable files that give instructions to the system on how to perform a task. Programs and commands are kept in binary, executable files. Binary code is created from ASCII text using specialized compilation software.
The main difference between text and binary files is that text files have lines that are fewer than {LINE_MAX} bytes long, without NUL characters, and always end with a newline character.
Directory files
Although they don't hold the actual file contents, directory files do hold the information the system needs to access all file kinds. Directories offer the file system structure flexibility and depth while taking up less space than a typical file. Each directory entry represents a file or a subdirectory. The file name and the index node reference number (inode number) are contained in each entry. The inode number indicates the file's unique index node. The inode number indicates the location of the file's associated data. A different set of instructions creates and manages directories.
Special files
Special files are temporary files produced by processes, or they define devices for the system. Block, character, and FIFO (first-in, first-out) are the three fundamental categories of special files. Pipes are another name for FIFO files. Processes can temporarily communicate with one another by creating pipes. Following the completion of the initial operation, these files disappear. Devices are defined by character and block files.
Each file has a set of permissions, also known as access modes, which control who can open, edit, and run the file.
File Access Methods
The procedure that controls how files are viewed and read into memory is known as file access. Operating systems typically only support one access method at a time. Nevertheless, some operating systems allow for more than one type of access.
There are three ways to access files:
- Sequential access
- Direct random access
- Index sequential access
Sequential Access
This file access technique allows records to be accessed in a predetermined order. The sequential access approach likewise processes the file's contents one at a time. Most compilers use this access mechanism to access files.
Random Access
Direct random access is another name for the technique. The record can be directly accessed using this approach. Every record has a unique address that may be accessed for direct reading and writing.
Sequential Access
The foundation of this kind of accessing technique is basic sequential access. With this type of access, an index, including a direct pointer to various memory blocks, is constructed for each file. Using this method, the file can be accessed directly from the index pointer, which is searched sequentially. Greater access efficiency can be achieved by utilizing multiple levels of indexing. It also reduces how long it takes to access a single record.
Issues Handled By File System
There are numerous data structures that we have seen where the file may be stored. The primary responsibility of the file system is to maintain optimal file organization.
A free space is produced every time a file is removed from the hard drive. Many of these spaces might need to be recovered to reallocate them to other files. The primary problem with files is deciding where to store them on the hard drive; a block can be used to store a file. It could be stored in non-contiguous blocks on the disc. Every block where the files are partially located needs to be monitored.
Files Attributes and Their Operations
| Attributes | Types | Operations |
| Name | Doc | Create |
| Type | Exe | Open |
| Size | Jpg | Read |
| Creation Data | Xis | Write |
| Author | C | Append |
| Last Modified | Java | Truncate |
| protection | class | Delete |
| File type | Usual extension | Function |
| Executable | exe, com, bin | Read to run machine language program |
| Object | obj, o | Compiled, machine language not linked |
| Source Code | C, java, pas, asm, a | Source code in various languages |
| Batch | bat, sh | Commands to the command interpreter |
| Text | txt, doc | Textual data, documents |
| Word Processor | wp, tex, rrf, doc | Various word processor formats |
| Archive | arc, zip, tar | Related files grouped into one compressed file |
| Multimedia | mpeg, mov, rm | For containing audio/video information |
| Markup | xml, html, tex | It is the textual data and documents |
| Library | lib, a ,so, dll | It contains libraries of routines for programmers |
| Print or View | gif, pdf, jpg | It is a format for printing or viewing an ASCII or binary file. |
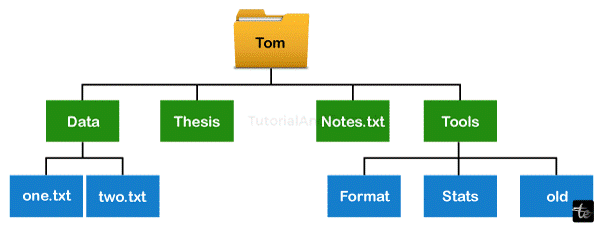
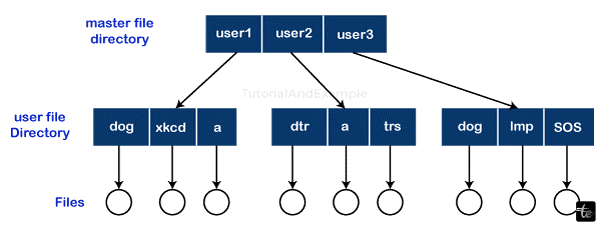
File Directories
An arrangement of files is called a file directory. Details about the files, such as their location, ownership, and attributes, are contained in the directory. The operating system is in charge of a lot of this data, particularly that related to storage. Several file management procedures can access the directory, a file in and of itself.
Below are information contained in a device directory:
- Name
- Type
- Address
- Current length
- Maximum length
- Date last accessed
- Date last updated
- Owner id
- Protection information
The operations performed on the directory are as follows:
- Search for a file
- Create a file
- Delete a file
- List a directory
- Rename a file
- Traverse the file system
Advantages of File System
- Organization: Files can be arranged into directories and subdirectories using a file system, which facilitates file management and location.
- Data protection: To guard against data loss or corruption, file systems frequently come with features like backup and restore, file and folder permissions, and error detection and correction.
- Better performance: A well-designed file system can enhance the speed at which data is read and written by effectively arranging data on the disc.
Disadvantages of File System
- Compatibility problems: Data transfer across other operating systems might be challenging due to incompatibilities between file systems.
- Overhead: File systems may utilize a portion of their disc capacity to hold overhead data, metadata, and other information, which takes up space that could be used for user data.
- Vulnerability: File systems are susceptible to viruses, data corruption, and other security risks that could jeopardize the system's stability and security.