Operating System Layers
Many structures can be used to implement the operating system. How the different operating system's common parts are connected and integrated into the kernel largely determines how the OS is structured. In light of this, we must adhere to the operating system's architecture.
The operating system is divided into levels using the layered structure concept, giving the system administrator far more control. The hardware is located at layer 0's bottom, while the user interface is at layer N's top. Each of these levels solely utilizes the features of the lower-level layers due to how they are constructed. It streamlines the debugging process by simulating the troubleshooting of lower-level layers with an error. Since the lower-level layers have previously undergone debugging, the issue can only be on that layer.
What an operating system with layers is:
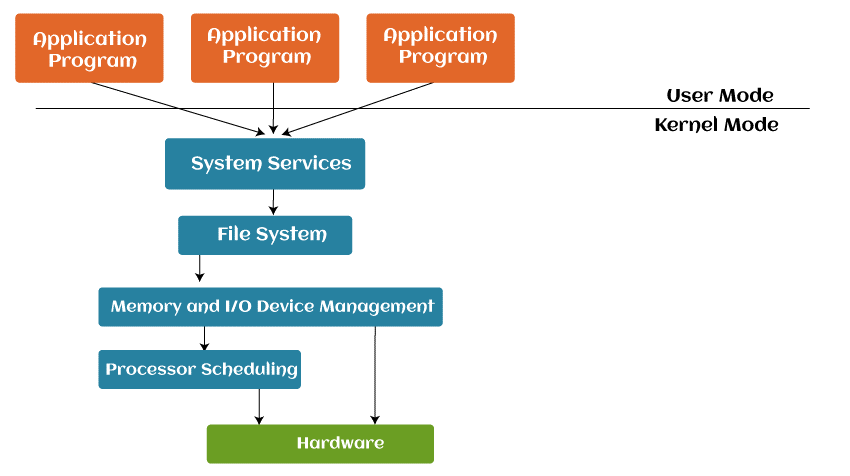
A layered operating system uses several layers to manage user applications and system software. The lower levels handle core system software, while the upper layers deal with application software. Only the layer above or below a given layer can communicate with that layer.
Only the layers above and below each other in the operating system may interact. The top layer handles the user applications, while the lowest layer governs the hardware.
The various operating system functions are divided into layers in a layered structure, each responsible for a clearly defined job. It was developed to enhance previously established frameworks such as the Monolithic (UNIX) and the Simple (MS-DOS) frameworks.
There were two sorts of systems existing before the layered structure:
- Monolithic building (UNIX)
- Easy structure (MS-DOS)
Examples of an operating system with layers:
- Windows NT as a working environment
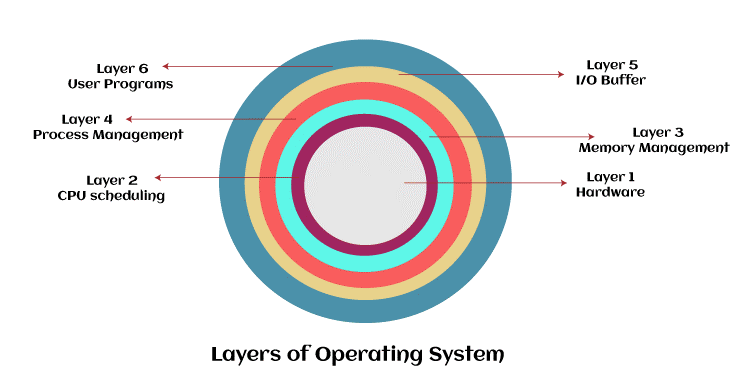
Layered Structure Design of operating system
The early monolithic systems were replaced with this kind of operating system. The layered operating system is divided into numerous levels, each with unique capabilities. The following are some guidelines for implementing the levels.
- A layer can access all layers below it, but it cannot access those layers. Layer n-1 can reach all levels from n-2 to 0 but cannot access layer n.
- Layer 0 is responsible for assigning processes and moving between them when there are delays or when the timer runs out. It also covers the CPU's fundamental multiprogramming.
Therefore, the answer will pass through all the layers from n-1 to 1 if the user layer wishes to communicate with the hardware layer. The implementation and planning of each layer must be done only to require the services offered by the levels below it.
Design Analysis:
The picture shows that the entire operating system is divided into levels ranging from 0 to n. Each component needs to fulfill a particular task that is unique to it. The following are some guidelines for implementing the levels.
- The User Experience component must be the topmost layer.
- The hardware component must be the deepest layer.
A specific layer can access every layer beneath it, but it cannot access the layers above it. In other words, layer n-1 can reach all levels from n-2 to 0 but not layer n.
The operating system's layers
The levels of an operating system are listed below:
Process management layer:
This layer handles processes, including how many functions will remain in the waiting timetable and which method will be performed next. In this layer, the operations' priorities are also handled.
This layer handles the processes, which include choosing how many functions will remain in the waiting plan and allocating the CPU to each method. In this layer, the operations' priorities are also handled. First-come, first-served (FCFS), SJF (shortest task first), priority scheduling, round-robin scheduling, and others are some of the various algorithms used for process scheduling.
Personal programs layer:
This layer is connected to applications used by users, such as Microsoft Word, Google Chrome, calculators, music players, etc. This stratum oversees the management of all projects. Given that it is focused on application programs, you could also refer to this as an application layer.
In the tiered operating system, this layer is the topmost. Word editors, sports, browsers, and other user programs and apps that are active within an operating system are handled by this layer. Given that it is focused on application programs, you could also refer to this as an application layer.
CPU scheduling layer:
This layer manages all CPU (central processing unit) scheduling. This component controls the number of tasks that will be assigned to the CPU and the number that will be kept outside of the CPU.
This tier handles the CPU task scheduling. To manage operations, many scheduling lines are employed. The processes are added to the work queue when they reach the system.
The ready queue is used to store programs that are prepared to run in primary memory. This layer controls how many tasks will be assigned to the Processor and which ones will not.
Memory management layer:
This layer is responsible for all aspects of memory administration. As you know, a computer has many different kinds of storage, including RAM and ROM. When RAM (random access memory) is used, memory moving in and out is problematic. When our computer operates, some tasks are transferred to the main memory (RAM) for processing. When applications (such as the calculator) are closed, they are removed from the main memory. This stratum is responsible for managing such activities.
Memory and process transfer from disc to main memory for processing and return are handled in memory management. The third component of the operating system is in charge of managing this. The entire memory management system is connected to this component. The computer has a variety of storage, including RAM and ROM.
If that makes sense, RAM is involved with moving in and out of memory. When our computer operates, some tasks are transferred to the main memory (RAM) for processing. When applications, like the calculator, are closed, they are also deleted from the main memory.
I/O buffer layer:
Assume you are using a computer to type. A keyboard buffer that is connected to the keypad temporarily saves data. In a similar vein, every input/output device has a cache of some kind attached to it. This is due to the sluggish working and storing speeds of the input/output devices. The computer uses buffers to keep the proper timing pace of the CPU and input/output devices. In this stratum, the pads are handled.
I/O hardware plays a crucial role in computer networks. They offer customers ways to communicate with the machine. The I/O device caches are managed by this component, ensuring proper operation.
Let's say you are using a keypad to type. The keypad has a connected keyboard buffer, which temporarily saves data. Similarly, every input/output device has a cache connected to it. This is due to the working and storage speeds of the input/output devices. The computer uses buffers to keep the input/output devices and the Processor's excellent timing performance.
Hardware layer:
The computer can be connected to many devices, such as a keypad, mouse, printer, and scanner. The hardware layer controls these kinds of physical components. The hardware component has the most power and is immediately connected to the system's brain.
This layer integrates with all peripheral devices, including a printer, mouse, keypad, scanner, etc., and works with the system hardware. The hardware layer controls these kinds of physical components.
The hardware layer is the lowest and most powerful component in the layered operating system design. It is immediately connected to the system's brain.
Benefits of the layered operating system:
The layered framework of operating system architecture has several benefits, including:
- Modularity: This design encourages modularity because each component only performs assigned duties.
- Simple debugging: Because the levels are distinct, debugging is very simple. There needs to be a solution to the Processor scheduling mechanism. In contrast to the Monolithic system, where all the services are available, the coder can only explore that specific layer to debug.
- Simple update: Modifications made to one layer won't impact those made to subsequent levels.
- Hardware layer cannot be accessed directly: The hardware layer is the innermost component in the architecture. So, unlike the Simple system, where the user had direct access to the hardware, a user can use the services of hardware but cannot directly change or access it.
- Abstraction: Each component considers how it performs. Therefore, the other levels' methods and functions are abstract to it.
Drawbacks of the layered operating system:
Even though this system has several benefits over the monolithic and straightforward design, it also has some drawbacks, including:
- Complicated and meticulous implementation: Because a layer can access the services of levels below it, the layers' organization must be done with care. For instance, the backing store layer uses the memory management layer's functions. The memory control layer must be maintained below it—consequently, complicated execution results from massive modularity.
- Execution is slower: When two levels want to communicate, each layer asks to pass through every other layer that exists in between them. As a result, reaction times lengthen, in contrast to the Monolithic method, which is quicker in this regard. Therefore, adding more levels could result in more efficient construction.
- Functionality: Dividing the features is only sometimes feasible. They frequently interact with one another and cannot be divided.
- Communication: Non-adjacent levels cannot communicate with one another.