Data Link Control
Data Link Control
Data-link control is the main function of the data link layer. It deals with the configuration and coordination for connection between two neighboring nodes: node-to-node communication. The task of the data link layer includes error-control, software-implemented protocols, flow-control, and framing that provide efficient and smooth transmission of frames between nodes.
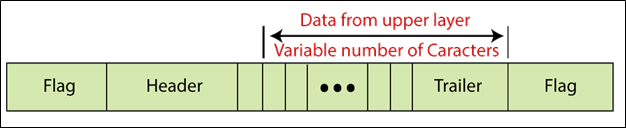
Framing
The data link layer separates the bit-stream obtained from the network layer into usable data units called frames.
Flow control
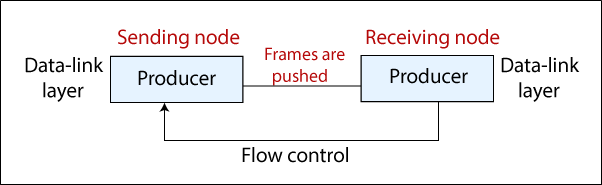
Flow control is one of the essential duties of the data link layer. It manages the amount of data that can be sent before obtaining confirmation. Flow control is a set of methods that tell the sender how much data it can transmit before the receiver is overloaded. Any receiving device has limited speed and limited memory for the process of incoming data and storage of the incoming data.
Error control
Error control includes both methods of error detection and error correction. The error control helps the receiver to notify the sender of any lost frames or damaged frames during the transmission. It allows to retransmission of those frames by the sender. At the data link layer, error control is often easily implemented: whenever an error is detected at the frames, those frames are re-transmitted.
Protocols
The protocols usually use one of the common programming languages to execute the software. Protocols are divided into two categories: Noiseless channel and Noisy channel. The diagram of protocols structure is shown below.
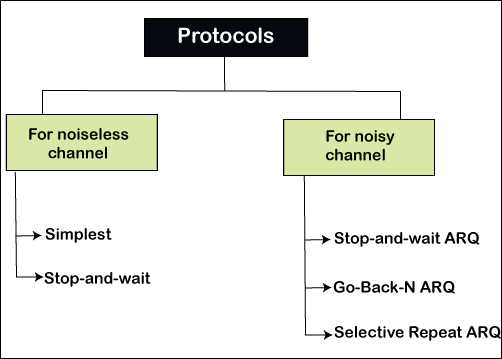
Noiseless channel
The noiseless channel is divided into two sub-categories: Simplest protocol and Stop-and-Wait protocol. The first protocol of this channel does not use flow control, but the second protocol uses flow control.
Simplest Protocol
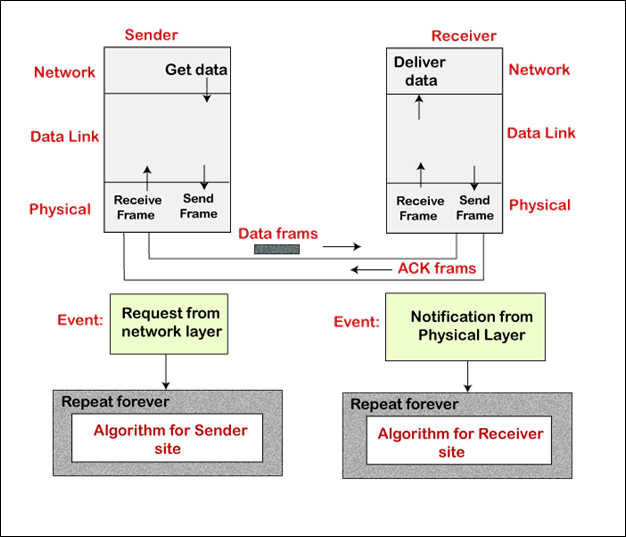
In this protocol, it doesn't use the flow and error control. It is a unidirectional protocol where data frames only travel from sender to receiver in one direction. The design of the simplest protocol with no flow control or error control is shown below.
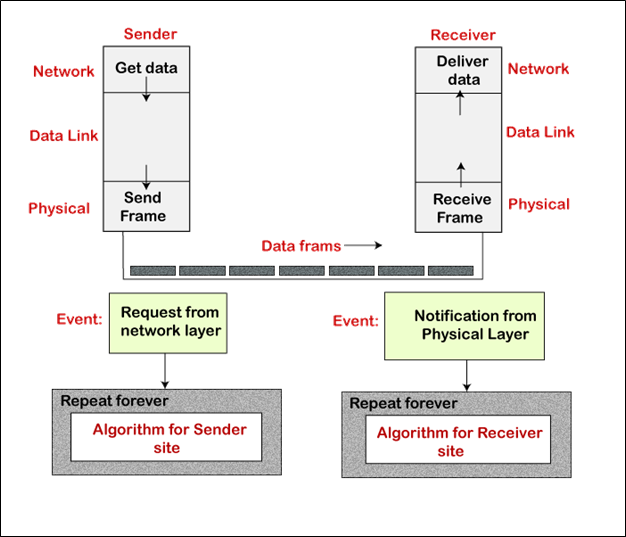
Algorithm
Sender-site algorithm for the simplest protocol
while(true) // Repeat forever
{
WaitForEvent(); // Sleep until an event occurs
If (Event (RequestToSend)) // There is a packet to send
{
GetData();
MakeFrame();
SendFrame(); // Send the frame}}
Receiver-site algorithm for the simplest protocol
while(true) // Repeat forever
{
WaitForEvent(); // Sleep until an event occurs
If (Event (ArrivalNotification)) // Data frame arrived
{
ReceiveFrame();
ExtractData();
DeliverData(); // Deliver data to network layer}}
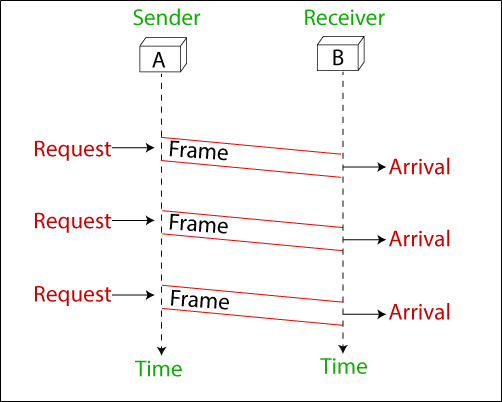
For example: The simplest protocol is very simple. The sender sends frames in the sequence without really knowing about the receiver. In this protocol to send three frames, there are three events at the sender and three events at the receiver. These events are shown below in the figure.
Stop-and-Wait Protocol
The sender sends a frame in the Stop-and-Wait protocol, and it stops until when the receiver receives the data and then sends the next frame. In this protocol, adds the flow control. This protocol is a unidirectional protocol for data frames, but auxiliary ACK (Acknowledgment) frames travel from other directions. The design of the Stop-and-Wait protocol is shown below.
Algorithm
Sender-site algorithm for the simplest protocol
while (true) // Repeat forever
canSend = true // Allow the first frame to go
{
WaitForEvent ( ); // Sleep until an event occurs
If (Event (RequestToSend) AND canSend)
{
GetData ( );
MakeFrame ( );
SendFrame ( ); // Sleep the data frame
canSend = false; // Cannot send until ACK arrives
}
WaitForEvent ( ); // Sleep until an event occurs
if (Event (ArrivalNotification)) // An ACK has arrived
{
ReceiveFrame ( );
// Receive the ACK frame
canSend = true;
}
}
Receiver-site algorithm for the simplest protocol
while (true) // Repeat forever{
WaitForEvent ( ); // Sleep until an event occurs
If (Event (ArrivalNotification)) // Data frame arrives
{
ReceiveFrame ( );
ExtractData ( );
Deliver (data); // Deliver data to network layer
SendFrame ( ); // Send an ACK frame
}
}
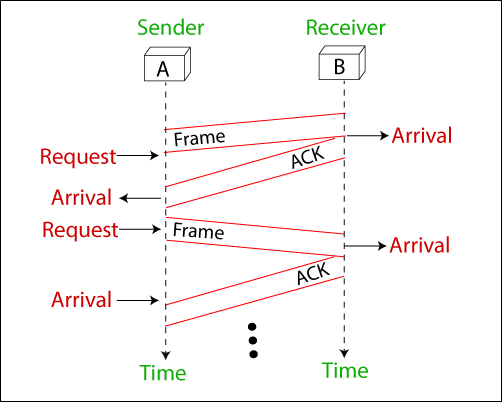
For example: The stop-and-wait protocol is very simple. The sender transmits a frame and wait for the receiver response. The sender transmits the next frame after arrives the ACK of the previous frame.
Note that sending three frames in this example involves the sender in six events and the receiver in three events. These events are shown below in the figure.
Noisy Channels
The noisy channel is divided into three sub-categories:
- Stop-and-Wait automatic repeat request
- Go-back-N automatic repeat request
- Selective repeat automatic repeat request
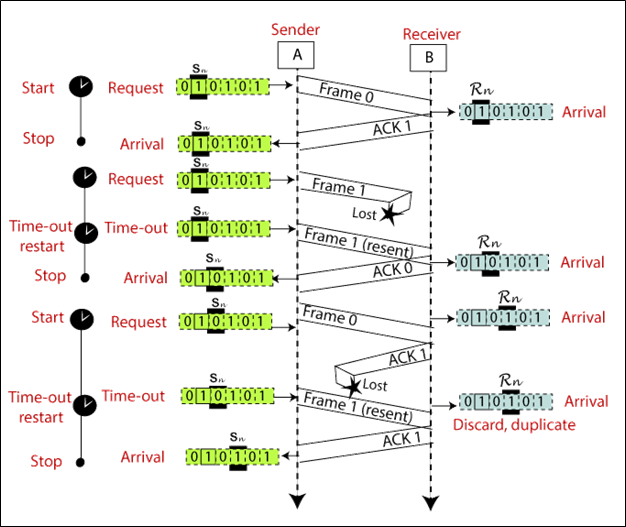
Stop-and-Wait Automatic Repeat Request
Stop-and-wait automatic repeat request is a protocol that is used in tele-communications to transfer the data between two connected systems.
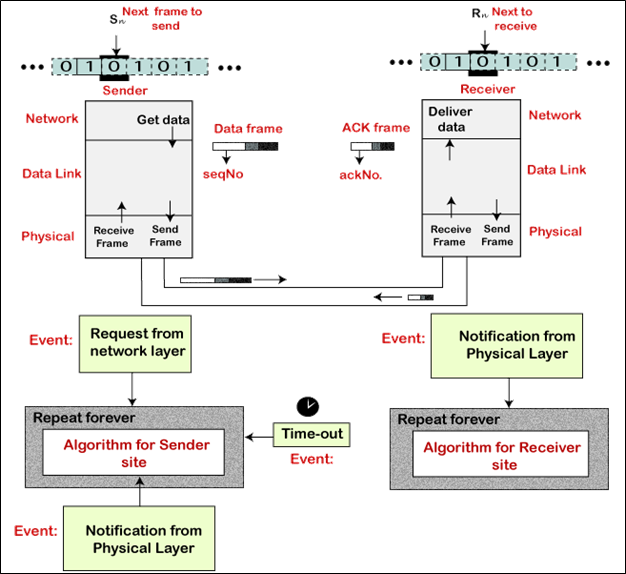
In the stop-and-wait automatic repeat request protocol, the sender sends one frame at a time. The sender transmits a frame and waits for the receiver response. The sender transmits the next frame after it arrives acknowledgment (ACK) signal of the previous frame. When the acknowledgment (ACK) does not reach the sender within a specified time, the sender sends the same frame again.
At the end of each frame, the sender adds redundancy bits. At the receiver-end, these redundancy bits are used to check the damage of the frames.
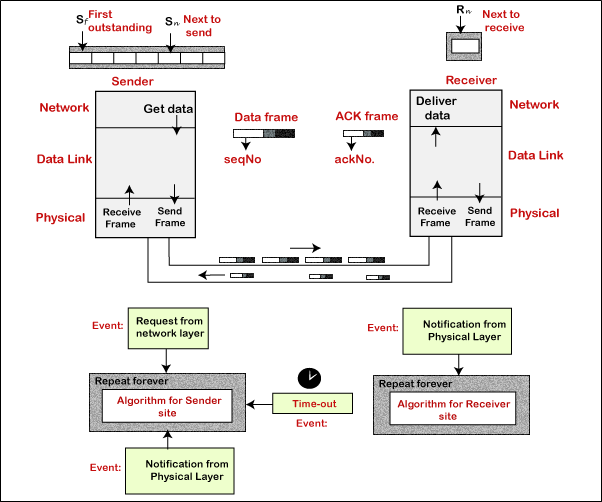
In this protocol, we need a sequence number for the frames. The design of the Stop-and-Wait ARQ protocol is shown below.
Algorithm
Sender-site algorithm for the Stop-and-wait ARQ protocol
Sn = 0; //Frame 0 should be sent first
canSend = true; // Allow the first request to go
while (true) // Repeat forever
{
WaitForEvent (); // Sleep until an event occurs
if (Event (RequestToSend) AND canSend)
{ GetData ();
MakeFrame (Sn); // The seqNo is Sn
StoreFrame (Sn); // Keep copy
SendFrame (Sn);
StartTimer ();
Sn = Sn + 1 ;
canSend = false ;
}
WaitForEvent (); // Sleep
if (Event (ArrivalNotification) ) // An ACK has arrived
{
ReceiveFrame (ackNo) ; // Receive the ACK frame
if (not corrupted AND ackNo == Sn) // valid ACK
{
Stoptimer ();
PurgeFrame ( Sn-1 ) ; // copy is not needed
canSend = true ;
}
}
if ( Event (TimerOut)) // The timer expired
{
StartTimer () ;
ResendFrame (Sn-1) ;
}
}
Receiver-site algorithm for the Stop-and-Wait ARQ protocol
Rn = 0 ; // Frame 0 expected to arrive
firstwhile ( true )
{
WaitForEvent() ; // Sleep until an event occurs
if ( Event (ArrivalNotification) ) // Data frame arrives
{ ReceiveFrame () ;
if (corrupted (frame) );
Sleep () ;
if ( seqNo == Rn ) // Valid data frame
{
ExtractData () ;
DeliverData () ; // Deliver data
Rn = Rn + 1 ;
} SendFrame (Rn) ; // Send an ACK
}
}
The example of Stop-and-Wait ARQ is shown below in the figure.
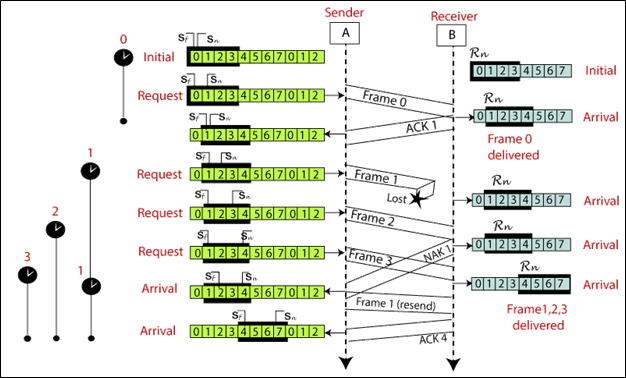
Go-Back-N ARQ
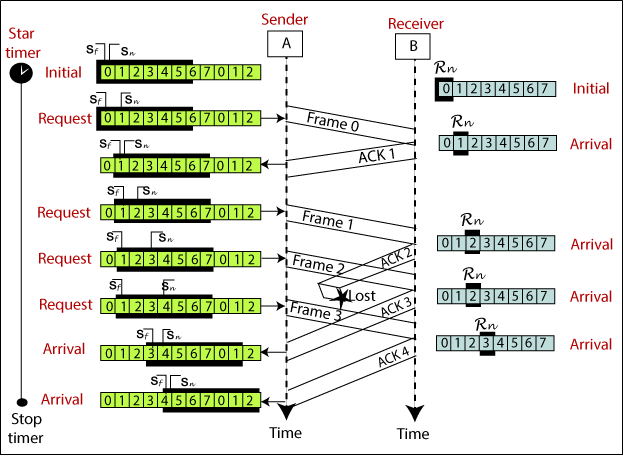
Go-Back-N ARQ protocol is also known as Go-Back-N Automatic Repeat Request. It is a data link layer protocol that uses a sliding window method. In this, if any frame is corrupted or lost, all subsequent frames have to be sent again.
The size of the sender window is N in this protocol. For example, Go-Back-8, the size of the sender window, will be 8. The receiver window size is always 1.
If the receiver receives a corrupted frame, it cancels it. The receiver does not accept a corrupted frame. When the timer expires, the sender sends the correct frame again. The design of the Go-Back-N ARQ protocol is shown below.
The example of Go-Back-N ARQ is shown below in the figure.
Selective Repeat ARQ
Selective Repeat ARQ is also known as the Selective Repeat Automatic Repeat Request. It is a data link layer protocol that uses a sliding window method. The Go-back-N ARQ protocol works well if it has fewer errors. But if there is a lot of error in the frame, lots of bandwidth loss in sending the frames again. So, we use the Selective Repeat ARQ protocol. In this protocol, the size of the sender window is always equal to the size of the receiver window. The size of the sliding window is always greater than 1.
If the receiver receives a corrupt frame, it does not directly discard it. It sends a negative acknowledgment to the sender. The sender sends that frame again as soon as on the receiving negative acknowledgment. There is no waiting for any time-out to send that frame. The design of the Selective Repeat ARQ protocol is shown below.
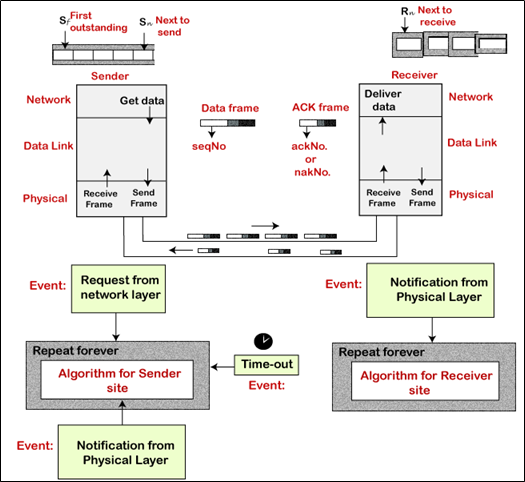
The example of the Selective Repeat ARQ protocol is shown below in the figure.
Piggybacking
It is used to increase the performance of the bidirectional protocols. In piggybacking, if node A sends a data to node B, it can also give the node-A information about the frame coming (or lost) from node B. if node B sends a data to node A, it can also give the node B information about the frame coming from node A.