Access Control in Networking
Access control in networking refers to granting or denying specific requests to access or use network resources, such as computers, data, applications, and other network devices. Access control aims to protect sensitive information and maintain the integrity, confidentiality, and availability of network resources by ensuring that only authorized individuals or systems can access them. Access control can be implemented through many methods, such as digital certificates, biometrics, passwords, and firewalls.
Access control in networking refers to regulating who or what is allowed to access a network and its resources, such as computers, data, applications, and other devices. This can be achieved through implementing policies, procedures, and technologies that enable administrators to manage user authentication and authorization, control access to network resources, and enforce security and compliance requirements.
Access control is a security implementation to ensure the confidentiality, and availability and integrity of sensitive information and network resources by allowing only authorized individuals or systems to access them. Its aims to prevent unauthorized access, ensure data privacy, and maintain the network's security... Some common access control techniques include username and password authentication, role-based access control (RBAC), firewalls, and encryption.
Application of Access Control in Networking
Access control in networking has a wide range of applications, including as:
- User Authentication
- Data Protection
- Resource Allocation
- Network Security
- Compliance
- Network Segregation
- Remote Access
1. User authentication: The user authentication in access control defines the process of verifying the identity of a user, typically through the credential provision such as password and username. This step is essential in access control as it helps to determine whether a user is authorized to access a particular resource or perform a specific action. User authentication used to ensure that only authorized users can access protected resources, maintaining the confidentiality and security of sensitive information. They verify the identity of users before allowing them to access network resources.
2. Data protection: Data protection in networking refers to the measures and technologies used to secure data transmitted over a network. This can include encryption to scramble data into an unreadable format, authentication protocols to verify the identity of users and devices, and firewalls to block unauthorized access to a network. Other data protection measures in networking can include private networks (VPNs), intrusion detection and prevention systems (IDPS), and secure socket layer (SSL) certificates. These measures aim to protect sensitive information from theft, unauthorized access, or manipulation as it is transmitted over a network, ensuring its confidentiality, integrity, and availability. They control access to important information, such as financial information, personal data, and intellectual property.
3. Resource Allocation: It determines which users or systems have access to which network resources, such as printers, servers, and bandwidth. Resource allocation in networking refers to allocating and managing the available resources, such as bandwidth, storage, and computing power, in a network efficiently and effectively. This process is critical in ensuring that network resources are used to meet the demands of different applications and users and avoid congestion, delays, and other performance issues.
There are various methods for allocating resources in networking, including:
- Fixed allocation - a fixed number of resources is assigned to each user or application, regardless of actual demand.
- Dynamic allocation - resources are assigned based on real-time demand to maximize efficiency and avoid waste.
- Fair allocation - resources are divided equally among users or applications, ensuring a minimum level of service for each.
- Priority allocation - resources are assigned based on priority, with higher priority applications receiving more resources.
The choice of resource allocation method will depend on the specific requirements of the network and its users and can be adjusted as needed demands and conditions.
4. Network Security: Protecting the user network from external threats, such as malware, hackers, and unauthorized access attempts. Network security used to protect a computer network and its devices from unauthorized access, theft, damage, and other cyber threats. This can include implementing firewalls, encrypting data transmission, using secure protocols, regularly updating software, and establishing secure passwords. The goal of network security is to ensure the confidentiality, integrity, and availability of network resources and information.
5. Compliance: Ensuring that an organization's network meets industry and regulatory data protection and security standards. Compliance in networking refers to the adherence to standards, regulations, and laws related to data security, privacy, and the handling of sensitive information. Some examples of compliance frameworks in the user networking industry include the Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), and the General Data Protection Regulation (GDPR). These frameworks set guidelines for the protecting sensitive information, such as credit card numbers, medical and personal records. Organizations that handle such information must follow these regulations to avoid financial penalties, damage to their reputation, and potential legal consequences.
6. Network segregation: Creating separate, isolated networks for different departments, users, or systems to prevent unauthorized access and maintain security. Network segregation, also known as network segmentation, divides a network into the smaller sub-networks, each with its own security policies, network architecture, and level of access. This helps to reduce a network's attack surface and limit the damage that a security breach can cause. There are several ways to implement network segregation, including VLANs (Virtual Local Area Networks), VPNs (Virtual Private Networks), and firewalls. Segmenting a network makes it possible to isolate sensitive data and systems from less secure parts of the network, such as guest networks or Internet of Things (IoT) devices. This helps improve the user network's overall security and makes it easier to detect and respond to the security incidents.
7. Remote access: Allowing the authorized users to access network resources from remote locations, such as from home or while travelling. Remote access refers to the ability of users to connect to a computer network or system from a remote location. This can be done using the various methods, including VPNs (Virtual Private Networks) and cloud-based services, remote desktop protocols. Remote access is widely used for the telecommuting, allowing employees to work from home or other remote locations. It also enables organizations to support customers and partners, allowing for remote maintenance and management of systems and networks. To ensure remote access security, it is important to implement strong authentication mechanisms, such as two-factor authentication, and to encrypt the data transmitted over the remote connection. In addition, organizations must regularly update their remote access systems and infrastructure to address any vulnerabilities and ensure they are protected against cyber threats.
Access Control Methods
There are several methods of access control in networking, including:
- Role-Based access control (RBAC)
- Access Control lists (ACLs)
- Authentication and Authorization
- Mandatory Access control (MAC)
- Discretionary access control (DAC)
- Key based access control (KBAC)
Role-Based Access Control (RBAC): Users are assigned roles with specific permissions and can only access resources that their role allows. Role-Based Access Control (RBAC) is a method of access control in which users are assigned roles, and these roles determine what resources they can access and what actions they can perform. This method is commonly used in organizations with multiple users with different levels of responsibility and privileges. In RBAC, roles are created corresponding to specific job functions or responsibilities, and each is assigned a set of permissions. When the user is assigned a role, they inherit its permissions. This allows the administrators to easily manage the user access to resources by assigning or revoking roles rather than the making changes to individual user accounts. RBAC is an effective and flexible access control method, but it requires careful planning and management to ensure that roles and permissions are defined appropriately.
Examples of roles in RBAC include administrator, manager, operator, or end-user. Each role would have different permissions, allowing the administrator to control access to sensitive information or critical systems.
Access Control Lists (ACLs): Access to the resources is defined using rules that specify which users or systems can access specific resources. An access Control List (ACL) is a method of access control in networking that allows administrators to specify which users or systems are allowed to access specific network resources. An ACL is the set of rules, also known as entries or permissions, that determine whether access to a resource is granted or denied. Each entry in an ACL consists of a source address, a destination address, and the type of access (permit or deny) allowed for that combination of source and destination. When an access request is made, the ACL is consulted to determine whether the request matches any of the entries, and access is granted or denied based on the match. ACLs are commonly used in routers and firewalls to control network resources and restrict access to specific IP addresses, ports, or protocols. They are also used to implement the security policies and enforce compliance with regulatory requirements.
ACLs effectively control the access to resources but can become complex and difficult to manage as the number of entries and the network size grows. It is important to carefully plan and manage ACLs to ensure that they are configured correctly and are not overly restrictive.
MAC (Mandatory Access Control): Access to resources is determined based on security labels assigned to users and resources. Mandatory Access Control (MAC) is a method of access control in which access to resources is determined based on security labels assigned to users and resources. MAC is used in environments where the highest level of security is required, such as in military and government organizations. It is often used in conjunction with the other methods, such as Role-Based Access Control (RBAC) or Access Control Lists (ACLs), to provide a comprehensive security solution. MAC provides a high level of security, but it can be difficult to manage and is inflexible compared to other access control methods.
In MAC, security labels are assigned to users and resources, and these labels define each security clearance level. Access to resources is then granted or denied based on the security labels, with the principle of "no read up, no write down", meaning that users with a lower security clearance cannot access resources with a higher security clearance.
"For example, if a user has a security label of "secret," they would only be able to access resources with a security label of "secret" or lower. A user with a higher security clearance, such as "top secret," would have access to resources with both "secret" and "top secret" security labels.
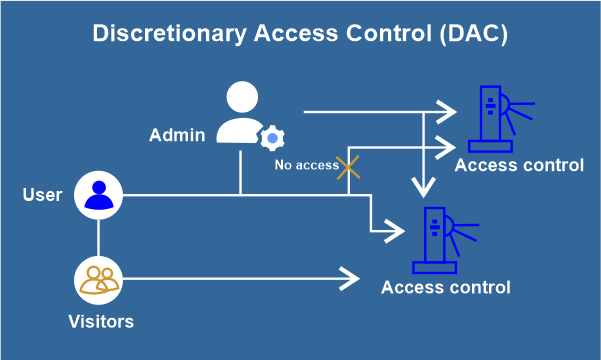
DAC (Discretionary Access Control): Users can control their resources and grant or revoke access to other users. Discretionary Access Control (DAC) is a type of the access control in computer networks where access to resources is granted based on the discretion of the resource owner. In other words, the resource owner can get grant or deny access to specific users or user groups. This is in contrast to the mandatory access control (MAC), where access is determined by predefined security policies and not by the resource owner. DAC is commonly used in small to medium-sized networks and is implemented through permissions and access control lists (ACLs). These ACLs determine which users or user defined groups are granted access to specific network resources, such as files, directories, or printers. The resource owner can modify the ACLs needed to grant or revoke access as necessary.
Key-Based Access Control: Access to resources is controlled using cryptographic keys, which are used to encrypt and decrypt data. Key-based access control is a method of controlling the access to resources based on the possessing a cryptographic key. In this type of access control, a user must present a key to the system to gain access to a particular resource. The key acts as proof of identity and authorization and are used to encrypt and decrypt data or to unlock resources. Key-based access control is commonly used in secure communication protocols, such as SSL/TLS, and in file encryption systems, such as PGP. In these systems, a user's private key is used to the encrypt a message, and the recipient's public key is used to decrypt it. This provides a secure channel for the communication and ensures that only the intended recipient can access the information.
Using smart cards or biometric authentication methods, key-based access control can also be used to secure physical resources, such as doors or cabinets. In these cases, a key is a physical object, such as a smart card or a biometric scan, that is used to unlock the resource
Authentication and Authorization: Users must provide a valid username and password before granting access to network resources. Authorization then determines the resources the user can access based on their authentication credentials. Authentication and authorization are two wide closely related concepts in computer networking.
- Authentication aims to ensure that the person or entity accessing the network resources is who they claim to be. Authentication is the process of verifying to the identity of a user, device, or system before granting access to resources. This is typically done through usernames, passwords, biometric information, or digital certificates.
- Authorization grants or denies access to resources based on the authenticated identity. Once a user is authenticated, the system checks the authorization rules to determine what resources they can access and what actions they can perform This is typically done through the use of the access control lists (ACLs), role-based access control (RBAC), or attribute-based access control (ABAC).
Together, authentication and authorization form the cornerstone of security in computer networks. By verifying the identity of users and controlling access to resources, these processes help to ensure that network resources are used in a secure and controlled manner.
Use of Access Control in Networking
Access control regulates who or what is allowed to access a network, its resources, and the data it contains. The use of access control helps to:
- Secure sensitive information: By controlling access to sensitive information, organizations can protect confidential data from unauthorized access and ensure data privacy.
- Manage network resources: Access control enables network administrators to manage who has access to specific network resources, such as printers, servers, and storage devices.
- Enforce security policies: Access control helps enforce security policies and procedures, ensuring that all network users follow the same rules.
- Prevent unauthorized access: Access control helps prevent access to network resources and data, reducing the risk of security breaches and data theft.
- Comply with regulations: Access control can also help organizations comply with industry regulations and standards, such as HIPAA, PCI-DSS, and SOX.
Overall, access control is a critical component of network security and helps to ensure that network resources and data are protected from unauthorized access and misuse.
Figure: show the security level in networking.
Factor affect Access Control in Networking
There are several numbers of factors that can influence access control in networking. The factors that affect access control in networking are as follows: o
- Firewalls: The hardware or software systems that act as the barrier between the network and external threats, controlling incoming and outgoing traffic. Firewalls are the key component of network security and are used to protect against unauthorized access to a network. A firewall acts as the barrier between the network and the external environment, controlling incoming and outgoing traffic based on predefined security rules. There are two main types of firewalls:
- Network firewalls: these are the hardware-based devices installed at the perimeter of the network to control incoming and outgoing traffic.
- Software firewalls: these are installed on individual devices, such as computers or servers, and are used to protect against incoming threats.
Overall, firewalls play a crucial role in securing networks by controlling access, monitoring traffic, and protecting against unauthorized access and malicious activity. Firewalls can be configured to allow or block traffic based on various criteria, such as source and destination IP address, port number, and application type or protocol used. They can also be used to implement virtual private network (VPN) connections, providing remote workers with secure access to the network.
- Encryption: Encryption is a process in which the information is transformed into a coded format to protect its confidentiality and privacy. In networking, encryption is used to secure data transmitted over the network, preventing unauthorized access to sensitive information. There are two main types of encryptions used in the networking that are as:
- Symmetric encryption: also known as the shared secret encryption, this method uses the same key to both encrypt and decrypt the data.
- Asymmetric encryption: also known as a public-key encryption, uses two different keys, a public key to encrypt the data and a private key to decrypt it.
Encryption is an very important aspect of network security, as it helps to protect against data breaches, hacking attempts, and other security threats. Encrypting sensitive information as the transmitted over the network helps ensure that even if the data is intercepted, it will be unreadable to unauthorized parties. In addition to these methods, encryption algorithms such as Advanced Encryption Standard (AES) and RSA are commonly used in networking to secure data transmission.
- Physical security: the measures in place to protect the network's physical infrastructure, including the devices and cabling. Physical security in networking refers to the measures taken to protect network equipment, such as routers, switches, and servers, from physical damage, theft, or unauthorized access. This can include implementing secure data centers, locked cabinets or rooms for equipment, surveillance cameras, access controls, and environmental controls such as temperature and humidity monitoring. The goal is to ensure network data and resources' availability, confidentiality, and integrity.
- User behavior: the actions and activities of users on the network can also affect access control, as users may attempt to bypass security measures or engage in malicious activities. User behavioral in networking refers to the actions and practices of individuals interacting with a network, including employees, contractors, vendors, and customers. This can include following password policies, accessing restricted resources, downloading software or data, and using the network for personal activities. User behavior can significantly impact network security, as malicious or careless actions can lead to security breaches, data loss, and other negative consequences. As a result, organizations often implement user education and training programs, technical controls, and policies to manage and monitor user behavior to maintain network security.
- Authentication: verifying an identity of users and devices before granting access to the network.
- Authorization: the process of granting or denying specific permissions to the users and devices based on their authenticated identities
- Policies: the rules and regulations that the determine who can access the network and what they can do once they are connected. Networking policies refer to rules and guidelines that dictate acceptable behavior and usage of a network. These policies help to ensure the network's security, reliability, and performance and protect sensitive information from unauthorized access or theft. Policies are typically enforced through a technical control, such as firewalls, intrusion detection systems, and access controls, and can also be the enforced through employee training and monitoring. It is important for organizations to regularly review and update their policies to reflect changes in technology and business needs. Some common types of network policies include as:
Acceptable Use Policy (AUP): outlines what activities are allowed on the network and what is considered inappropriate or harmful behavior.
Security Policy: defines the procedures for protecting network resources, data, and information.
Password Policy: this specifies the rules for creating and maintaining secure passwords. Backup and
Disaster Recovery Policy: outlines a procedure for protecting and restoring data in the event of a disaster.
Remote Access Policy: defines the set of rules for accessing the network from remote locations, such as home or while travelling.
Incident Response Policy provides guidelines for responding to security incidents and minimizing their impact.
These factors work together to maintain the security and privacy of a network and must be carefully considered and managed to ensure effective access control.