Define Framing in Computer Network
Framing is a function of the data link layer, which provides a way for a sender to transmit a set of bits that should be meaningful to the user. The primary function of Datalink is framing.
What is Framing?
Frames are nothing but a possible group of bits to be communicated.
Bits are boxed up and then combined into frames so that each frame is distinguishable and recognizable from another.
Frame at the data link layer distinguishes a message from a source to a final destination or from one point to another destination by computing a sender address and a destination address together.
Thus, the Data Link Layer needs to pack bits into frames so each frame is distinguishable.
Inserting a letter into an envelope separates one piece of information; the envelope serves as the delimiter.
The set of zeros and ones is packed into a frame, and these frames are understandable only by the data link layer.
A frame is a Character-oriented Protocol.
Framing type
Frames can be categorized as fixed-size or variable size
1. Fixed-size frame:
With fixed-size frames, you don't need to define frame bounds. The size itself can be used as a limit. An example of this type of framing is the ATM vast area network, which uses fixed-size frames called cells.
2. Variable size frame:
Variable-sized frames are standard in local area networks and require only a slight announcement of the end of a frame and the beginning of the next frame. Two different approaches are used for this task.
It must be defined to distinguish between the end of a frame and the beginning of the next frame. Here are two methods:
- Length Field - You can specify the length of the frame by adding a length field to the frame. Used for Ethernet (802.3). The problem with this is that the length field can sometimes get corrupted.
- End Delimiter (ED) – An ED (pattern) can be introduced to mark the end of the frame. Used in Token Ring. The problem with this is that ED can appear in the data. This can be resolved by Character/Byte Stuffing.
Character/byte stuffing: -
It is used when the frame consists of characters. Then, if the data contains an ED, 1 byte is inserted into the data to distinguish it from the ED.
It is the process of adding one extra byte whenever there is a flag or escaping character in the text. The bits to be transmitted are first broken into discrete frames at the data link layers
The checksum of each frame is computed if we want the bit stream to be error-free.
Now breaking this bit stream into frames is called framing.
The application layer creates the data, a set of zeroes and ones. Then, it goes to the transport layer; in the transport layer, it will add some zeroes and ones.
It is then passed over to the network layer. In the network layer also, it will add a network layer header, which we will call a packet.
So again, a set of zeroes and ones are added, and then it goes to the data link layer.
The two types of variable-sized frames are
1. Character-oriented framing
2. Bit-oriented framing
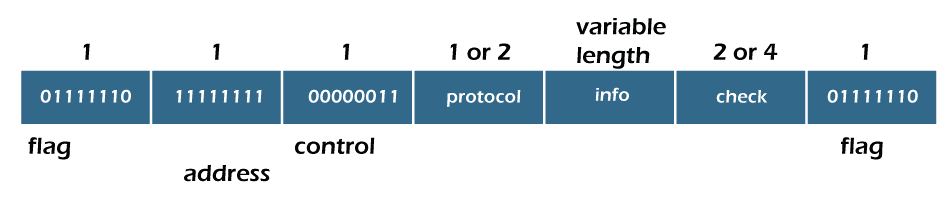
Character-oriented protocol
In a character-oriented protocol, data to be carried are an 8-bit character from a coding system such as ASCII.
The header, which usually carries the source and destination addresses and other control information, and the trailer, which has error detection or error connection redundant bits, are also multiple of 8 bits.
To separate one frame from the next, an 8-bit (1-byte) flag is added at the frame's beginning and the end.
The flag, composed of protocol-dependent special characters, signals the start or end of a frame.
The Figure shows the format of a frame in a character-oriented protocol.
- Any patterns used for the flag could also be part of the information. If this happens, the receiver thinks it has reached the end of the frame when it encounters this pattern in the middle of the data.
- To fix this problem, a byte-stuffing strategy is added to character-oriented framing in which a particular byte is added to the data section of the frame when there is a character that belongs to the same pattern as that of the flag.
- This particular extra byte is usually called the escape character(ESC), which has a predefined bit pattern whenever the receiver encounters the ESC character as data, not a delimiting flag.
- Byte stuffing by the escape character allows the flag's presence in the data section of the frame, but it creates another problem if the text containers contain one or more than one characters that are escape followed by a flag. Then, in this case, the receiver removes the flight.

To resolve this problem, any break-out characters inside the textual content must additionally be diagnosed with an extra break-out individual. Suppose the break-out individual is a part of the textual content. In that case, a different individual is usually brought to signify that the second individual is a part of the textual content.
Bit-oriented Protocols
In a bit-oriented protocol, the statistics segment of a frame is a series of bits to be interpreted by way of the top layer as text, photograph, audio, video, and so forth. However, similarly to headers (and possible trailers), we need a delimiter to separate one body from the opposite. Most protocols use a unique 8-bit pattern flag 01111110 because the delimiter outlines the frame's beginning and top.
This flag can create a similar kind of problem we saw in the byte-oriented protocols. If the flag sample seems to be inside the information, we must inform the receiver that this isn't the body's end. We do this by stuffing one single bit (in preference to 1 byte) to prevent the pattern from looking like a flag. The process is known as bit Stuffing. In bit stuffing, if zero and five consecutive 1 bit are encountered, a further zero is brought. This more filled bit is ultimately eliminated from the data by the receiver. notice that the extra bit is introduced after one 0 accompanied by way of Five 1s irrespective of the cost of the next bit. This ensures that the flag field series only sometimes seems in the body.
A frame body has the subsequent parts -
- Frame Header - It includes the control bytes as well as the frame's source and destination addresses.
- Flag - It marks the start and end of the body.
- Trailer - It includes mistake detection and mistakes correction bits.
- Payload field - It includes the message to be delivered.
Methods of Framing
- Count of Characters
The entire number of characters that are available in the frame must typically be counted using the methods presented here, even though it is never worn. While this procedure is frequently carried out by modifying header field values. Although this character count methodology ensures that framing in the data connection layer is at the receiver end about the overall range of characters maintained, and wherever the frame finishes. Utilizing this system has another drawback in that, in the event that the character count is ever incorrectly calculated during the transmission process, the receiver end may experience synchronization loss. The receiver's power is insufficient to determine or establish the beginning of the next frame.
- Character-stuffed Flag Byte
It is more commonly known as bit stuffing specifically. Byte stuffing really affects bytes since bit stuffing affects their bits. When there is communication that has a matching pattern, notably of the flag byte, a specific byte known as ESC (Escape Character) that has a defined design is typically attached to the data section of the frame. Although the receiver separates the ESC and the data, this could cause issues.
- Starting and Ending Flags with Bit Stuffing
An alternative name for Starting and Ending Flags with Bit Stuffing is a bit-oriented framing or bit-oriented approach. Bit stuffing is the practice of adding extra bits to data streams created by computer network protocol designers. In order to easily supply and send communication data and information to the recipient and to avoid or simply neglect the element of unwritten or inessential check sequences, additional bits are often lodged within the transmission unit. The only purpose of this type of protocol control is to stop the bit sample, which causes the transmission to go out of sync.
- Encoding violation
Encoding in physical media results in a kind of repetition that is used in multiple graphic or visual structures, simply encoding or representing information variables.
Framing's benefits in the data link layer
- The time-division multiplexing technique frequently employs framing in Data connections. A sender can transmit a class of valid bits to a recipient using frame at the data connection layer.
- The time-division multiplexing technique uses frames continually. It makes it easier for the sender to fill out a form to convey a set of valid bits to the recipient. Additionally, frames have headers that contain data like error-checking codes.
- There are frame architectures for A-Frame relay, Token Ring, Ethernet, and other data connection layer techniques. Frames enable the data to be split into numerous recoverable bits that can be checked for corruption further.
Conclusion
Additionally, as part of the data link layer, the header contains data such as error-checking codes.
Framing in Data Link Layer Relay, Token Ring, Ethernet, and other types of data link layer technologies has a specific frame structure.
Information can be decomposed into several recoverable pieces, and data link layer framing allows checking for corruption.
The Data Link Layer Framing feature provides a flow control mechanism that regulates the flow of frames, helping fast senders to prevent slow receivers from information overload.
Within the peer network layer, data link layer framing provides reliable information transmission services.