Test Set Lock Mechanism | Operating System
Modification in the Assembly Code
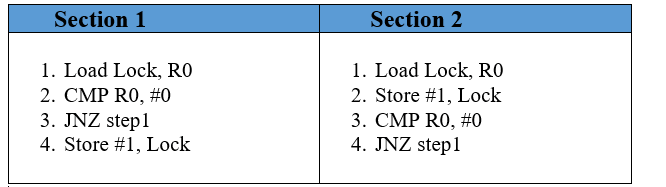
The problem in the lock variable is that, in some cases, the process reads the previous or old value of the lock variable and enters into the critical section. Because of this, sometimes, more than one process can enter into the critical section. Instead of this, the code given in the first section can be simply replaced with another code that is already present in the section. By doing this, the algorithm will not affect, but with the help of this, we can handle to offer mutual exclusion to a little bit but not entirely.
We can easily see that in the updated version of code. First, the lock variable value is loaded into the R0 register, which is the local register, and after loading the value, we set the value of the lock variable to 1.
In the 3rd step, we compared the value of the previous lock variable with 0. And then, we checked the value of the lock variable if the value is 0, then the process gets to enter into the critical section, but if the value is not 0. Then we have to wait for the process execution endlessly in the loop.
The advantage of setting the value of lock variable as 1, instantly with the help of process, is that if the process wants to enter into the critical section, then the process also holds the updated value of the lock variable, which is 1.
In the case, if the process is preempted and wants to schedule further, then in this case, the process will not enter into the critical section because the process already knows the current value of the lock variable means the updated value of the lock variable.
TSL Instruction
The solution discussed in the above sections offers the facility of mutual exclusions but not completely, and there may be a chance that more than one process can enter into the critical section.
What will happen when the process is preempted after executing the instruction, which is mentioned in the first step of section 2 written in assembly code? In that situation, there may be a possibility that a process brings the previous lock variable value, and without knowing the current value of the lock variable, the process enters into the critical section. Due to this, there may be a chance that at the same time, more than two processes enter the critical section.
To remove such type of problems, we take care of one thing that is ‘no preemption’ takes place after loading the earlier lock variable value, and before setting the value of lock variable to 1. We can solve this problem by combining the first two instructions, which are mentioned in the above two sections.
To solve this type of problem, some special instructions are given by the operating system named Test Set Lock (TSL) instruction. With the help of Test Set Lock (TSL) instruction at the same time, we can easily load the lock variable value into the local register R0, and after loading the value into the register, we set the value of lock variable to 1. And the process that first executes the Test Set Lock(TSL) instruction always enters into the critical section first, and the other processes are not allowed to enter into the critical section until the first process, which is already present in the critical section will come out. If there is a preemption in the process first, then, in this case, the process also cannot execute in the critical section.
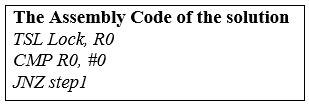
Now, based on the four conditions, we discuss TSL:
- Mutual Exclusion: - TSL (Test Set Lock) Mechanism provides mutual exclusion because, in TSL, there occurs no preemption before we set the value of the lock variable. In this at a specific time, only a single process can see the value of the lock variable that is 0. That’s why the TSL mechanism offers mutual exclusion.
- Progress: - Based on Progress definition, if there is a process which doesn’t want to enter into the critical section then due to such process, other process doesn’t allow to enter into the critical section. In the TSL mechanism, a process executes TSL instruction in case, if any process needs to enter into the critical section. If there is no process to enter into the critical section, then the value of the lock variable will be 0 always. That’s why the TSL mechanism offers Progress.
- Bounded Waiting: - In TSL Mechanism, sometimes, there may be a chance that a process waits for a long time to enter into the critical section, and there is no guarantee that a process will get a chance to enter into a critical section. That’s the reason that the TSL mechanism does not offer bounded waiting.
- Architectural Neutrality: - TSL (Test Set Lock) mechanism depends on the Hardware Platform, and the instruction of TSL is offered with the help of the Operating System. That’s why the TSL (Test Case Lock) mechanism does not offer Architectural Neutrality.