What is Telnet in Computer Network
Definition and Overview of Telnet
Telnet (short for “Telecommunication Network”) is a protocol that establishes an interactive session between two devices using text commands over computer networks. It operates on the application layer of the OSI model, providing a user with remote virtual terminal access.
Key Features
- Text-Based Communication: Telnet simplifies communication between local and remote devices by providing text-based data transmission. It also provides access to the command-line interface of that remote system.
- Client-Server Architecture: Telnet has a client-server architecture. The client links up to the remote server, which allows one to use resources at this point’s screen.
- Port 23: The standard port for Telnet communication is 23. When a user initiates the Telnet session, the port is used to create the connection.
Telnet Historical Background and Development
Telnet has its roots in the early days of computer networking. It was one of the earliest protocols that played a large part in influencing long-distance communication.
Development Era
In relation to this need for a mechanism of accessing and controlling remote computers, telnet was created.
In 1973, the Telnet was formalized in RFC number thirty-eight as “Tel – Net Protocol Specification.”
Early Implementation
The early stages of Telnet implementation were important in paving the foundation for network communication. It quickly became an indispensable aid to scientists who could employ remote computing capabilities.
Widespread Adoption
The Telnet protocol was popular among academics and researchers because of the advancement in computer networks. It played a vital role in fostering collaboration and resource sharing among institutions spread across space.
Challenges and Security Concerns
While Telnet turned out to be helpful almost immediately, it required support with security. The protocol transmitted data that contained login information in the clear, and it was, therefore, easy to eavesdrop without authorization.
Evolution and Security Improvements
Recognizing the need for better security, the industry provided more secure alternatives such as SSH (Secure Shell). SSH resolved the shortcomings of Telnet by making remote access, because communication was encrypted.
Legacy and Transition
Although Telnet usage has decreased significantly due to security concerns, it remains culturally valuable. Some legacy systems and environments currently still have Telnet, a testimony of its continuity.
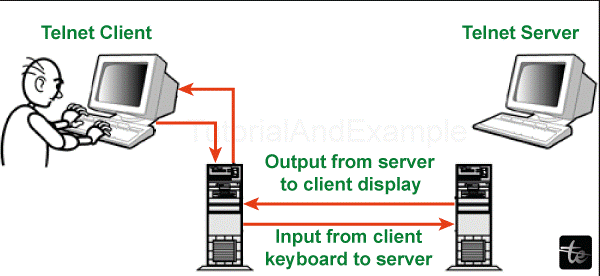
How Telnet Works: Client-Server Architecture
As a client-server technology, Telnet remote users connect with the host system. Understanding this structure is essential to understanding how Telnet allows communication between devices.
Client-Server Model
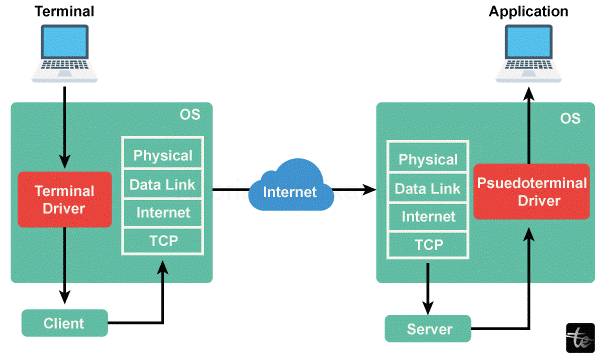
Telnet is based on the principle of client-server protocol, with a link established between a local terminal (client) and distant host (server). This model allows data transmission from the local and remote systems.
Client-side Interaction
A Telnet client installed on the user device makes a connection request to the host where an endless-running server runs. This request often entails specifying the host’s IP address or domain name and Telnet port number (usually 23).
Connection Establishment
As an answer to the request for connection, the Telnet server of its host establishes a link with the client. This connection turns into a virtual terminal that allows the user to work in the remote system as if he were actually there.
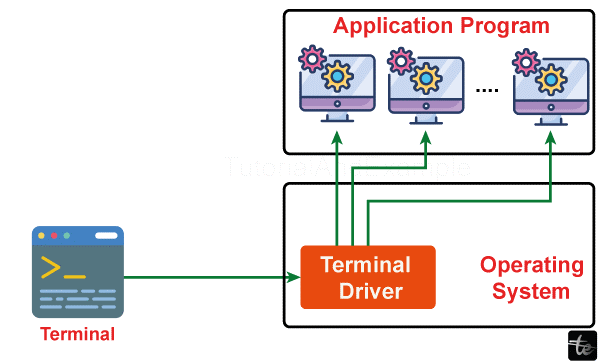
Terminal Emulation
Telnet uses terminalization and imitates a computer console on the client's part. This emulation ensures that any commands and data inputs by the customer are relayed to the remote host through their operating system.
Command Transmission
A Telnet connection is always initiated between a user’s terminal locally and some remote host. Under the environment of remote computing, hosts run such commands and possibly reply to a client with fixed output.
Data Transfer
Data can stream bi-directionally from the client and server sides using Telnet. Users can run commands, launch applications, and modify files in a remote host to collect theirs locally on the presentation.
Plain Text Communication
Telnet also uses clear text; all the data sent, especially passwords and command outputs, is unencrypted. The inability to encrypt means a compromise of security, especially where information is carried across networks that do not belong to them.
Session Termination
After completion of using Telnet, the user can log out. This comprises logging off, severing the VTE connection, and placing a user back on the local site.
Telnet Commands and Syntax
Telnet serves as a protocol for network usage that relies on… Understanding these commands is critical for easy navigation and communication with the remote machine.
Connecting to a Remote Host
Syntax: telnet [host] [port]
Example: telnet example.com 23
Explanation: This connects to the specified host on the specific port (default is 23).
Logging In
Syntax: login: [username]
Example: login: user123
Explanation: Next, enter the username assigned to the remote system.
Providing Password
Syntax: Password: [password]
Example: Password: *********
Explanation: Once you have input the username, then type in its corresponding password for authentication.
Exiting Telnet Session
Syntax: exit or logout
Example: exit
Explanation: Ends the Telnet session and drops connection with the remote host.
Closing Connection
Syntax: Ctrl+] followed by quit
Example: Press Ctrl+] followed by quit
Explanation: Closes the Telnet connection gracefully.
Remote System Information
Syntax: who or finger
Example: who or finger
Explanation: Provides information about current users logged in on the remote system.
Remote System Status
Syntax: stat or status
Example: stat or status
Explanation: Gets the status and information about the remote system.
File Transfer
Syntax: send [file]
Example: send example.txt
Explanation: Copies a file from the local system to the remote host.
Remote Shell Access
Syntax: ! followed by a command
Example: !ls
Explanation: Runs a shell command on the remote host without terminating the Telnet session.
Character Set Configuration
Syntax: Ctrl+] followed by set charset
Example: Hit Ctrl+] and type set charset.
Explanation: Sets the character set for the Telnet session.
Toggle Echo
Syntax: Ctrl+] followed by toggle echo
Example: Press Ctrl+] and enter toggle echo
Explanation: Toggles the local echo of characters typed during a Telnet session.
Display Help
Syntax: help or ?
Example: help or ?
Explanation: Gives Telnet available commands.
Telnet vs. SSH
Introduction to Telnet
Telnet or Telecommunication Network is one of the first network protocols to have provided remote system access. Telnet was developed in the period when security issues were not of much significance; it works as a text-based and unencrypted protocol. It allows command-line access to remote devices and systems management over the network.
Introduction to SSH
SSH stole the stage in order to become a strong and secure equivalent of Telnet, which was inherently weak. The SSH uses encryption technologies grant each of the two connected devices with a secure and authenticated connection over an insecure network. The cryptographic protocol involves confidentiality and integrity-oriented specifications that make it applicable for private data transmission. SSH can use a number of different methods for authentication, such as passwords and public-key cryptography, which allows greater flexibility.
Key Differences
| Comparison Index | Telnet | SSH |
| Security Mechanism | Telnet operates in plaintext mode, and thus, data is vulnerable to tapping. Because it is unencrypted, this makes it vulnerable to security attacks. | This protocol ensures both confidentiality and integrity through the use of encryption algorithms. It also offers excellent security from intrusion. |
| Authentication | It provides a simple username-password authentication scheme in a clear layer that could be susceptible to an attack. | It also supports multiple authentication strategies, which may be the passwords or public keys/certificates in a controlled enclave. |
| Encryption | Telnet sends data using a clear text that is interceptable. It does not encrypt data for safe transmission. | Throughout the session, all communication is encrypted by SSH to ensure that only one approved individual can communicate and that no data transmitted remains unencrypted. |
| Data Integrity | It does not ensure data integrity because the transmitted bits can be corrupted. | In data integrity, cryptographic mechanisms guarantee that the transmission process is not changed by unauthorized parties. |
| Use Cases | The server for remote command line access to systems, however, has been replaced by talk due to security weaknesses. | Most environments use SSH for secure remote access, file transfer (SFTP), and shell-based communication. |
| Interactive Sessions | This protocol mainly targets interactive sessions and can be managed remotely via a command-line interface. | Administrates interactive sessions and secure file transfers along with remote command execution, which makes it a flexible choice for multiple applications. |
| Legacy Considerations | Viewed as out-of-date and insecure for modern network environments, usually replaced by better security protocols. | Thanks to its flexibility and powerful security parameters, SSH remains an optimal choice for secure communication, even in old-fashioned systems. |
Security Considerations: Telnet vs. SSH
If one were to compare the security of Telnet and SSH, several significant discrepancies can be found that directly influence whether these technologies would serve contemporary networks well.
Telnet Security Considerations
- PlainText Transmission: Telnet sends data such as usernames and passwords through the network on unencrypted text. This leaves sensitive information vulnerable to possible eavesdropping and interception by wrong elements.
- Lack of Encryption: Telnet does not provide encryption from where attackers can intercept data and read without any cryptographic protection. This creates a real threat, especially in not trusted or public networks.
- Authentication Risks: The basic username and password authentication of Telnet becomes vulnerable to a packet sniffer during an unencrypted data transmission, making unauthorized access easier.
- Limited Confidentiality: Since Telnet does not involve encryption, It offers poor confidentiality. Any type of data, like commands and responses, is easily monitored and understood by malicious users.
- No Data Integrity Assurance: Telnet does not guarantee data integrity. If data is not encrypted during transmission, manipulation threats could cause real security compromises.
SSH Security Considerations
- Encrypted Communication: SSH encrypts all the channels used in communication between two parties, allowing seamless transmission of data from one party to another. This encryption ensures that no one can gain illegitimate access to the information, and also it will not be intercepted.
- Authentication Options: SSH offers various authentication options, such as password-based and public keys. This adaptability allows users to select a reliable authentication mechanism depending on their security needs.
- Secure Port Default: The port number 22 is the default communication part of SSH. When coupled with a secure default port, encryption contributes to overall protection, wherein no one specific port is attack-proof.
- Data Integrity Assurance: Cryptographic functions are used to authenticate the transmitted data in SSH. If an attempt is made to change anything in the data during transfer, it will be immediately detected, and no unauthorized alterations shall occur.
Telnet & SSH Applications and Use Cases
Despite the difference in services provided by Telnet and SSH, they both are useful for various activities.
Use Cases and Applications of Telnet
- Remote Device Management: Telnet was mainly used to drive things at remote locations predominantly in network hardware such as routers and switches. Through the command-line interface, administrators are able to configure and troubleshoot devices from a remote location.
- Network Testing and Debugging: Network tests and debugs use Telnet. It enables administrators to access a designated port on the remote server to ensure network issues and availability.
- Legacy Systems Support: Certain legacy systems and devices continue to offer Telnet for remote access. Although not advised due to security concerns, Telnet is employed when a switchover from other more secure protocols becomes unbearably tedious.
Use Cases and Applications of SSH
- Remote Command Execution: Secure commands can be run on remote nodes with SSH. This tool allows System Administrators to administer and configure servers remotely, a modern way of managing servers.
- Tunneling and Port Forwarding: SSH tunneling has both functions, such as providing tunnel services and allowing port forwarding by building secure links between remotely located machines and local computers for data transmission. This function is used in the open environment where secured services are attempted.
- Git and Version Control Systems: Developers rely on SSH for secure access to Git and other version control systems. Authentication is done using SSH keys to ensure secure and authenticated communication with code repositories.
- Secure File Storage and Retrieval: SSH saves and downloads files from these protocols, such as SFTP. In this setting, the secrecy and safety of transmitted files are guaranteed to ensure management security.
Advantages of Telnet
Simplicity and Ease of Use
Telnet is user-friendly. The interface, which is text-oriented, allows users, even those who are not technical by nature, to control remote systems using a small command set.
Resource Efficiency
Telnet needs more system resources to work on. This is further beneficial where the resources of networks or systems are going to be much more diversified.
Wide Compatibility
Telnet works with many different kinds of operating systems and is thus a great multi use remote management tool. It offers a standard way of accessing Windows, Unix, or Linux systems.
Platform Independence
Telnet is hardware platform independent because it does not depend on the underlying hardware architecture. Users can access the devices regardless of the type of processor or system architecture.
Low Overhead
Telnet has minimal overhead on network bandwidths and system resources. It operates in the clear, so relatively little processing is involved as compared to more sophisticated protocols.
Real-Time Interaction
Telnet enables real-time communications between users and remote systems, where commands are issued with instantaneous results. This quick response is beneficial for tasks that need immediate verification or troubleshooting.
Legacy System Support
Telnet remains necessary for access to legacy systems that do not support contemporary and safe protocols. Under certain restrictions, when it is impossible to upgrade the infrastructure, some environments use backward-compatible solutions like Telnet.
Educational and Training Purposes
Telnet's relative simplicity makes it a good tool for educational settings and training environments. It enables students and novice users to learn the basic fundamental principles of network communication using rather simplified protocols.
Quick Connection Setup
Telnet facilitates easy connection without too many configurations. Through the use of a command-line interface, a connection can be initiated, reducing setup time for remote access.
Disadvantages and Risks of Telnet
Man-in-the-Middle Attacks
Telnet is vulnerable to attacks in which an attacker intercepts and maybe alters communication between the client and server. In the absence of encryption, malicious players can intercept and alter critical data while in transit.
Limited Session Encryption Options
While some versions of Telnet offer session encryption through mechanisms such as Kerberos, this is not an inclusive trend. The majority of Telnet implementations have poor encryption functionality, leaving their communications open to interception and modification.
Protocol Spoofing
Telnet communications work through a simple protocol that attackers can fake. Malicious actors may masquerade as Telnet servers, causing unsuspecting users to connect to a fraudulent system, enabling the compromise of data integrity.
Inadequate for Modern Secure Applications
Telnet needs to address security issues to be more appropriate for use on modern secure applications and environments. Industries and situations where enforcement of strict standards is demanded usually choose more secure alternatives such as SSH (Secure Shell).
No Native Encryption
Telnet lacks native encryption support. Indeed, unlike other more secure protocols like SSH, which encrypt the entire communication channel; Telnet's plaintext nature prevents it from protecting information in transit.
Limited Authorization Controls
Telnet offers few authorization protections, which makes it difficult to implement fine-grained access control mechanisms. This restriction may result in situations where the users have more significant access to resources than is required or necessary, thus increasing vulnerability to unauthorized activities.
Not Firewall-Friendly
Since Telnet uses dynamic port assignments, it is difficult to configure firewalls so that specific traffic can pass through them. This unfriendliness to firewalls can make managing network security, especially in large and complex structures, difficult.
No Integrity Checks
Transmitted data integrity has no built-in mechanisms in Telnet. The lack of protective measures against integrity checks makes it vulnerable to information distortion; however, users cannot know if their data has been altered during transit.
Vulnerability to Password Sniffing
Since passwords are transmitted in plaintext over Telnet, it is vulnerable to a 'password sniffing' attack. During the login process, attackers can obtain passwords and other details to gain access to victims' accounts and compromise system security.
Obsolete Encryption Methods
In cases where Telnet indeed applies encryption techniques, these could be obsolete and susceptible to cryptographic attacks. The use of old encryption techniques makes the protocol more vulnerable to security threats.
Best Practices for Telnet Usage
Use SSH Instead
To enable secure remote access, use Secure Shell (SSH) instead of Telnet. SSH provides data encryption, an improved version of Telnet that does not encrypt the transmitted information. SSH is widely used and recommended because many systems and applications support the protocol.
Limited Use in Trusted Networks
Allow Telnet to be used only on trusted, internal networks. Of course, do not make the Telnet services available on the Internet, as unencrypted data transmission can be intercepted at any time. To protect Telnet traffic from external connections, use VPNs or SSH tunnels.
Employ Encryption
If Telnet has to be used, enable the encryption capabilities available with certain implementations of the protocol. Although it is less secure than SSH, encrypted Telnet offers further protection from eavesdropping.
Regularly Update Software
Upgrade Telnet server and client software. Routinely update the software security patches and updates supplied by its vendor. Known attacks apply to old software.
Conclusion
In summary, Telnet is a relatively simple network protocol that allows command-line remote access to devices. Although Telnet is an important part of history, its importance has reduced slightly because data travels in plain text due to security breaches. The arrival of safer alternatives, like Secure Shell (SSH), indicates the need for securing necessary data in remote communication.