WAP-Wireless Access Point
A Wireless Access Point (WAP) is a type of networking gadget that connects several devices to a wired network. A Wireless Access Point (WAP) works to form a WLAN (Wireless Local Area Network), and it is typically seen in large workplaces and buildings with expanding enterprises.
It is easier to comprehend and implant the gadget. It can be stationary, mobile, or hybrid and has flourished in the twenty-first century. The accessibility, security, and reliability of the exchange of information and network are responsibilities that must be upheld.
A wireless access point links wired networks and wireless clients. It makes it easier for mobile users to connect to the network, increasing productivity while lowering infrastructure costs.
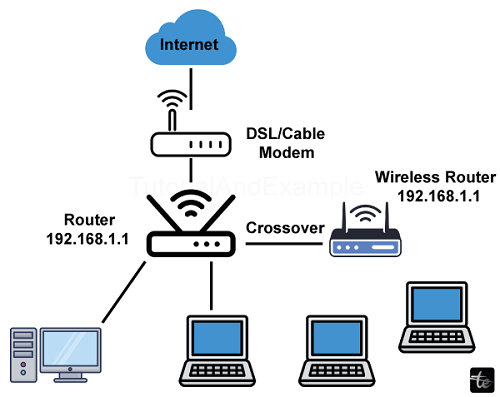
For example, in an enterprise wireless network, many workers can print papers from their PCs that are physically linked to the network's wireless connection using a wireless printer situated centrally in the office. The WAP device serves as a hub for delivering and receiving data over WLAN (Wireless Local Area Networks).
The access point is usually employed in residential and business networks. A company can offer secure access points that allow you and your coworkers to work wherever in the workplace while being linked to a centralized network; you are connecting to the internet via an access point rather than a cable. In most households, a wireless access point (WAP) serves as a wireless router that connects to a DSL or cable modem. IEEE defines the standards and frequencies, and all WAP devices adhere to the IEEE 802.11 specifications.
What is the need of WAP?
Networking & Internet services are critical components of today's corporate computing. An increasing percentage of internet users have gone mobile. These mobile users want network connectivity regardless of wherever they are since they wish to use the network simultaneously. Wireless LANs allow users to access shared data without having to seek for a spot to plug in their computers, and network managers do not need to build up networks by wiring up cable and equipment.
Working of WAP (Wireless Access Point)
Wireless LANs employ electromagnetic radiation (radio or infrared technologies) to transmit data from one location to another without requiring a physical connection. Radio waves are sometimes referred to as radio carriers since they merely transport energy to a distant receiver. The data being communicated is overlaid on the radio wave, allowing for precise extraction at the point of reception. This is sometimes referred to as carrier modulation by the sent information.
When data is overlaid (modulated) onto a radio transporter, the radio signal takes up more than one frequency because the modulating information's frequency or bit rate is added to the carrier. Multiple electromagnetic carriers can coexist in the same space without interfering with one another if radio signals are sent at distinct frequencies. To gather data, a radio reception selects one radio frequency and rejects all others. In a typical wireless LAN design, a transmitter/receiver (transceivers) device known as an access point links to the wired network from a fixed position using ordinary cable.
The access point connects the wireless LAN & the wired network architecture by receiving, buffering, and retransmitting data. A single connection point can accommodate a limited number of users and operate within an area of less than a hundred to several thousand feet. The point of access (or the antenna that's attached to it) is often set high, but it may be mounted almost anywhere as long as the requisite radio coverage is achieved.
End users connect to the wireless LAN using wireless LAN adapters in order which are installed as addition cards in notebooks or palmtop computers, are chips in desktop machines, or as integrated components in handheld computers. Wireless LAN adapters connect the client network's operating system (NOS) to the airways via an antenna.
Transmission Media
Wireless LANs can transmit data using either radio wave (RF) or infrared light (optical). Each technology has its own set of benefits and limits. The characteristics of these two systems are explained below.
Radio Wave Technologies
Radio waves travel freely in the air. They are utilized in a variety of applications. Radiowaves are used in radio broadcasting, television transmission, telecommunication, and defence. The band utilized for a certain application is extremely important and can't be utilized for other purposes. The selection of a certain band for an application is governed by both national and international agreements. Radio wave transmission as well as reception needs extremely advanced technology. Both receivers and transmitters must operate inside a narrow band.
The following are the issues linked with radio frequency transmissions:
Path Loss SNR, or information to noise ratio, is characterized as the power of the heard information divided by the power of the heard signal's noise. This aspect improves the communication system's performance. However, improving this characteristic will increase the complexity of the design. SNR may be improved by either increasing transmitting power or lowering the distance between transmitter and receiver.
Neighbouring channel interference: Another phenomenon that impacts radio frequency transmission occurs when a single frequency band is assigned to two neighbouring transceivers that, resulting in interference. Interference happens when one good signal is confused with another. This issue can be addressed by splitting the available spectrum into sub bands and assigning separate bands to neighbouring transceivers.
Another issue with transmission of radio waves is multipath. A receiver at any location can receive two sorts of signals from the transmitter. It is the direct signal, while the other is the signal that is reflected. Everything reflects radio waves. As a result, the receiver can receive many reflected signals via different pathways. At certain locations, the signal intensity is additive, while at others it is out of phase. As a result, the receiver may get maximum power at certain moments while receiving minimal power at others. This process is referred to as wavelength selective fading. This problem may be handled with two antennas separated by a quarter wavelengths.
Narrow Band Technology
A narrow-band radio system sends and receives user data over a specified radio frequency. Narrow-band transmission employs a single frequency modulation scheme that is mostly configured in the 5.8 GHz range. The main advantage of narrowband networks is high throughput since they lack the overhead associated with broadband systems. Radio LAN is an instance of a system that uses narrowband technology. Unwanted crosstalk between communications channels is prevented by properly coordinating various users on separate channel frequencies.The usage of different radio frequencies in a radio system ensures privacy and non-interference. The radio receiver rejects all radio signals other than the one that comes from to which it is set. According to the client, one disadvantage of narrowband technologies is the fact that the user must get a license to utilize the specified frequency.
Direct Sequence Spread Spectrum Technology (DSSS)
This technique is used in the vast majority of wireless LAN systems. More bandwidth is used compared to narrow-band transmission. The transmission of the signal is spread across an authorized band using direct sequencing spread spectrum (for example, 25 MHz). A random binary string known as a spreading code is utilized to modify the transmitted signal. The data bits are translated to a pattern of "chips" at the source and then back into a bitstream at the destination. Spreading ratio refers to the total quantity of chips used to represent one bit.
At the price of larger bandwidth, as higher the propagation ratio is, as greater the signal's resistance to disruption. The Federal Communications Committee for Foreign Radio Transmission (FCC) advises that the propagation ratio be more than 10. The majority of devices have a spread ratio that's less than twenty, while the recently released IEEE 802.11 wireless networking standard specifies a spread ratio of eleven. The transmitter and receiver must be synced using identical spreading code. To an unintentional receiver, DSSS looks as low-power broad band noise, which is discarded (ignored) by most narrow-band receivers.
Frequency-hopping Spread Spectrum Technology (FHSS)
This approach divides the band into several little sub-channels for each 1 MHz frequency. The signal then travels from sub-channel to sub-channel, broadcasting small bursts of data on each for a predetermined amount of time, known as dwell time. The hopping sequence has to be synchronized at both the transmitter and the receiver; otherwise, all information would be lost. Frequency hopping is not as prone to interference since the frequency is continually changing. This renders frequency-hopping systems particularly difficult to intercept. This characteristic allows frequency-hopping devices a high level of security.
To disrupt a frequency bouncing system, every band has to be jammed. These traits appeal to law enforcement and military agencies. To an unintentional recipient, FHSS seems to be a brief impulsive noise.
Infrared Technology
Infrared (IR) is a technology that is rarely utilized in commercial wireless local area networks. Infrared has a frequency far higher than radio waves. They have a frequency of at least 1014 Hz. Optical cables, TV remote controls, CD players, and more applications already employ infrared technology. IR systems are easy to develop and hence economical. They utilize the same frequency bands as fiber optic lines. IR systems detect just the signal's amplitude, hence interference is considerably minimized.
Infrared systems require unique infrared emitters and detectors. Infrared transmission is carried out in two ways. The first approach employs direct modulation, whereas the second uses channel modulation. Wireless LANs exclusively employ the direct modulation approach, which is detailed below.
Direct Modulation
Direct modulation, often known as on-off keying, is commonly employed in fiber optic systems. A binary 1 immediately turns on a light source, which is often an LED, while a binary 0 turns it off. The direct modulation scheme is similar to that seen in Figure. Before being modulated, the source bit flow is encoded using an ordinary encoding method. The encoded data is subsequently modified by a modulator. To lower power consumption, pulse position modulation or other comparable modulation techniques are used.The modulated signal is then delivered into the LED device. On the receiving end, an optical range-pass filter is employed to pick the needed band that includes the signal that is sent component. The photodetector generates an electrical signal in modulated form. A demodulator removes the data that has been encoded from this, whereas a decoder restores the data in its original form. Direct modulation is typically employed in a room or small area when the transmitter and receiver have a direct line of sight.
Operating Modes
Infrared connections can be employed in two distinct ways. There are two types of modes: direct (point-to-point) and diffuse (omnidirectional). In a direct mode, the radiation from the emitter is focused directly at the detector. As a result, low-power emitters and photo detectors with lower sensitivity are viable options. This method of operation is suitable for establishing a direct wireless connection with two portable devices. Directed systems have an acceptable radius of a few kilometres and may be utilized outdoors. It also provides the best bandwidth and throughput. High-performance directed IR is impracticable for mobile users; hence it is primarily utilized to create stationary sub-networks.
In the diffuse setting, the infrared light of the light source is optically dispersed, scattering it across a large region. Thus, this method is appropriate for broadcasting. Omni-directional infrared systems have very limited range, often decreasing coverage to 30 - 60 feet, and are infrequently employed in particular wireless LAN applications. All of the detectors in the area can receive a signal from a single transmitter, with variable phases. The phase fluctuation results from differences in route length between the signalling device and receiver. Several reflections of light additionally generate phase variation. This phenomenon is referred to as multipath dispersion. In an everyday setting, this difficulty will have little impact on communication.
WAP (Wireless Access Point) Modes
Infrastructure Mode
To tackle specific challenges of supplying services from a stationary network for mobile users, an infrastructure-based wireless LAN is employed. In a LAN, a central server runs on an established wired network. Portable customers can access fixed network services via access points known as Portable Access Units. The figure depicts the framework of a LAN. The typical range for a PAU ranges from 50 and 100 metres.
Ad-hoc Mode
The simplest setup of a wireless LAN is comprised of PCs having wireless adapter cards. They may establish an autonomous network whenever they're within proximity to one another. This is known as a peer-to or informal network. This setting must be set on demand. Such networks do not require any management or pre-configuration.In this scenario, every client would only be given the abilityto utilize the resources that are part of the additional clients, not a central server.Access points are limited to finite range, often 500 feet indoors and 1000 feet outside.
In a big institution, like a university or college campus, more than one entry point will most likely be required. A site survey is used to determine where access points should be installed. The purpose is to design the area of coverage with overlaid coverage cell so that customers may travel around the region without losing network connection. Roaming refers to clients' ability to move effortlessly among a set of access points.
Access points transfer clients from one to a different one in an unobtrusive manner, maintaining continuous connectivity. Wireless LAN may be required for conferences held in buildings or airports, as well as meetings held at company headquarters.
Components of WAP
A wireless LAN requires extra components beyond those required by a traditional cable LAN. They are RF or IR transmitters and receivers. Antennas are required for two-way communication between radio frequency transmitters and receivers. This field necessitates extensive understanding of antenna and propagation. Usually, a test installation is performed before to real deployment. Hubs, which are bridges, network operating systems, servers, and other components on a wired LAN continue to function normally.
Mobile Clients
Mobile clients are mobile computers that function as clients. The ones that follow are some examples of mobile systems.
- Laptop computer systems: Laptop PCs having two-way communication capability (transceiver).
- Palmtops and Personal Digital Assistants (PDAs) with communication capabilities.
- Portable fax.
- Cell phones
Special Units
A wireless LAN requires additional equipment to administer the network and communicate effectively.
These are:
- Communication units: these are devices that communicate both inside the network and with other networks.
- Data collection units: These units gather information from other systems.
- Security Units: those that manage network security. Transceivers are half-duplex devices. It transmits and receives data via a wireless LAN. It is capable of transmitting in one way at a time.
- Portable bridges: These bridges can support net working activities. A bridge connects two wireless LANs. It might be a transceiver, a satellite port, or another type of communication gear that provides bridge services.
lProtocol for Wireless Access Point
The CSMA protocol is quite complex to implement in wireless LAN. Thus, particular procedures are required to avoid collisions. MACA & MACAW are both of the most commonly utilized protocols.
MACA Protocol
In 1990, Kam created the MACA (Multiple Access with Collision Avoidance) method for wireless communication. The protocol is quite simple to create and operates in the way that follows. Station X, which wishes to transmit data to adjacent station Y, transmits a brief frame known as RTS (Request to Send) first. When all stations except the receiving station hear this short frame, they avoid transmitting, letting the connection to proceed without interference. The receiving station transmits a clear to send (CTS) frame to the caller station. After getting the CTS frame, transmitter X starts transmitting. When two stations, Wand X and Station Y, transmit RTS simultaneously, both frames clash and are lost. When there is no CTS at location Y, the two stations wait a random period of time (binary exponentially back off) before restarting the operation.
MACAW Protocol
Bhargavan et al (1994) analyzed the behaviour of the MACA protocol and improved it with adjustments. The initial change was to include an acknowledgment frame for each frame that was successfully received. This tweak provides carrier sense to station. The second alteration was applying the binary or exponential back off method to the source-destination pair. This increases the equitable nature of the procedure. They have also introduced the option for stations to communicate information about congestion.
Uses of WAP (Wireless Access Point)
Wireless Access Point is commonly used as an alternative to wired LAN networks. They frequently offer the final few meters of communication between a wired network and a mobile device. The list below illustrates some of the numerous applications madeavailable by the power and flexibility of wireless LANs.
- Nurses and physicians in hospitals may be more effective because wireless handheld terminal or notebooks with wireless LAN connectivity can send patient information quickly.Quick wireless networks setup can boost productivity for consulting or accountancy audit teams, as well as small workgroups.
- Students or research researchers attending a lesson on an institute site can instantaneously connect to the Internet and check the catalog of the internet digital library.
- In dynamic situations, network administrators minimize the overhead associated with wireless LAN transfers, network expansions, and other changes.
- Wireless connection is used at corporate training facilities and by university students to facilitate information access, exchange, and learning.
- Wireless LANs, according to network administrators deploying networked PCs in older buildings, are an economical network infrastructure option.
- Tourists and tourists can buy their tickets online throughout their trip.
- Warehouse workers utilize wireless LANs to communicate with central databases.
- Network administrators use wireless LANs to offer backup for critical applications that run on wired networks.
- Senior executives at meetings make faster judgments because they have instantaneous data at their disposal.
Application of Wireless Access Points
- Wireless Printing: Once wireless printers are linked to the network, users can print from anywhere within the access point's range.
- Cloud services: Wireless access points may link devices to cloud services, enabling data backup and syncing across many devices.
- It is a gadget that establishes the WLAN (Wireless Local Area Network) in huge companies.
- It is used to increase the network's coverage area so that it does not disconnect, allowing additional users to effortlessly connect to the network.
- An access point links a switching device, Ethernet cable, wire router, and Wi-Fi to identify a specific region.
- It is used to give connection to users in big offices or organizations, allowing them to wander freely within the office while remaining connected to a net.
- LANs may additionally be set up in public areas including coffee shops, eateries, and airports.
Advantages of WAP (Wireless Access Point)
- More User Access: Typically, the wireless router permits 10 - 20 people or gadgets to access the internet. While the WAP permits 50-100 people or devices to connect to the network. The WAP offers a stronger capacity to broadcast and receive signals, allowing for more usage.
- Broader Transmission Range: A wireless router's transmissions can reach up to half a dozen or 10-12 meters. Yet, an access point that is wireless has a range of more than 100 - 300 meters. The broad range is ideal for large cover offices and buildings for larger organizations. With a wireless access point, users may simply wander the network.
- Flexible Networking: Except in households, wireless networking frequently involves a large number of wireless devices and various networking patterns that are implemented according to the environment & requirements of commercial venues.
- Mobility: Users may move freely while remaining linked to the network.
Disadvantages of WAP (Wireless Access Point)
- Costly: Wireless Access Points (WAPs) can be costly due to the size of the company network. The number of WAPs required increases the cost. As a result, the corporate prioritizes cost containment, which causes many consumers to be hesitant to utilize WAP, instead opting for low-performance home routers.
- Poor stability: Because wireless networks employ air as a transmission channel, network stability and speed in WAP are lower than in cable networks, where cable is the transmission medium. Although WLAN has more devices, it is still sluggish, and a wired network is quicker and more reliable than a network that is wireless.
- Less secure: It is less secure than a wired network since the user transmits over radio waves, and anyone on that network, including a hacker, may sniff the content.
- Limited range: WAP's range is limited by a variety of variables, including physical barriers, interference from other wireless devices, or environmental conditions.
- Bandwidth limits: It can be influenced by bandwidth limits, resulting in decreased network speed and dependability.
- Wireless signals are hindered by many barriers like heavy rain, high walls, gates, storms, strong winds, enormous crowds of people, and so on. The signal strength is also determined by the place where the wireless internet connection is installed.
Conclusion
In conclusion, Wireless Access Points (WAP) can be used to offer network connection in workplaces, allowing workers to work from wherever in the workplace while remaining connected to the network. Furthermore, WAPs offer wireless Internet access in public areas such as coffee shops, airports, & train stations.