Body Area Network
Introduction
Nowadays, networking media are covered globally in several fields, including computer networking and health departments. The different types of n/ws that deal with monitoring and detecting the entire human body system are typically referred to as the body area network. Another name for it is the Body Sensor Network (BSN). The body area network (BAN), a technology that provides accessible, affordable healthcare globally, is covered in this article.

A body area network (BAN), also called a wireless body area network (WBAN), a body sensor network (BSN), or a medical body area network (MBAN), is a wireless network of wearable computing devices. BAN devices can be implanted into the body as pills or implants, surface-mounted on the body in a fixed position, or accompanied by devices that people can carry in different positions, like pockets of clothing, hands, or bags. Despite this trend, decimetre-sized (tab and pad) smart devices are a significant component of body area networks.
In addition to serving as data hubs or gateways, they offer a user interface for instantaneously viewing and managing BAN applications. Applying wireless personal area network (WPAN) technologies to implement communications on, near, and around the human body was the impetus for developing WBAN technology, which began in 1995. Six years later, systems where communication is entirely within, on, and near a human body began to be called "BAN" systems. WPAN wireless technologies can be used as gateways by a WBAN system to achieve greater ranges. The Internet can be accessed by wearable technology on the human body using gateway devices. This makes it possible for medical personnel to access patient data online via the Internet, regardless of the patient's location.
Applications
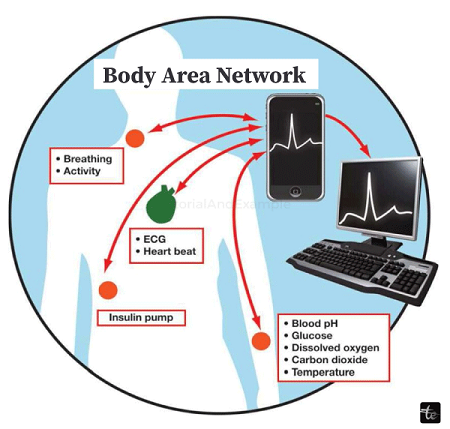
The healthcare industry is anticipated to be the primary area in which BANs are initially used, particularly for continuously monitoring and logging vital parameters of patients who suffer from chronic conditions like diabetes, asthma, and heart attacks.
- A BAN can notify the hospital even during a heart attack by monitoring changes in a patient's vital signs.
- When a diabetic patient's insulin level drops, a BAN could use a pump to administer insulin to them automatically.
- It is possible to use a BAN to understand the dynamics of a disease and its underlying health state transitions.
Security, sports, and the military are some more fields this technology uses. Expanding technology into new domains could facilitate a smooth information exchange between people or between people and machines.
Standard: IEEE 802.15.6 is the most recent international standard for BANs.
Parts of BAN(Body Area Network)
Vital sign monitoring sensors, motion detectors (using accelerometers to determine the monitored person's location), and a communication device to send vital signs and motion readings to carers or medical professionals are all necessary for a typical BAN or BSN. A transceiver, a processor, a battery, and some sensors make up a standard body area network kit. Developing physiological sensors, like SpO2 and ECG sensors, has been possible. Additional sensors are being developed, including an EEG sensor, a blood pressure sensor, and a PDA with a BSN interface.
An Abstract Idea
The swift development of physiological sensors, low-power integrated circuits, and wireless communication has made it possible to create a new breed of wireless sensor networks currently being utilised for traffic, infrastructure, health, and crop monitoring. Interdisciplinarity in body area networks may make it possible to monitor health in an affordable and ongoing manner while updating medical records in real-time via the Internet. Wearable wireless body area network uses include early medical condition detection and computer-assisted rehabilitation. These networks can be combined with a variety of intelligent physiological sensors. This field depends on the viability of comfortably inserted, minute biosensors that do not interfere with daily functions. The human body's implanted sensors will gather different physiological changes so that the patient's condition can be tracked wherever they are. A wireless data transmission will be made to an external processing unit. Doctors around the globe will receive real-time, instantaneous access to all information through this device. The doctors will promptly notify the patient if an emergency is identified through the computer system by sending the relevant alerts or messages. Currently, there are restrictions on the amount of information that can be provided and the energy resources that can run the sensors. Although the technology is still in its infancy, it is the subject of extensive research and, should it gain traction, could prove to be a game-changer in the healthcare industry, bringing ideas like telemedicine and MHealth to life.
Troubles
Issues arising from the utilisation of this technology might comprise:
- Data Quality: Data created and gathered via BANs can be critical throughout patient care. To guarantee that the decisions made are founded on the best information available, the quality of this data must be of the highest calibre.
- Data management: Since BANs produce vast amounts of data, managing and preserving these datasets is crucial.
- Sensor Validation: The inherent hardware and communication limitations of ubiquitous sensing devices, such as unstable wired and wireless network links, interference, and low power reserves, must be considered. This might lead to the transmission of inaccurate datasets back to the end user. All sensor readings must be validated, particularly in the healthcare industry. This lessens the likelihood of generating false alarms and helps spot potential flaws in the hardware and software architecture.
- Data Consistency: It is necessary to seamlessly gather and analyse data from wireless patient notes and various mobile devices. Important patient datasets in body area networks might be dispersed among several nodes and networked PCs or laptops. The quality of patient care may suffer if a physician's mobile device is not equipped with all available information.
- Security: Ensuring accurate and secure WBAN transmission would take significant work. It is necessary to ensure that patient secure data is isolated from other patient data and comes solely from their individual WBAN system. Secure and restricted access should also be provided to the WBAN-generated data. Not much research has been done on WBAN security despite most networks placing a high premium on it. It's possible that security solutions designed for other networks won't work on WBANs due to their limitations on power, memory, communication rate, and computational capacity. WBAN security requirements include data freshness, confidentiality, authentication, integrity, and availability, as well as safe management practices. In an attempt to offer security in WBAN, the IEEE 802.15.6 standard—the most recent one was created. It does, however, have a number of security issues.
- Interoperability: WBAN systems would have to facilitate smooth data transfer across Bluetooth, Zigbee, and other standards in order to encourage communication between devices and plug-and-play pairing. Additionally, the systems would need to provide constant connectivity, guarantee effective network migration, and be scalable.
- System components: WBAN would require its sensors to be easy to use, lightweight, compact, power-efficient, reconfigurable, and low in complexity. Furthermore, through the Internet, the storage devices must enable remote patient data viewing and storage and provide access to outside processing and analysis tools.
- Expense: Customers today want highly functional health monitoring systems at a low cost. To attract consumers who are concerned about their health, WBAN implementations must be affordable.
- Continuous monitoring: Different users may need varying degrees of monitoring. For instance, people who are at risk of cardiac ischemia might need their WBANs to be on all the time, while people who are at risk of falling might only need them to be on when they are walking or otherwise moving. The degree of monitoring affects the amount of energy needed and how long the BAN can last before running out of energy.
- Constrained deployment: The WBAN must be portable, light, and discreet. It shouldn't interfere with or change how the user goes about their everyday business. Ultimately, the technology ought to be transparent to the user—that is, it ought to carry out its monitoring functions without the user's awareness.
- Performance consistency: The WBAN ought to exhibit a consistent level of performance. Even after turning the WBAN on and off and back on again, sensor readings ought to be precise and calibrated. The wireless connections ought to be reliable and functional in various user settings.
- Energy vs. accuracy: The activation policy of the sensors should be chosen to maximise the trade-off between the power consumption of the BAN and the likelihood of misclassifying the patient's health status. More accurate assessments of the patient's condition are frequently the outcome of high-power consumption, and vice versa.
- Invasion of privacy: If WBAN applications extend beyond "secure" medical use, people may view the technology as a possible threat to their freedom. For this technology to be used more widely, social acceptance is essential.
- Interference: To minimise interference and promote the coexistence of sensor node devices with other network devices in the surrounding area, the wireless link used for body sensors should be used. This holds particular significance for the widespread adoption of WBAN systems.