Token Ring in Computer Networks
Overview of Token Ring
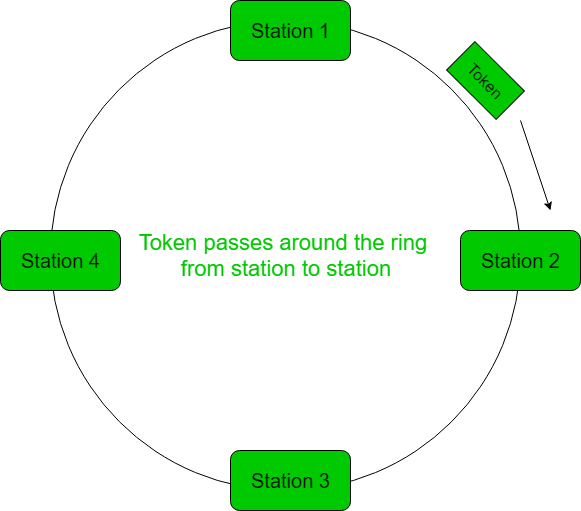
Token Ring is a LAN technology that features the ring topology of data transmission, which may be one-way direction or two-way flow. The token traverses the network in this setup, with the only entity allowed to send information owning the token. This makes sure that the necessary order to be maintained in data transmission takes place as well as makes it possible for the network to be deterministic and highly reliable by using this mechanism of token passing.
Characteristics of Token Ring
- Token Passing Mechanism: This implies that the token gives every device in the network a chance before passing it until every device is considered.
- Ring Topology Explained: The devices connect through a closed loop of physical or logical rings. This ring carries data from one point to another until it eventually reaches out to its intended destination.
- Unique Features: The token ring networks provide determinism that refers to that which is known in advance about how and when the data transmission will take place. Unlike Ethernet, a collision may result in unknown time delay periods.
Historical Context
One of the most used technologies was the token ring developed in the earlier eighties, taking on LAN supremacy with another emerging network, Ethernet. Firstly, in terms of being widely accepted, it was initially made famous by IBM since it possesses determinism, thereby being suitable in areas where a defined time signal is required for information transfer precision needs in specific applications or environments as in most cases.
Evolution of Token Ring
- IBM Influence: The token ring is one of the most robust products that IBM's Networking Architecture depended on and provided with deterministic performance.
- Industry Adoption: Initially, the Token Ring was popular and was adopted especially by many businesses. However, it encountered resistance with respect to adoption because of Ethernet.
- Legacy Systems: Even though it went down in history, the Token Ring had an enduring influence on certain legacies, which still rely on the structure.
Token at the Core of Computer Networks
Reliable Deterministic Performance
- Reliable and deterministic network performance is a critical strength of Token Ring in computer networks. On the other hand, the token-passing mechanic helps ensure that the data transmission process is systematic and deliberate.
- Hence, Token Ring provides a reliable and constant timing environment, thus applicable in any area where such is important to the application layer information delivery.
Reduced Collision Probability
- Contrary to Ethernet, which adopts a contention-based access approach and is prone to collisions, Token Ring greatly reduces the likelihood of collisions. The devices are said to share a common communication medium that is accessed in turn, and this one is called a 'token.'
- Having orderly access reduces the probability of data collisions, which makes for a stable and more effective network.
Applicability in Critical Systems
- The deterministic nature of the Token Ring is useful for critical situations, such as when precise timings and order of messages are needed. These include industries like the manufacturing sector, financial bodies, and health sector that require real-time communication and have therefore chosen token rings for their strict demands.
Legacy Systems and Compatibility
- Although Ethernet is now commonly used to replace Token Ring, this technology remains essential for some old systems. Although its relevance is declining, knowing about Token Ring is important for those who deal with old network infrastructures so that they can incorporate them into the current system without difficulties.
Fundamentals of Token Ring
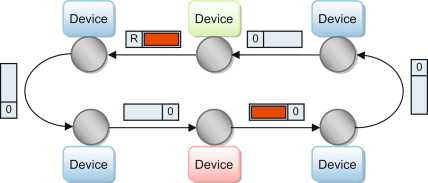
Token Passing Mechanism
- The orderly transmission of data from linked devices in the Token Ring networks is governed by a token-passing approach. A control frame that is known as a token circulates the network, permitting it to transmit to the device that currently holds the token. In turn, this deterministic method minimizes the chances of collision and guarantees streamlined data flow.
Ring Topology Explained
- In token ring networks, devices are connected in the form of the ring topology. For communication purposes, each device has only two neighboring devices. This one-way data flow over the ring is in accordance with the ordering of processes defined through the token-passing technique. This ensures network reliability and also makes it easy to identify and fix faults in ring topology.
Unique Features and Characteristics
Different factors have made token ring networks unique in computer networking. These include:
- Deterministic Performance: The token passing system allows a steady, definite performance that may be necessary in real-time, precisely timed applications.
- Reduced Collisions: The sequential data transmission feature ensures fewer incidences of data collision within a Token Ring network; hence, it is more stable.
- Addition/Removal Ease: This simplifies network management as additional devices can be added and removed in different parts of the network without disturbing everyone at once.
Token Ring Architecture
Token ring networks have good design comprised of critical elements that support their functionality:
MAU (Multistation Access Unit)
A Multistation Access Unit is the core of the Tokening Ring network. In a ring topology, it serves as a physical connection for several devices, which organizes them into a ring. The MAU is linked with every single device on the network, which makes it possible to send messages through the token-passing system.
Token
A special control frame called the Token is very important in Token Ring architectures. The device is allowed to transmit as it passes through the network. The passing of these tokens guarantees smoothness as well as avoiding clogging of the data transmission.
NIC (Network Interface Card)
Each node in the token ring network is equipped with a Network Interface Card (NIC). They are used in communicating between devices with which data can be exchanged. They are very important and follow the rule of "token passing."
Ring Topology
Ring topology is an architectural hallmark of Token Ring networks. The devices are lined up circularly with an orderly and linear way of passing through the token and the information. Ring-topology improves reliability, scalability, and fault tolerance.
Token Ring vs. Ethernet
The comparison between Ethernet and Token Ring brings out unique features that determine how they perform in different networking situations.
| Comparison Index | Token Ring | Ethernet |
| Network Topology | Ring topology wherein devices are interconnected in series forming a loop. Adopt a linear, sequential structure as it makes use of the token passing method. | It normally uses a star or bus (figure) topology, thus affording greater flexibility in physical arrangements. Uses Carrier Sense Multiple Access with Collision Detection (CSMA/CD) to control data delivery over its network. |
| Data Transmission | Ensures controlled and orderly data transmission by implementing a token-passing protocol. Ensures that only a device that has a valid token can send any data, avoiding collisions. | It uses CSMA / CD protocol with device sensing. Collision prone, especially at high traffic, which may interfere with the total network output. |
| Performance and Scalability | The traditional token passing made the performance more predictable because of its determinism. Suffers from a phenomenon known as scale effect which leads to performance degradation as the network reaches its maximum limit for the supported devices. | Modem Ethernet provides highly efficient Gigabits and 10 Gigabit Ethernet for ease of scaling. However, advancements have overtaken most of the historical limitations of the networks, though such performance could vary depending on load. |
| Reliability and Fault Tolerance | A ring-topology increases failure tolerance; where a single device is down, the network functions normally. This can, however, make troubleshooting and maintenance predictable. | Vulnerable to network interruptions due to cable damage or faulty device operation. It demands tough network management to make it reliable. |
Token Ring Network Operational Processes
Specific operational procedures are adopted for smooth data transmissions, error management, and recovery in token ring networks. These processes must be studied in order to protect the network's integrity.
Initialization
It is the initialization phase of a Token Ring network:
Ring Formation:
- Devices choose a logical starting point to create a ring topology.
- The generation of tokens for data transmission initializes the network.
Data Transmission
Efficient data transmission is a hallmark of Token Ring networks:
Token Passing:
- This token is circulating to give data transmission rights.
- Only the device holding the token must send data, thus keeping all things in order.
Error Handling and Recovery
Token Ring networks implement strategies for error management and recovery:
Error Detection:
- The constant monitoring reveals discrepancies in transmitted data or device malfunctions.
- These devices send an error message to the network, causing it to take immediate corrective action.
Error Recovery:
- It isolates faulty devices and data and does not disrupt the whole network.
- Recovery involves token reassignment and bypassing faulty stations.
Fault Tolerance
Ring Continuity:
- Ring topology increases tolerance; if a device fails, the network is still running.
- Changes are accommodated by the logical ring such that data flows continuously.
Recovery Measures:
- Redundancies and self-healing reduce time lost to failures in the network.
- They recover automatically and return to the network as normal.
Advantages of Token Ring Networks
Token Ring networks, with their unique characteristics, offer several advantages that make them suitable for specific environments:
Predictable Data Transmission
- Deterministic access into the network is achieved by token passing.
- Sending of data is in a predictable order by devices, thus minimizing contentions and collisions.
Controlled Access
- Token-based access control gives structure to data transmission.
- The token ensures that only devices with it can send their messages; hence, the chances for unauthorized transmission are eliminated.
Data Integrity
- By restricting access, it ensures that the transmitted data cannot be corrupted.
- This ensures that transmitted information is not tampered with by introducing enhanced security measures.
Sequential Data Flow
- All devices transmit data consecutively in compliance with what the token prescribes.
- It enhances the smooth flow of traffic, reducing chances for network congestion.
Low Collision Rates
- With token passing, data sharing becomes collision-free.
- Network efficiency is enhanced through reduced collisions.
Stable Network Behavior
- The performance of token ring networks is known to be stable and predictable.
- A reliable network environment comprises deterministic access and controlled transmission.
Ideal for Controlled Environments
- A token ring network is, therefore, suitable if deterministic access and low collisions are vital.
- The features of the Token Ring are useful in applications that need the transmission of a structured and organized data sequence.
Challenges and Limitations
Limited Scalability
- The scalability challenge may come with a growing number of token ring devices.
- Token passing in a network becomes an issue when one or multiple new devices are added, and these results in a lot of traffic, meaning a crowded or congested network.
Structured Topology Requirements
- Token ring network also needs an appropriate form of physical configuration (a ring) in order to work properly.
- This type of structured topology may require complicated management as well as being too limited.
Fault Isolation Challenges
- In practice, identifying faults/errors in a token ring is more difficult as compared to some other topology types.
- Depending on the design, it may involve troubleshooting and maintaining the network that needs special knowledge.
Single-Token Limitation
- Transmission of just one token per network ensures that different data packets are transmitted simultaneously.
- This limitation may also affect the overall bandwidth utilization in scenarios where fast data communication is vital.
Cost of Implementation
- For example, setting up a Token Ring network will be more costly than some other solutions at the start.
- Specialized hardware and structured cabling are very expensive; hence, they could be obstacles.
Complete Ring Failure
- Failure in a single device or part of the ring may lead to disruption of the whole network operations.
- Failures might occur, and as such, it may be necessary to adopt network redundancy measures.
Token Ring Maintenance and Troubleshooting
Cable Integrity Checks
- Ensure periodic monitoring, checks, and assessments at the strength of the real bodily cables constituting the ring.
- Ensure that each one faulty or damaged wires are replaced as quickly as viable.
Device Firmware Updates
- Regularly update the firmware of network gadgets in order that one will revel in a few enhancements or malicious program fixes in addition to more compatibility.
Use of Network Monitoring Tools
- Enhance network monitoring by deploying community monitoring structures and studying site visitors’ patterns.
- Identify anomalies by means of studying the community's fitness and overall performance.
Addressing Token Passing Issues
- Quickly investigate and resolve any problems related to the token moving mechanism.
- Make sure that tokens go with the flow properly within the network to avoid congestion in information transmission.
Ring Reconfiguration
- Provide instructions on a way to ring may be restored after a defective device or cable.
- State approaches on separating and bypassing the failed components of the internet without compromising its integrity.
Backup Token Management
- Create contingency plans on lower back-up tokens in times of breakdowns.
- Make sure that the network is flexible enough to modify without delay with out affecting records float.
Periodic Network Testing
- Perform common checks to measure the network's functionality and find weaknesses.
- Test the machine's capacity to face up to top loads by means of the usage of scenarios which have high visitors.
Simulation of Failure Scenarios
- Simulate device disasters or disconnect cables and check your community resilience on every event.
- Assess the manner the network responds to these simulated situations.
Documentation Practices
- Ensure that the configuration, layout, as well as maintenance records of the network are properly documented.
- Such a document is essential during troubleshooting and also an upgrade.
Token Ring in Contemporary Networking
Today, the significance of Token Ring technology continues to exist within contemporary networking for various specialized applications that are also being developed under current needs.
Explore its current significance:
Deterministic Communication
- Deterministic communications are appropriate for industrial applications of the Token Ring.
- The predictable nature of the token-passing mechanism makes it appropriate for environments with strict timing demands.
Security and Predictability
- The deterministic nature of the token ring makes it more secure against risks of collision.
- Therefore, it still makes sense in situations that favor more consistent data transmission over rapid, moving environments.
Legacy System Support
- This may apply to some of the legacy systems that can still use the Token Ring architecture.
- If there is a need for organizations with already established infrastructures to combine their systems, they can decide to include the Token Ring technology in order to conserve interoperability.
Redundancy Strategies
- In some scenarios, particularly when backup or redundancy solutions are necessary, Token Ring can function as alternative network architecture.
- This technology can work in synergy with other ones to facilitate constant running even during breakdowns.
Educational Purposes
- That is why the token ring is part of many networking coursework.
- In this connection, token ring scenarios can be useful in demonstrating the theories of networking to educators and educational institutions.
Research Applications
- However, Token Ring may be useful in certain research efforts designed to examine deterministic communication.
- Its unique features can be helpful for experimentation and specialized networking research.
Future Trends and the Legacy of the Token Ring
While Token Ring is no longer at the cutting edge of networking technology, it leaves a lasting legacy that may impact future developments in certain ways:
Considerations for Legacy
- Token Ring's historical significance in creating early networking ecosystems secures its legacy.
- Professionals in networking frequently appreciate its position as a forerunner to modern architecture.
Communication Standards that are Changing
- Influence of Deterministic Communication: Token Ring concepts such as deterministic communication may inspire future networking standards.
Elements of Token Ring may return as sectors want more dependable data transport.
Applications for Specific Markets
Specialized Industry Adoption
- Token Ring may continue to be deployed in niche businesses with special deterministic needs.
- Sectors that value dependable communication over high-speed data transfer may keep Token Ring relevant.
Hybrid Network Integration
- Hybrid Network Architectures: Token Ring could coexist with newer technologies in hybrid network architectures.
- Integrating Token Ring into hybrid configurations enables organizations to capitalize on their capabilities in specific contexts.
Use in Education
- Token Ring's incorporation into educational courses assures that its concepts are passed on to future networking specialists.
- Understanding its historical context leads to a well-rounded networking education.
Development and Research
- Token rings may be investigated in experimental networking topologies by researchers.
- Its deterministic nature could be investigated in order to improve knowledge and inspire new networking paradigms.
Efforts to Preserve
- Archival Importance: Token Ring documentation, protocols, and equipment may be saved for future reference.
- Museums and technology enthusiasts may keep Token Ring artifacts as part of networking history.
Conclusion
In Conclusion Token Ring, a once-dominant networking technology, has left an indelible mark on the evolution of computer networks. Token Ring's deterministic communication and ring topology provided essential concepts to the networking world while being overtaken by more scalable and adaptive alternatives such as Ethernet. Its historical value, educational relevance, and prospective uses in specialized settings all contribute to its long-term legacy. As networks evolve, Token Ring teachings continue to influence the design and understanding of current and future networking technologies. While Token Ring is no longer at the forefront, its effect lives on, reminding us of the fluid nature of technical innovation and the pivotal role it plays in creating network topologies.