Java Anon Proxy
The Java Anon Proxy (JAP), also known as JonDonym, is a proxy system designed to enable Web browsing with revocable (the use of or publication under a pseudonym, a false or fraudulent identity). Without this anonymity, each internet-connected device has a traceable address, such as:
- The provider of internet services.
- The websites that the device visits.
- Anyone using the internet network which is an eavesdropper.
If encryption is not used, it may be possible to determine which websites the user is browsing or the type of request being made on a specific system. However, because JAP uses a static address that is shared by other JAP users, neither an eavesdropper nor a site that is visited can learn what kinds of requests are being made by the user.
Java Anon Proxy:
The user does not connect directly to a requested site when Java Anon Proxy is used. In actuality, the user travels a long distance to reach the website. The lengthy route entails connecting with encryption through numerous middlemen, or "Mixes." The JAP employs a predetermined sequence for Mixes. The term "Mix Cascade" refers to a particular type of linked mix sequence. Users can select from a variety of mixed cascades. To implement the long route, the web browser must be configured so that data flows through the JAP first rather than straight to the requested site.
When a user launches the JAP software, it first establishes a connection with the InfoService to check that the programme version remains compatible. If the JAP software version is incompatible with the other software, the user is prompted to upgrade the application; otherwise, access to the JAP service is not possible. The JAP then registers with the specified mix cascade's first mix station. There is a continual network connection between the JAP programme and the initial mix station until logoff.
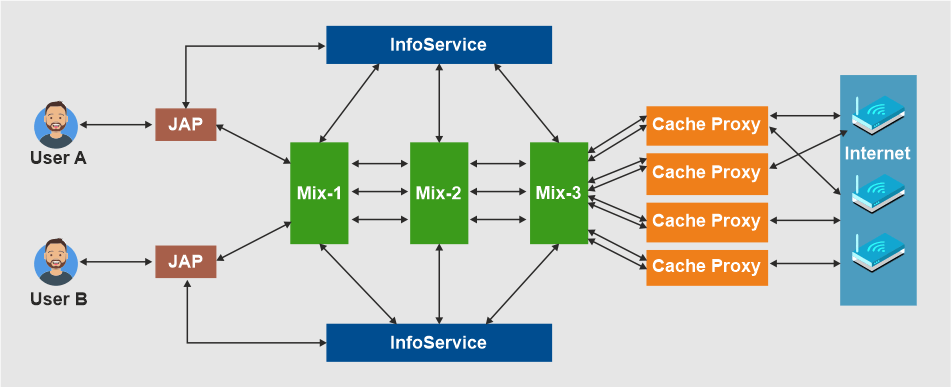
Encryption:
The JAP software first performs data encryption. The initial mix station receives the encrypted data next. The encrypted data is merged with that of other users at the first mix station before being delivered to the second mix station. As depicted in the picture above, the data is subsequently transported from the second mix station to the third mix, where it is decrypted before being relayed to the internet via the cache proxy. JAP employs powerful encryption between the client's machine and the other JAP servers. As was already mentioned, data is encrypted multiple times. Due to the numerous layers of encryption, it can be compared to an onion.
The data for the final mix in the mix cascade is protected by an encryption layer. Only the final mix has the power to remove this layer and access the data. For the second to last mix, additional encryption is placed around the already encrypted data. The third layer of encryption is applied in a similar way to the third-to-last mix.
Types of Encryptions:
Asymmetric cryptography is used by Java Anon Proxy to encrypt data, ensuring that only the right combination of keys can break each layer of encryption. The use of two keys distinguishes asymmetrical cryptographic processes: one secret key is used to decrypt encrypted data, and the other key, which is known to the public, is used to encrypt data. The secret key is the one that can only be used by the mix station where the encrypted data is to be decrypted. The two encryption techniques that the Java Anon Proxy employs are listed below.
- AES with a key length of 128 bits
- RSA with a key length of 1024 bits
For increased efficiency, the data is symmetrically encrypted with AES. The symmetric key is encrypted using the more time-consuming asymmetric RSA algorithm.
Advantages of encryption:
To achieve anonymization, encryption is crucial for two key reasons.
- To make sure that authentic mixes and not any snoopers or attackers are properly decrypting encrypted data.
- Data is more secure when encrypted at various layers because encrypted data has a unique appearance each time. As a result, it is very challenging for an attacker to draw a connection between an incoming and an outgoing message based solely on the appearance of the data.
Cons of Java Anon Proxy:
To allow for user anonymity, the following restrictions should be considered.
- A cascade's mix should never be under the attacker's control.
- The offender must never exert control over the other users. It's because the assailant is aware of the information coming from the others.
As a result, the additional data must originate with the actual user and not with the mix. As a result, an attacker can easily target the user.