How to Password Protect Files and Folders in Windows?
To ensure the security of your files and folders, it's a good idea to password-protect them, especially if you share your computer with others. Although Windows does not include a built-in feature for password-protecting files and folders, there are several third-party programs available that can be used for this purpose. It's important to note that the method for encrypting files and folders may vary depending on the version of Windows that is installed on your machine.

When you apply password-protect to a folder, it means that to access the files within the folder, you will need to enter the password you set up at the time of protecting the folder. Additionally, you can also use password-protect individual files or folders. The process for securing files and folders is the same.
It's a good practice to make a backup of your non-password-protected files and folders before password-protecting them in case you forget the password in the future. This way, you can still access your files even if you can't remember the password.
Microsoft Windows Vista, 7, 8, and 10
In order to password-protect files and folders in Windows Vista, Windows 7, Windows 8, and Windows 10, you will need to use a third-party software package.
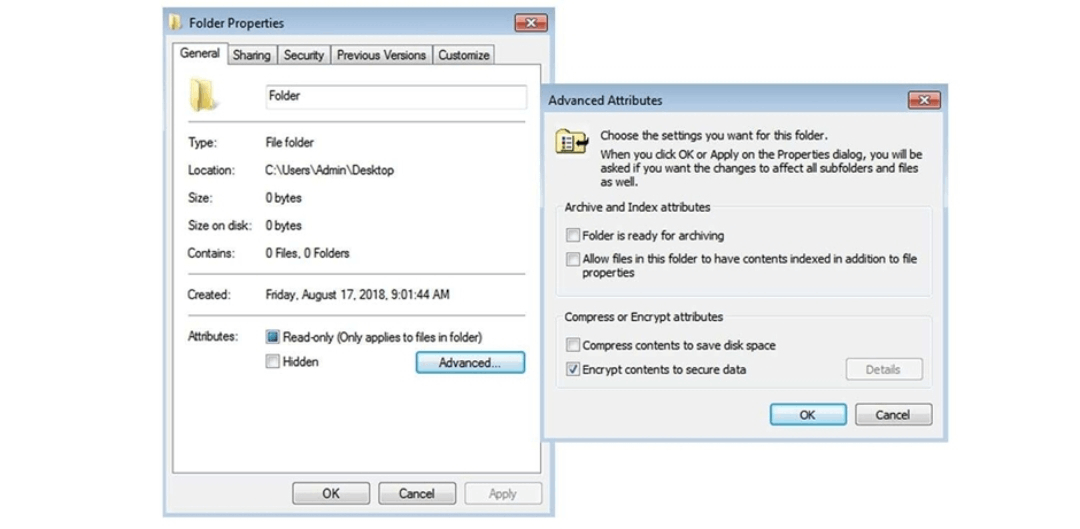
Here are the detailed steps you can follow:
- Choose or highlight the file or folder that you want to encrypt.
- Right-click on the file or folder you want to encrypt and choose Properties.
- Go to the General tab and click the Advanced button.
- In the Advanced Attributes window that appears, tick the box for "Encrypt contents to secure data" and then click OK.
- A pop-up window will appear asking if you want to encrypt the file or folder and all its subfolders and files. Click Yes to continue.
- You will then be prompted to back up your encryption certificate and key. This step is important as it is required to decrypt the files and folders in the future.
- Once the encryption process is complete, the file or folder will be designated with a blue color and a lock icon, indicating that it is now encrypted.
Note: If you do not see the "Encrypt contents to secure data" option, or this option isn't visible or selectable, you may have a Home Edition of Windows, which doesn't support this function. It is also possible that the hard disc needs to be formatted in the NTFS file system, which is required to encrypt files and folders.
Microsoft Windows XP Professional Users
Windows XP Professional users can password-protect files and folders using the built-in Encrypting File System (EFS). Here are the detailed steps you can follow:
- Choose or highlight the file or folder that you want to encrypt.
- Right-click on the file or folder you want to encrypt and choose Properties.
- Go to the Advanced button.
- In the Advanced Attributes window that appears, tick the box for "Encrypt contents to secure data" and then click OK.
- A pop-up window will appear asking if you want to encrypt the file or folder and all its subfolders and files. Click Yes to continue.
- You will then be prompted to back up your encryption certificate and key. This step is important as it is required to decrypt the files and folders in the future.
- Once the encryption process is complete, the file or folder will be designated with the green color and a lock icon, indicating that it is now encrypted.
Note: The Encrypting File System (EFS) is only available for the NTFS file system, so you need to format your hard drive with NTFS to use EFS. Also, it is important to backup your encryption certificate and key, otherwise, you won't be able to decrypt your files in the future.
Microsoft Windows XP Home Users
Encrypting files and folders on Microsoft Windows XP Home Edition is a way to protect sensitive information by making it unreadable to unauthorized users.
Here are the detailed steps to encrypt a file or folder on this operating system:
- Select the file or folder that you want to encrypt. This can be done by left-clicking on the file or folder and then holding down the "Ctrl" key while clicking on additional files or folders to select multiple items.
- Right-click on the selected file or folder and select "Properties" from the drop-down menu.
- In the Properties window, click on the "Sharing" tab.
- To make the folder private, check the box next to "Make this folder private."
- Click on the "Apply" button and then the "OK" button to save the changes.
There are some requirements that must be met for this option to work:
- The hard drive must be formatted in NTFS, not FAT32. This is because the encryption feature is not available on the FAT32 file system.
- The folder being encrypted must be within the user's personal folder (e.g. C:\Documents and Settings[username]).
- Encryption is not possible for folders outside of the personal folder.
If these requirements are not met, the option to "Make this folder private" will be grayed out and unable to be selected. In that case, you may consider other security solutions, such as third-party encryption software, to protect sensitive information on your computer.
Other Security Solutions for Protecting Your Files And Folders In Windows
There are several alternative security solutions for protecting files and folders on Windows XP Home Edition, including:
- Third-party encryption software: There are many encryption software programs available that can be used to encrypt files and folders on your computer. These programs typically use strong encryption algorithms, such as AES or RSA, to protect your data. Some popular encryption software options include VeraCrypt, AxCrypt, and 7-Zip.
- Password-protecting files and folders: You can use built-in Windows utilities or third-party software to password-protect files and folders. For example, you can use the compress feature in windows to create a password-protected archive of your files and folders.
- File and folder permissions: Windows XP allows you to set permissions on files and folders so that only certain users or groups can access them. This can be a useful way to restrict access to sensitive information.
- Cloud-based storage: You can store your files and folders on a cloud-based storage service, such as Google Drive, Dropbox, or Microsoft OneDrive. These services typically have built-in encryption and other security features to protect your data.
- External hard drive: You can store your files and folders on an external hard drive and disconnect it when not in use. This makes it difficult for hackers to access your data, but it is important to note that physical security should also be considered.
- Disabling the guest account: Windows XP has a built-in guest account that allows anyone to log in and access files and folders on your computer without a password. Disabling this account can help to prevent unauthorized access to your data.
It is important to note that no one method is completely foolproof, and it is recommended to use a combination of these solutions to ensure maximum protection for your files and folders.
Things To Remember When Encrypting or Password-Protecting Files and Folders
When encrypting or password-protecting files and folders, it is important to remember the following:
- Keep your encryption key and password safe: Your encryption key or password is the only way to access your encrypted files and folders. Make sure to keep it in a safe place, such as a password manager, and do not share it with anyone.
- Use strong encryption and password: It is important to use strong encryption algorithms and a strong password to protect your files and folders. Avoid using easily guessable or weak passwords, such as "123456" or "password".
- Remember to back up your files: Encrypting or password protecting files and folders can make them inaccessible if you forget your key or password. Make sure to back up your files and folders to an external drive or cloud storage before encrypting them.
- Be aware of the risk of social engineering: Be aware of the risk of social engineering attacks, in which an attacker may try to trick you into revealing your encryption key or password. Always be suspicious of unsolicited emails or phone calls, and never reveal your key or password to anyone.
- Update your software and operating system: It is important to keep your encryption software and operating system up-to-date to ensure that any security vulnerabilities are patched.
- Be aware of the legal regulations: It is important to be aware of any legal regulations or compliance requirements that may apply to your data. For example, certain industries have specific regulations regarding the encryption of sensitive data.
- Be aware of physical security: Encryption and passwords will protect your files and folders from unauthorized access, but it is also important to make sure that your computer and external devices are physically secure.
- Be aware of the cloud-based storage security: If you choose to store your files and folders on a cloud-based storage service, make sure to choose a reputable provider and check their security features.
- Have a plan for key or password loss: Have a plan in place for what to do if you lose your encryption key or password. This could include keeping a physical or digital copy of the key or password in a secure location or having a trusted individual hold a copy.
By keeping these things in mind, you can help to ensure that your files and folders remain secure and protected against unauthorized access.
Why Password-Protect Files?
Password-protecting files is important for maintaining the privacy and security of sensitive information. It helps prevent unauthorized access, accidental sharing, and human error. Additionally, it can protect against external threats such as hackers or data breaches. By adding a password to your files, you can ensure that only authorized individuals have access to the information, which can be especially important for businesses or organizations that handle sensitive data. Additionally, password-protecting files can also be useful for personal use, such as protecting personal documents, financial information, and other private information. Overall, password-protecting files is a simple and effective way to safeguard your information and keep it secure.
Difference Between Password Protected File and Encryption File
- Password protection refers to the use of a password to restrict access to a file or folder, while encryption refers to the process of converting data into a coded format that can only be accessed with a decryption key.
- Password-protected files can be easily unlocked by anyone with the correct password, while encryption requires a more complex process to decrypt the data.
- Password-protected files are typically less secure than encrypted files, as passwords can be easily guessed or stolen.
- Encryption uses mathematical algorithms to scramble data, making it much more difficult for unauthorized users to access the information.
- Password-protected files can be unlocked by simply entering the correct password, while encryption requires a decryption key to be entered in addition to the password.
- Encryption can be applied to individual files or to entire drives, while password protection is typically only applied to individual files or folders.
- Password-protected files can be easily copied or moved to other locations, while encryption requires the decryption key to be entered before the data can be accessed.
- Encryption can be used to protect data in transit, such as email or online transactions, while password protection is typically only used to protect data at rest.
- Encryption can be used to protect data in the cloud, while password protection is typically only used to protect data stored on local devices.
- Encryption can be used to protect sensitive information, such as financial data or personal information, while password protection is typically only used to protect less sensitive information.