What is a MAC Address?
MAC (Media Access Control) is a unique identifier assigned to network interface controllers for use as a network address in transmissions within a network part. Simply put, a MAC address is a hardware address that identifies a specific device on a network.
Every network device, whether a computer, a smartphone, or a printer, has a unique MAC address. This Address is typically represented as a series of six pairs of hexadecimal digits, separated by colons or hyphens. For example, a MAC address might look something like this: 00:1A:2B:3C:4D:5E.
Structure of MAC Address
"Institute of Electrical and Electronics Engineers" standardized the MAC address structure.
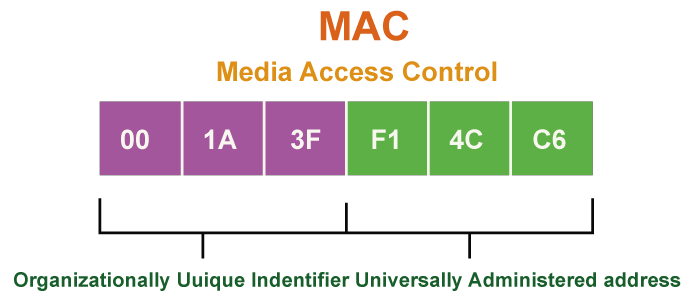
The MAC address is a 48-bit address, which means it comprises 6 bytes. Two hexadecimal digits represent each byte, separated by colons or hyphens. The first 3 bytes of the MAC address identify the manufacturer or vendor of the NIC, while the last three are unique to the device.
The 1st byte of the MAC address is known as the Organizationally Unique Identifier (OUI). This byte is assigned to a manufacturer or vendor by the IEEE. The OUI is followed by three bytes, which the manufacturer assigns to identify the specific NIC. These three bytes are called the Device ID.
The OUI can be used to identify the manufacturer or vendor of the NIC. The IEEE maintains a database of registered OUIs, which can be used to look up the manufacturer or vendor of a device based on its MAC address. This can be useful in regulating network issues or identifying unauthorized devices.
The three last bytes of the MAC address are known as the Interface ID. The Interface ID is unique to the device and is assigned by the manufacturer. The network uses the Interface ID to identify a specific device.
MAC addresses are used by network protocols such as Ethernet, Wi-Fi, and Bluetooth to identify devices on a network. When a device wants to communicate with any other devices on the network, it uses the MAC Address of the other device to address the packet. The network uses the MAC address to route the packet to the correct destination.
Unlike IP addresses, which can change depending on the network configuration, MAC addresses are assigned to factory devices and hardcoded into the device's hardware. This means that a device's MAC address remains the same no matter where it is connected to the network.
In summary, the structure of a MAC address consists of a 48-bit address comprising 6 bytes. The first three bytes identify the manufacturer or vendor of the NIC, while the last three are unique to the device. The IEEE assigns the OUI to identify the manufacturer or vendor. In contrast, the manufacturer assigns the Device and Interface ID to identify the specific NIC and device. Understanding the structure of MAC addresses can be useful in troubleshooting network issues and identifying unauthorized devices on a network.
When a device wants to connect with another device on a network, it uses the MAC Address to address the message. The process of sending a message between devices on a network using MAC addresses is known as MAC addressing. MAC address is used in the lower layers of the OSI (Open Systems Interconnection) model, specifically in the Data Link Layer. This layer transmits data over a physical link, such as a network cable or Wi-Fi connection.
To understand why MAC addresses are important, it is helpful to understand how they are used in practice. One common use of MAC addresses is in the process of MAC filtering, which restricts access to a network based on the MAC addresses of the devices allowed to connect.
For example, a company might configure their Wi-Fi network to only allow devices with specific MAC addresses to connect. This is often used with other security measures, such as WPA2 encryption, to help prevent unauthorized access to the network.
MAC addresses are also used in the ARP (Address Resolution Protocol) resolution process, which maps IP addresses to MAC addresses. When a device on a network wants to send data to another device, it first needs to get the MAC address of the terminal device. It does this by sending an ARP request to the network, which asks, "who has this IP address?" The device with the corresponding
MAC address then responds with its MAC address, and the original device can use this information to send the data directly to the destination device.
This process of ARP resolution is crucial for ensuring that network traffic is properly routed and reaches its intended destination. Without ARP, devices on a network would have to rely on inefficient and error-prone methods of routing data, such as broadcasting messages to all devices on the network and hoping that the intended recipient receives them.
Overall, ARP plays a vital role in enabling the smooth and efficient functioning of modern computer networks, and MAC addresses are a key component of this process.
Uses of MAC Address
Here are some of the crucial uses of MAC addresses:
- Addressing: In networking, addressing assigns a unique identifier to a device or network resource to enable communication between devices. The Internet Protocol (IP) addressing scheme is the most common network addressing scheme. Each device on a network is assigned a unique IP address, which is used to route traffic between devices. IP addresses are typically assigned dynamically through Dynamic Host Configuration Protocol (DHCP) or manually through static IP addressing.
- Switching: Switching refers to forwarding data packets between devices on a network. A network switch is a device that joins many devices on a network and dispatches data packets between them. Switches work at the data link layer of the OSI model and use MAC addresses to determine where to forward data packets. Switches are an important component of local area networks (LANs) as they provide a fast and efficient way to forward data packets between devices.
- Filtering: Filtering refers to selectively allowing or blocking traffic on a network based on certain criteria. For example, a network administrator may configure a firewall to block traffic from certain IP addresses or certain types of traffic, such as peer-to-peer file sharing. Filters can be applied at different levels of the network stack, including the network layer (IP filtering) and the transport layer (TCP/UDP filtering).
- Authentication: The process of proving the identity of a device/user on a network is called Authentication. This is typically done using a username and password or other credentials. Authentication is important for network security, as it helps ensure that only authorized/verified users and devices can access network resources. Several authentication mechanisms are available, including local Authentication, remote Authentication, and multi-factor Authentication.
- Troubleshooting: Troubleshooting refers to the process of identifying and resolving problems on a network. Common network issues include connectivity problems, slow performance, and security breaches. Network administrators use various tools and techniques to diagnose and resolve these issues, including network monitoring tools, packet sniffers, and log analysis. Troubleshooting is critical for network administrators as it helps ensure that the network functions properly and that downtime is minimized.
- Inventory Management: Inventory management tracks network resources, including devices, software, and licenses. This is important for network security and compliance, as well as for budgeting and planning purposes. Network administrators use tools such as asset management software to track and manage network resources.
In summary, MAC addresses are important for identifying devices on a network, controlling access, monitoring activity, managing resources, and mobile device management.
Different Methods to check your MAC Address
There are Different methods to check your MAC Address. The method to check for the MAC AddressAddress is different for every device. Many ways to check for MAC Addresses in Multiple Devices are written below:
Method 1: Using Command Prompt on Windows
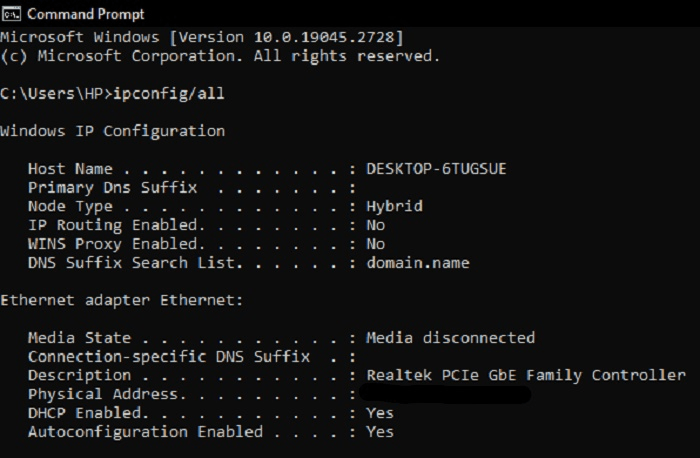
- Open the Command Prompt: Click the Windows Key + R on your keyboard, type cmd in the Run box, and press Enter.
- Type "ipconfig/all" and press Enter.
- Look for the "Physical Address" under the Ethernet adapter section. The Physical Address is your MAC address.
Method 2: Using Network Preferences on MacOS
- Click on the Apple icon on the top-left corner of your screen and click System Preferences.
- Click on the Network icon.
- Select the interface for which you want to find the MAC address (Ethernet or Wi-Fi).
- Press the Advanced button at the bottom right of the window.
- Click on the Hardware tab.
- Your MAC address will be given as the Ethernet Address or Wi-Fi Address.
Method 3: Using Settings on iOS Devices
- On your Apple Device, open the Settings Application
- Tap on General.
- Tap on About.
- Scroll down and find the Wi-Fi Address. This is your device's MAC address.
Method 4: Using Settings on Android Devices
- On Android, open Settings.
- Tap on About Phone.
- Tap on Status.
- Scroll down and check for the Wi-Fi MAC Address or Ethernet MAC address. This is your device's MAC address.
Method 5: Using Router Configuration Page
- Type your router's IP address in the address bar on your web browser.
- Log in to your router's configuration page with your username and password.
- Look for the MAC Address of the connected device in the DHCP client table.
Difference between Mac Address and IP Address
A Mac address (Media Access Control address) and an IP address (Internet Protocol address) are different types of addresses used in computer networks. While they are both used to identify network devices, there are some critical differences between them.
On the other hand, an IP address is a unique identifier assigned to a device on a network. It is a 32-bit numeric address that consists of four sets of numbers separated by ".", such as 192.168.0.1. IP addresses are used to specify devices on a network, but they are used for routing data across the internet. An IP address can be either static, meaning it is manually assigned to a device and remains the same, or dynamic, meaning it is given by a network's Dynamic Host Configuration Protocol (DHCP) server and can change over time.
One of the main differences between a Mac address and an IP address is its scope. A Mac address is used to identify devices on a local network, while an IP address is used to identify devices across the internet. This means a Mac address is not visible outside the local network, while any device can see an IP address online.
Another difference between Mac and IP addresses is how they are used. A Mac address ensures that data is transmitted to the correct device on a local network, while an IP address is used for routing data across the internet. IP addresses are also used for other network protocols, such as Domain Name System (DNS), which maps domain names to IP addresses.
In summary, while Mac and IP addresses are used to identify network devices, they have different scopes and purposes. Mac addresses identify devices on a local network, while IP addresses are used to identify devices across the internet. Mac addresses are hardwired into a device's hardware and cannot be changed, while IP addresses can be either static or dynamic.
| IP Address | MAC Address | |
| Purpose | An IP address is used to specify a device on a network. It is a logical addressing scheme, allowing devices to communicate with each other regardless of their physical location on the network. | MAC address determines a device on a Local Area Network (LAN). It is a physical addressing scheme and is used to help direct data packets to their intended destination. |
| Layer | An IP address is used at the Network layer of the OSI model, which is accountable for routing data packets across multiple networks. | MAC address is used at the Data Link layer of the OSI model, which is accountable for the reliable data transfer between directly connected devices. |
| Addressing | An IP address is a logical address given to a network interface by the Dynamic Host Configuration Protocol (DHCP) or a network administrator. It is used to identify the network location of a device. | MAC address is a unique identifier given by the manufacturer of a network interface card. It is used to identify the physical device on the network. |
| Assigned by | An IP address can be given by a network administrator or a DHCP server, which dynamically gives IP addresses to devices on the network. | MAC address is given by the manufacturer of the network interface card and cannot be changed. |
| Format | An IP address is a 32-bit or 128-bit number divided into four 8-bit numbers separated by periods (e.g. 192.168.1.1 for IPv4 and 2001:0db8:85a3:0000:0000:8a2e:0370:7334 for IPv6). | MAC address is a 48-bit number represented by six hexadecimal digits separated by colons (e.g. 01:23:45:67:89:AB). |
| Uniqueness | IP addresses are unique within a network but can be reused on different networks. | MAC addresses are unique to each device and are used to prevent data collisions on the LAN. |
| Location | IP addresses can be changed or reassigned by a network administrator or a DHCP server, leading to network conflicts or duplicate addresses. | The manufacturer assigns MAC addresses that cannot be changed, but a device can have multiple MAC addresses if it has multiple network interface cards. |
Types of MAC Address
There are three types of MAC addresses:
1) Universally Administered Address
A Universally Administered MAC Address (UAA) is a MAC address assigned by the manufacturer of the NIC. It is also known as a burned-in address (BIA) because it is programmed into the NIC during manufacturing and cannot be changed. The first three octets of a UAA identify the network adapter's manufacturer, while the last three octets are unique identifiers assigned by the manufacturer.
The IEEE allocates MAC addresses to manufacturers. They assign a block of MAC addresses to each manufacturer, which can then be used to assign a unique MAC address to each network adapter they produce.
The first three octets of a UAA are known as the Organizationally Unique Identifier (OUI). The OUI is assigned to the manufacturer by the IEEE and is used to identify the network adapter manufacturer. The device identifier the manufacturer assigns is the three last octets of the MAC address.
UAA is the most common type of MAC address used in computer networks. It is used in all Ethernet-based networks, including wired and wireless networks. The UAA uniquely identifies each network adapter on the network and ensures that data is sent to the correct device.
One of the advantages of using UAA is that it is globally unique. Since the MAC address is given by the manufacturer and managed by the IEEE, there is no chance of two devices having the same MAC address. This makes it easy for devices to communicate on the network without conflicts.
Another advantage of using UAA is that it is more secure than LAA. Since the manufacturer assigns UAA and cannot be changed, it is more difficult for an attacker to spoof the MAC address of a device on the network.
In conclusion, a Universally Administered MAC Address (UAA) is a globally unique MAC address assigned to a network adapter by the manufacturer. It is used to identify each network adapter and ensure that data is sent to the correct device. UAA is more secure than LAA because the manufacturer assigns it, and it cannot be changed. Using UAA ensures that devices can communicate on the network without any conflicts and that the network is secure from attackers trying to spoof the MAC address of a device on the network.
2) Locally Administered Address
A Locally Administered MAC Address (LAA) is a distinctive identifier assigned to a network interface controller (NIC) by a network administrator or user. Unlike a Universally Administered MAC Address (UAA), which is assigned by the manufacturer of the NIC and is globally unique, an LAA can be assigned by anyone and may not be globally unique.
LAA is useful when a network administrator wants to change the MAC address of a device for security or other reasons. For example, some Internet Service Providers (ISPs) use the MAC Address of a device to authenticate it on their network. If a user wants to use a different device on the network, they can change the new device's MAC address to match the old device's MAC address. This is done using an LAA, which allows the user to assign a MAC address that is locally unique and not globally unique.
Another use case for LAA is when a network administrator wants to assign a MAC address to a virtual network interface. Virtual network interfaces are software-based network interfaces that can be created on a device. They are commonly used in virtualization environments to allow multiple virtual machines to share a single physical network adapter. In this case, the network administrator can assign an LAA to the virtual network interface to ensure it has a unique MAC address.
However, using an LAA can also cause issues on a network. If two different devices on the same network have the same MAC address, it can cause network problems such as packet loss and other issues. For this reason, it is necessary to check that an LAA is not assigned to a device if it conflicts with another device on the same network.
In conclusion, a Locally Administered MAC Address (LAA) is a unique identifier posted to a NIC by a network administrator or user. It is useful when a network administrator wants to change the MAC address of a device for security or other reasons or when assigning a MAC address to a virtual network interface. However, using an LAA can also cause issues on a network if it conflicts with another device's MAC address.
3) Multicast MAC Address
In computer networking, multicasting is the process of sending a message to a group of destinations simultaneously. This differs from broadcasting, where a message is sent to all the hosts on the network. In multicasting, the message is only sent to the hosts that have subscribed to the multicast group. The Ethernet protocol uses a special MAC address called the multicast MAC address to enable multicasting.
A multicast MAC address is a special type of MAC address that addresses a group of network devices instead of a single device. It is used in multicast transmissions, where a single message is sent to a group of devices instead of to all devices on the network. Multicasting is commonly used in audio and video, online gaming, and other applications where data must be distributed to multiple recipients simultaneously.
A multicast MAC address comprises the first 24 bits set to a specific value and the last 24 bits set to a unique identifier. The specific value used in the first 24 bits is 01-00-5E in hexadecimal format. This value is reserved for multicast addresses by the Institute of Electrical and Electronics Engineers. The first 23 bits of this value are always the same, while the last bit is set to 0.
The last 24 bits of a multicast MAC address are used to identify the specific multicast group. The network administrator or the application developer assigns these bits. The network administrator can assign a range of multicast MAC addresses to be used by different applications. This ensures that different applications do not use the same multicast MAC address on the same network segment.
Multicast MAC addresses are used by the Internet Group Management Protocol (IGMP) to manage the membership of multicast groups. When a device wants to join a multicast group, it sends an IGMP membership report to the multicast router. The multicast router then sends the multicast traffic to all devices that have subscribed to the multicast group.
In conclusion, multicast MAC addresses are unique types of MAC addresses used to address a group of network devices instead of a single device. They are used in multicast transmissions, where a single message is sent to a group of devices instead of to all devices on the network. Multicast MAC addresses comprise a specific value in the first 24 bits and a unique identifier in the last 24 bits. They are used by the Internet Group Management Protocol (IGMP) to manage the membership of multicast groups.
Conclusion
In conclusion, a MAC address is a unique identifier the manufacturer assigns to a network interface controller (NIC). It is used to identify multiple devices on a Local Area Network (LAN) and is an essential network communication component. The MAC address is a 48-bit number represented by six pairs of hexadecimal digits separated by colons. While the IP address identifies a device on a network at the Network layer, the MAC address identifies a device on a LAN at the Data Link layer. Understanding the MAC address and its function is important in managing and troubleshooting network issues. Network administrators can identify and resolve network connectivity, security, and performance issues by examining the MAC address.