What is a router?
A router allows the user to connect multiple packet-switched networks or subnetworks. It ensures the delivery of the data packet to the IP addresses they are assigned. We can use the router to allow multiple systems to share the same network. They are mostly used to transfer the data among LAN and WAN.

There are several routers, but most routers pass data between LAN and WAN. A LAN is a group of systems restricted where the system is distributed in a small area. Geographical constraints bound them. LAN is preferred for the personal use of the network. In comparison, as the name suggests, WAN widens the network's area. It is a comparatively large network of systems. We can connect LANs that are spread over different locations using WAN. Large organizations mostly use it.
Working of a Router
A router is somewhat similar to the traffic lights that control traffic flow. The systems can be considered vehicles that are assigned to different destinations. Each vehicle can choose its path to reach its final destination. Similarly, the traffic lights ensure that the vehicle reaches move toward the destination without any chaos. Similarly, a router's job is to maintain an effective flow of data packets without causing any disruption.
To do so, the router has a list of all the possible paths taken by the data packets to reach the destination. The final destination of the data packet is provided in the header section of the packet. It is read by the router, which then uses it to determine the best-suited path to reach the desired location. Then the data packet is routed towards that particular path. This list is present in the form of an internal routing table.
Differentiate between A Router and A Modem
Usually, both the router and the modem are embedded in a single machine as they both are necessary to access the internet over multiple devices. But they both are quite different and have their role to perform in connecting various systems and the Internet.
The purpose of a router is to manage the flow of data packets between various networks. We can create the network with the help of using the router. It provides the pathway for transferring the data. In contrast, the function of the modem is to connect the network with the Internet.
The modem establishes the internet connection and converts the signal from the service provider into a digital signal. So that the connected device can understand it. It modulated the signal from the device to enable it to travel in the network and demodulate the signal coming from the network to the device. The role of the router is to control and direct the data flow within the network while the modem converts data into a format that is suitable for data transfer. A computer attached to a modem can use the Internet. At the same time, a router allows the computer to send the signal modulated by the modem to various devices that are present in the network.
Let's discuss a real-life situation: For Person A, who have a router but no modem, then Person A will only be able to establish a network between various devices and can transfer the data using that network only. The person won't be able to access the Internet. While Person B, who has a modem, but no router, will be able to access the Internet. It will allow only a single device to access the Internet. To access the Internet by using multiple devices. And Person C, who has both modem and router, will be able to access the Internet and allow multiple devices.
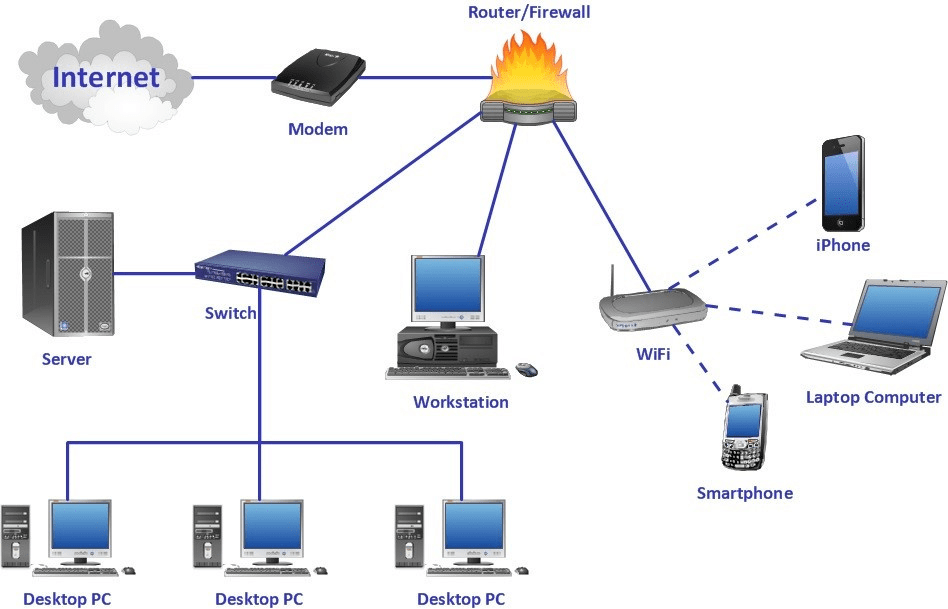
If you want to connect LAN and the Internet, a router needs to interact with the modem. This can be done using two methods:
- Wireless router: A wireless router is connected with a physical cable. The modem and router are connected using an Ethernet cable. They are not established using LANs; instead, the connection is established using a wireless local area network (WLANs). It transfers the data by changing the binary data into radio signals, and then these radio waves are transmitted using an antenna.
- Wired router: The wired router is connected using an Ethernet cable to the modem. Then the devices participating in the network are connected using separate wires. The local area network is established here, and each network device is linked to the Internet.
Types of Routers
They are different types of routers based on the function served by them. These are specialized routers that serve some specific purpose:
- Core Router: This is used by large organizations, as they enable the user to move a very high volume of data packets through the network. IT is efficient as it interacts with the core of the network while avoiding external networks.
- Edge Router: The core router is exclusively used for large networks while the edge counters are used for smaller networks. It is the opposite of the core counter as it lives at the very edge of the network. It interacts with both the core and the external network.
- Virtual Router: It is software that can perform all the functions performed by any hardware router.
Features of Routers
- A router is a component of the network layer that allows users to communicate with various devices in a network just by knowing the internet protocol address of the devices.
- The routers are connected to the devices using fast-Ethernet cables that provide better connectivity and high internet speed.
- The user can even configure the ports by using the requirement as needed by the network.
- They can be used to control the data traffic in the network, and they send the message only to the desired destination.
- They are essential for establishing large networks; they can be arranged so that the sub-networks are also intact networks.
- The router can create multiple paths between a single source and destination. Only one is the best route, while the rest are classified as alternatives routes.
- The routers
- Using routers enables the users to establish a single connection by combining several local and wide area networks.
- It ensures that there is no unnecessary interference in the network and there is no redundant transfer of data. The data can be protected by transferring as it can be encapsulated, preventing data loss.
- It ensures there is no conflict while transferring information to avoid such issues. They are assigned as masters and slaves.
Application of Routers
The routers play a crucial role in establishing computer networks. Some of the applications of routers are:
- Using routers, we can even connect hardware devices using remote networks.
- The transmission rate of data packets is relatively fast when routers are used. The links between routers and different components are established using a fast-Ethernet wire that is more efficient.
- They can establish both wireless and wired networks.
- The data can be transferred in e-mails, images, voice, and text messages.
- you can transfer the data among various systems just if we know the IP address assigned to the system; we wish to share data.
- Using routers, we can even limit access to the network. This can be done by allowing only a limited number of people who can access the data from the network. We can also restrict access to the level of information using the routers.
- They can be used to ensure proper working of wide-area network communication; by implementing routers, the executive can share the software tools available among various systems all connected by implementing WAN architecture.
- Routers can also be implemented along with the VPN in a wireless connection. This enables the user to set up the client-server model to request and share the information.
Routing Protocol
They are two types of Routing Protocol
- Static Routing Protocol
- Dynamic Routing Protocol
Static Protocols
They are static as assigning the path to the data packet is performed manually. This method provides more security to the network when determining the path from the source to the destination.
Advantages of using Static Routing Protocols:
- Addresses can be determined by the administrator only.
- There is no wastage of bandwidth between the various links.
- There is no additional overhead on the router.
Disadvantages of using Static Routing Protocols:
- The administrator needs to ensure that no router is left unconnected.
- It requires a lot of time and effort to manually assign the addresses.
- Even when a single link fails, the entire network goes down.
- It is not suitable for small networks.
Dynamic Protocols
In these protocols, adding information to the routing table is automated. Any modification in the network is sent as an update between various routers. These protocols are most used and highly important in establishing large networks.
Advantages of using Dynamic Protocols:
- Administrators can easily perform configurations.
- The data packets can be re-routed whenever a link goes down.
- We can balance the load among various links.
Disadvantages of using Dynamic Protocols:
- Since the modifications in the topology are sent to the routers, this consumes additional bandwidths.
- It puts an additional load on the router CPU.
- Internet Routing Protocol
- These protocols help the data packets to determine their path on the internet.
Routing Information Protocols
There are two different versions of the Routing Information Protocol. This protocol is implemented for both local and wide-area networks. This protocol is also implemented in the Application layer of the OSI model.
RIPv1 uses information like IP destination and hop count to determine the data packets' path.
RIPv2 is a more advanced version of the RIPv1 as it shares the routing table on a multicast address.
Distance Vector Routing Protocol (DVR)
It shares the routing table of the router to every connected after every specific time, but this uses a lot of bandwidth, and the coverage rate is quite low.
We need to perform updation if there is in the routing table whenever the router becomes unavailable.
Advantages of Distance Vector Routing Protocol:
- Updates are performed at regular intervals. The network updates are broadcasted whenever generated.
- It trusts the route provided by the neighbouring routers.
Disadvantages of Distance Vector Routing Protocol:
- These protocols waste a lot of bandwidth, and the traffic is unusually high.
Interior Gateway Protocol (IGP)
CISCO developed it to overcome the limitations faced by the RIP. It uses metrics to load bandwidth, delay, and increase reliability. The data is shared between the routers and the system using IGP.
The protocols perform broadcast every one minute and a half. That’s why this method is implemented over large networks. The updation in this protocol is automated, and there are 255 hop counts possible, making it most suited for configuring large networks. It also enables the user to distribute the load equally or unequally across various paths.
Link State Routing Protocol
This protocol is quite efficient as it computes the path followed to reach the destination against the cost of the resources to reach there using the path.
Working on Link State Routing Protocol
Three tables are created to implement the routing protocol. These are:
- Neighbour Table: This table records all the information about the other routers that are directly linked to the router.
- Topology Table: These tables handle the information about the network topology and the arrangement of the routers. It stores the information on paths from the source to the desired designation.
- Routing Table: It stores the best routes from the source to the designation.
Advantages of Link State Routing Protocol:
- There are separate tables to store the best routes and the alternative route for the same destination.
- This protocol has more information about the network between the routers and the system.
- It prevents unnecessary bandwidth usage, as, after any modifications, the updates are triggered automatically.
- It performs partial updates when there is any change in the network's topology, unlike other protocols where the entire routing table is changed even in the case of the slightest modifications.
Exterior Gateway Protocol (EGP)
This protocol allows the user to share the data between the gateway directly connected with the autonomous systems. It acts as a platform where different routers share information between various domains. This protocol constitutes the routers, addresses, the cost of travel, and the adjacent devices.
Enhanced Interior Gateway Routing Protocol (EIGRP)
This is a collection of multiple protocols. This single protocol provides routing protocols and link-state routing protocols. It is similar to IGRP as it also creates a composite metric to route the protocols. We can determine the best path to reach the destination using the composite metrics.
Open Shortest Path First (OSPF)
This protocol is a specially made IGP for internet protocol networks that are implemented using the shortest path approach. It constructs a database that records information about the structure of the network. It is a real-life implementation of the Dijkstra algorithm. It determines the network path each time after any change in the network topology. This protocol provides security to the network as it verifies the network, ensuring data security.
Border Gateway Protocol (BGP)
The function of this protocol is to notify the routing table of any change that occurs in the routes of the network. This protocol is not automated, and the change is to be manually reported by the user.
What is the purpose of implementing the Routing Protocols?
Routing protocols serve the following process during the transmission of data packets between the source and the destination:
- It helps in determining the best route for transmitting the information.
- It prevents loop routing of the data packet.
- It is faster to converge the data using the protocols.
- It reduces the data traffic on the network.
- It can be implemented to configure large networks.
- It adapts to the modifications made during the run-time.